

 The final phase of the WSIS+20 review has started. The two co-facilitators, Ambassador Suela Janina from Albania and Ambassador Ekitela Lokaale from Kenia, published on May, 21, 2025, their road map. The WSIS+20 Roadmap will lead us to the WSIS High-Level Meeting of the UN General Assembly (UNGA), scheduled for New York at the UN HQ on December 16-17, 2025. The first intergovernmental consultations were held on May 30, 2025, in New York. Two online stakeholder consultations followed on June 9 & 10, 2025. more
The final phase of the WSIS+20 review has started. The two co-facilitators, Ambassador Suela Janina from Albania and Ambassador Ekitela Lokaale from Kenia, published on May, 21, 2025, their road map. The WSIS+20 Roadmap will lead us to the WSIS High-Level Meeting of the UN General Assembly (UNGA), scheduled for New York at the UN HQ on December 16-17, 2025. The first intergovernmental consultations were held on May 30, 2025, in New York. Two online stakeholder consultations followed on June 9 & 10, 2025. more
 The future of the World Summit on the Information Society (WSIS) process will be one of the main topics of the 2025 Internet Governance Forum. Many in the IG community are heavily invested in the renewal of WSIS. They imply that if it is not renewed, there will be major, negative effects on the way we govern the Internet. IGP believes that it is healthy and productive for the community to consider the possibility of ending WSIS. more
The future of the World Summit on the Information Society (WSIS) process will be one of the main topics of the 2025 Internet Governance Forum. Many in the IG community are heavily invested in the renewal of WSIS. They imply that if it is not renewed, there will be major, negative effects on the way we govern the Internet. IGP believes that it is healthy and productive for the community to consider the possibility of ending WSIS. more
 Low-orbit space is growing increasingly crowded. Starlink has over 7,100 satellites in orbit and has plans to grow to 30,000. Project Kuiper has plans for a constellation of 3,232 satellites. One Web's first-generation constellation has 648 satellites, with plans to grow to over 6,300 satellites. The Thousand Sails (Qianfan) constellation is planning for up to 15,000 satellites. Numerous countries and businesses are launching or planning for smaller constellations for a wide variety of purposes.
Low-orbit space is growing increasingly crowded. Starlink has over 7,100 satellites in orbit and has plans to grow to 30,000. Project Kuiper has plans for a constellation of 3,232 satellites. One Web's first-generation constellation has 648 satellites, with plans to grow to over 6,300 satellites. The Thousand Sails (Qianfan) constellation is planning for up to 15,000 satellites. Numerous countries and businesses are launching or planning for smaller constellations for a wide variety of purposes.
more
 The ICANN Board's recent resolution to suspend an accountability safeguard hardcoded in its bylaws may represent the final straw that breaks the community's trust in ICANN. Most community members, including its own Board Chair, acknowledge that its current policy development and implementation processes are not working efficiently. However, the Board's decision to suspend the mechanism that could address these inefficiencies only seeks to preserve the status quo and the economic interests of these dominant market participants. more
The ICANN Board's recent resolution to suspend an accountability safeguard hardcoded in its bylaws may represent the final straw that breaks the community's trust in ICANN. Most community members, including its own Board Chair, acknowledge that its current policy development and implementation processes are not working efficiently. However, the Board's decision to suspend the mechanism that could address these inefficiencies only seeks to preserve the status quo and the economic interests of these dominant market participants. more
 We have just released the 2025 edition of the DOTZON study "Digital City Brands." Since first presenting the study in early 2017, DOTZON has now analyzed for the ninth consecutive year how cities successfully use their Digital City Brands. The Digital City Brand represents the digital aspect of a city's brand and reflects how digitally advanced a city is. The emergence of the Internet was the reason Digital City Brands were created in the first place. more
We have just released the 2025 edition of the DOTZON study "Digital City Brands." Since first presenting the study in early 2017, DOTZON has now analyzed for the ninth consecutive year how cities successfully use their Digital City Brands. The Digital City Brand represents the digital aspect of a city's brand and reflects how digitally advanced a city is. The emergence of the Internet was the reason Digital City Brands were created in the first place. more
 What happens when governments don't just regulate content, but forcibly repurpose the very guts of the Internet's infrastructure to enforce their policies? The chilling answer, increasingly evident worldwide, is widespread, devastating collateral damage. Around the world, neutral systems like Domain Name System (DNS) resolvers and IP routing, the bedrock of our digital lives, are being weaponized as enforcement tools. more
What happens when governments don't just regulate content, but forcibly repurpose the very guts of the Internet's infrastructure to enforce their policies? The chilling answer, increasingly evident worldwide, is widespread, devastating collateral damage. Around the world, neutral systems like Domain Name System (DNS) resolvers and IP routing, the bedrock of our digital lives, are being weaponized as enforcement tools. more
 Competition has been creeping into broadband pricing for the last several years as cable companies have been using low introductory rates to try to win new customers and offering similarly low prices to try to keep them. Anybody who competes against the big cable companies will tell you that cable companies have been competing for years by offering two-year promotional prices to keep customers. However, competition might have gone into a new gear recently... more
Competition has been creeping into broadband pricing for the last several years as cable companies have been using low introductory rates to try to win new customers and offering similarly low prices to try to keep them. Anybody who competes against the big cable companies will tell you that cable companies have been competing for years by offering two-year promotional prices to keep customers. However, competition might have gone into a new gear recently... more
 The NetBeacon Institute is pleased to publish its White Paper: Proposal for PDPs on DNS Abuse. We created this paper to support and advance ICANN Community discussions on potential policy development related to DNS Abuse. From our unique perspective, we believe there are a number of issues that are constrained enough to be a successful ICANN PDP and can make a meaningful difference in our collective work against DNS Abuse. more
The NetBeacon Institute is pleased to publish its White Paper: Proposal for PDPs on DNS Abuse. We created this paper to support and advance ICANN Community discussions on potential policy development related to DNS Abuse. From our unique perspective, we believe there are a number of issues that are constrained enough to be a successful ICANN PDP and can make a meaningful difference in our collective work against DNS Abuse. more
 On 17 May 1865, 20 European states convened to establish the International Telecommunication Union (ITU) to streamline the clunky process of sending telegraph messages across borders. 160 years later, ITU's anniversary is more than a mere commemorative moment; it is a stark reminder that multilateral cooperation is beneficial and necessary in our increasingly interconnected world. more
On 17 May 1865, 20 European states convened to establish the International Telecommunication Union (ITU) to streamline the clunky process of sending telegraph messages across borders. 160 years later, ITU's anniversary is more than a mere commemorative moment; it is a stark reminder that multilateral cooperation is beneficial and necessary in our increasingly interconnected world. more
 The ability to rank results according to the level of threat they pose (based on factors such as, for example, the extent to which a webpage relates to a brand of interest) is a key component of many brand protection services. The prioritisation process has a number of purposes, including the identification of: (a) priority targets for further analysis; (b) candidates for content tracking (i.e. regular reinspection of content or configuration, and the generation of an alert if high-concern findings are identified) - as may be appropriate in cases where a domain name presents a high potential level of risk but is not currently associated with any live site content; and (c) priority targets for enforcement actions. more
The ability to rank results according to the level of threat they pose (based on factors such as, for example, the extent to which a webpage relates to a brand of interest) is a key component of many brand protection services. The prioritisation process has a number of purposes, including the identification of: (a) priority targets for further analysis; (b) candidates for content tracking (i.e. regular reinspection of content or configuration, and the generation of an alert if high-concern findings are identified) - as may be appropriate in cases where a domain name presents a high potential level of risk but is not currently associated with any live site content; and (c) priority targets for enforcement actions. more
 The introduction of GDPR in 2018, and the subsequent tightening of privacy regulations around the world, was a necessary step toward protecting user data. Consumers gained critical rights over their personal information, and companies were forced to adopt stronger standards for how they collect, store, and use that data. However, one unintended consequence has been the erosion of access to domain registration information once easily available through WHOIS databases. more
The introduction of GDPR in 2018, and the subsequent tightening of privacy regulations around the world, was a necessary step toward protecting user data. Consumers gained critical rights over their personal information, and companies were forced to adopt stronger standards for how they collect, store, and use that data. However, one unintended consequence has been the erosion of access to domain registration information once easily available through WHOIS databases. more
 Negotiation processes in the UN are remembered not just for what came out of them, but also for what they were like, who participated, and how they were conducted. People who participated in the first World Summit on the Information Society (WSIS) back in 2003 and 2005 often talk about the process, its challenges and its achievements. more
Negotiation processes in the UN are remembered not just for what came out of them, but also for what they were like, who participated, and how they were conducted. People who participated in the first World Summit on the Information Society (WSIS) back in 2003 and 2005 often talk about the process, its challenges and its achievements. more
 Cyber criminals are the kings of recycling. Once they've found a tactic that works well, they'll keep doing it as long as they can get away with it. That's why it's so important for research teams to keep a close eye on what's happening behind the scenes with web traffic. Case in point? Our team at DNSFilter recently analyzed global DNS activity from the first quarter of 2025 and identified several notable trends. more
Cyber criminals are the kings of recycling. Once they've found a tactic that works well, they'll keep doing it as long as they can get away with it. That's why it's so important for research teams to keep a close eye on what's happening behind the scenes with web traffic. Case in point? Our team at DNSFilter recently analyzed global DNS activity from the first quarter of 2025 and identified several notable trends. more
 This past week offered a striking illustration of the pace and scale at which our shared orbital environment is evolving. In less than 24 hours, six rockets were launched from different parts of the globe, each contributing to the rapid expansion of low Earth orbit (LEO) infrastructure. China deployed a new set of Guowang satellites, while SpaceX launched two batches of Starlink satellites - one from Vandenberg in California and another from Cape Canaveral in Florida. United Launch Alliance (ULA) successfully placed Amazon's Kuiper satellites into orbit... more
This past week offered a striking illustration of the pace and scale at which our shared orbital environment is evolving. In less than 24 hours, six rockets were launched from different parts of the globe, each contributing to the rapid expansion of low Earth orbit (LEO) infrastructure. China deployed a new set of Guowang satellites, while SpaceX launched two batches of Starlink satellites - one from Vandenberg in California and another from Cape Canaveral in Florida. United Launch Alliance (ULA) successfully placed Amazon's Kuiper satellites into orbit... more
 Netscout recently released its latest Threat Intelligence Report that documents DDoS attacks in the second half of 2024. As has been the trend for many years, the largest target of DDoS attacks has been ISP networks. There were over 8.9 million DDoS attacks documented in the second half of last year, up 12.75% over the first half of the year. more
Netscout recently released its latest Threat Intelligence Report that documents DDoS attacks in the second half of 2024. As has been the trend for many years, the largest target of DDoS attacks has been ISP networks. There were over 8.9 million DDoS attacks documented in the second half of last year, up 12.75% over the first half of the year. more
 After several delays due to bad weather, Amazon's Project Kuiper finally launched its first batch of low-orbit broadband satellites on April 28. The company says it is in communication with all 27 new satellites. Amazon used a United Launch Alliance (ULA) Atlas V rocket launched from Cape Canaveral. Amazon is under pressure to get the launches going and has a commitment to the FCC to launch 1,618 satellites by July 2026. more
After several delays due to bad weather, Amazon's Project Kuiper finally launched its first batch of low-orbit broadband satellites on April 28. The company says it is in communication with all 27 new satellites. Amazon used a United Launch Alliance (ULA) Atlas V rocket launched from Cape Canaveral. Amazon is under pressure to get the launches going and has a commitment to the FCC to launch 1,618 satellites by July 2026. more
 The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light! more
The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light! more
 The debate surrounding digital sovereignty has gained momentum in recent years, particularly within BRICS nations, where governments seek to assert greater control over their digital ecosystems. Proponents of digital sovereignty often frame it as a necessary countermeasure against foreign technological dominance, positioning it as either a "positive" force- fostering local innovation and self-reliance- or a "negative" one- fueling authoritarian control and economic isolation. more
The debate surrounding digital sovereignty has gained momentum in recent years, particularly within BRICS nations, where governments seek to assert greater control over their digital ecosystems. Proponents of digital sovereignty often frame it as a necessary countermeasure against foreign technological dominance, positioning it as either a "positive" force- fostering local innovation and self-reliance- or a "negative" one- fueling authoritarian control and economic isolation. more
 The World Summit on Information Society (WSIS) convened by World leaders in 2003 and 2005 following the realization of the crucial roles of Information and Communications Technologies (ICTs) (also known in the industry as the Internet) played in economic growth and development. Since 2005, ICTs have added more than $10tr to the global economy (Oxford Economics, 2020). more
The World Summit on Information Society (WSIS) convened by World leaders in 2003 and 2005 following the realization of the crucial roles of Information and Communications Technologies (ICTs) (also known in the industry as the Internet) played in economic growth and development. Since 2005, ICTs have added more than $10tr to the global economy (Oxford Economics, 2020). more
 Tech developments saw less drama than trade and environmental shifts during Trump's first 100 days. Continuity, not abrupt change, defined his approach to AI and digital regulation. Only 9 of 139 executive orders (EOs) focused on tech. Trump's tech policy emphasised reviews and incremental shifts. Public consultations on AI, cybersecurity, and cryptocurrencies signal steady evolution over upheaval. more
Tech developments saw less drama than trade and environmental shifts during Trump's first 100 days. Continuity, not abrupt change, defined his approach to AI and digital regulation. Only 9 of 139 executive orders (EOs) focused on tech. Trump's tech policy emphasised reviews and incremental shifts. Public consultations on AI, cybersecurity, and cryptocurrencies signal steady evolution over upheaval. more
 Smuggled Phone Reveals North Korea’s Regime Captures User Screens Every Five Minutes, Censors Texting
Smuggled Phone Reveals North Korea’s Regime Captures User Screens Every Five Minutes, Censors Texting
 America’s Broadband Blind Spot: Audit Reveals Millions More Offline Than FCC Reports
America’s Broadband Blind Spot: Audit Reveals Millions More Offline Than FCC Reports
 Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats
Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats
 Massive Iberian Power Outage Raises Cybersecurity Questions
Massive Iberian Power Outage Raises Cybersecurity Questions
 Africa’s Digital Darkness: Internet Shutdowns Reach Record High
Africa’s Digital Darkness: Internet Shutdowns Reach Record High
 Massive Cyber Assault on X: Musk Hints at Foreign Involvement
Massive Cyber Assault on X: Musk Hints at Foreign Involvement
 Lack of Broadband Competition Leads to Higher Prices in Most U.S. Counties
Lack of Broadband Competition Leads to Higher Prices in Most U.S. Counties
 Meta’s Undersea Ambitions: A Cable to Power the AI Future
Meta’s Undersea Ambitions: A Cable to Power the AI Future
 India Launches ‘.bank.in’ and ‘.fin.in’ Domains to Deter Financial Fraud
India Launches ‘.bank.in’ and ‘.fin.in’ Domains to Deter Financial Fraud
 Baltic Sea Infrastructure Targeted Amid Rising Geopolitical Tensions
Baltic Sea Infrastructure Targeted Amid Rising Geopolitical Tensions
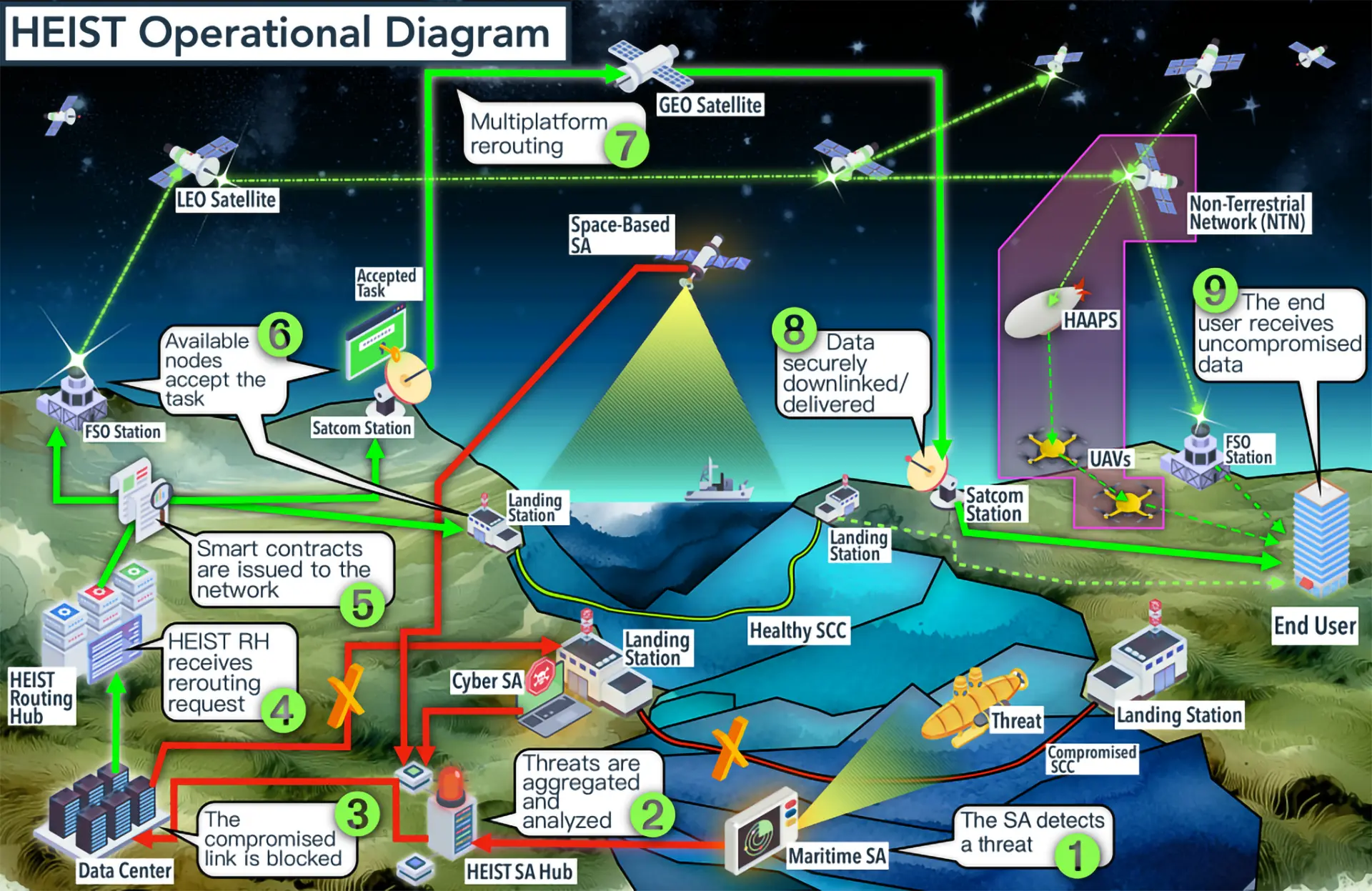 NATO’s Orbital Lifeline: A Backup Plan for the Internet
NATO’s Orbital Lifeline: A Backup Plan for the Internet
 Europe Seeks Space Independence with €10.6bn Iris² Satellite Network
Europe Seeks Space Independence with €10.6bn Iris² Satellite Network
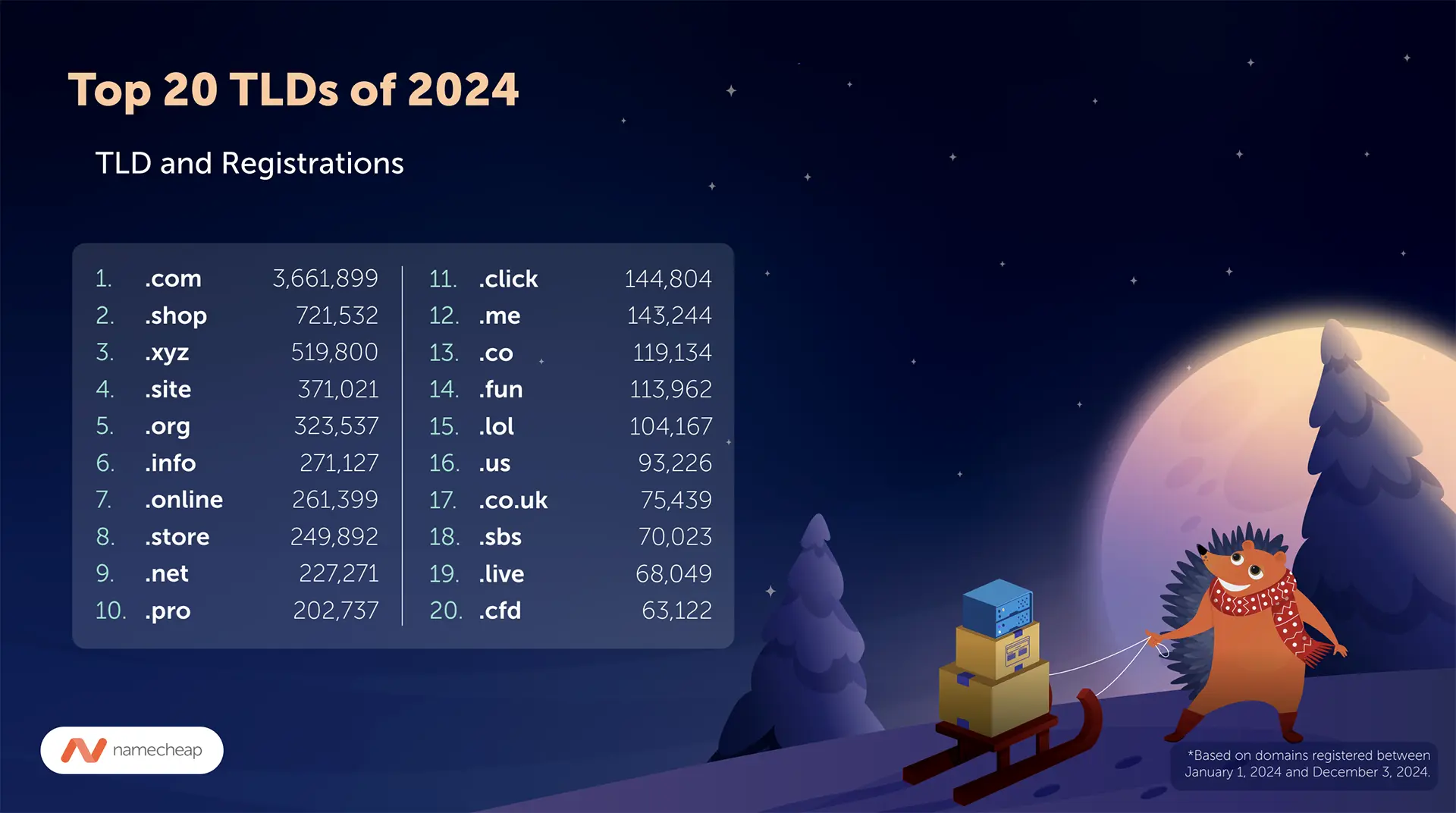 Domain Trends Signal Shifting Tides in 2024
Domain Trends Signal Shifting Tides in 2024
 Chinese Hackers Exploit U.S. Telecom Systems, Eviction Efforts Lag
Chinese Hackers Exploit U.S. Telecom Systems, Eviction Efforts Lag
 Meta’s $10 Billion Plan to Build the World’s Largest Subsea Cable Network
Meta’s $10 Billion Plan to Build the World’s Largest Subsea Cable Network
Sponsored byCSC

Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byDNIB.com

Sponsored byVerisign

 Adoption of new short and new long TLDs shows strong momentum, while IDN email compatibility continues to evolve across platforms. more
Adoption of new short and new long TLDs shows strong momentum, while IDN email compatibility continues to evolve across platforms. more
 The market for IPv4 addresses continues to experience deflationary pressures, with recent data showing a steady decline in prices across all block sizes. According to May 2025 figures from IPv4.Global by Hilco Streambank, average prices per address have been trending downward for nearly a year, with large blocks - particularly /16s - leading the descent. more
The market for IPv4 addresses continues to experience deflationary pressures, with recent data showing a steady decline in prices across all block sizes. According to May 2025 figures from IPv4.Global by Hilco Streambank, average prices per address have been trending downward for nearly a year, with large blocks - particularly /16s - leading the descent. more
 The MITRE Corporation updates its list of groups on the ATT&CK page every six months, specifically in April and October each year. The Updates - April 2025 advisory listed seven new groups with corresponding lists of indicators of compromise (IoCs) listed in the References section. Take a look at specific IoC-related details for each group below. more
The MITRE Corporation updates its list of groups on the ATT&CK page every six months, specifically in April and October each year. The Updates - April 2025 advisory listed seven new groups with corresponding lists of indicators of compromise (IoCs) listed in the References section. Take a look at specific IoC-related details for each group below. more
 The SideWinder advanced persistent threat (APT) group, active since 2012 and known for targeting government, military, and business entities throughout Asia, primarily Pakistan, China, Nepal, and Afghanistan, has struck once again. This time around, the threat actors updated their toolset and created new infrastructure to spread malware and control compromised systems. more
The SideWinder advanced persistent threat (APT) group, active since 2012 and known for targeting government, military, and business entities throughout Asia, primarily Pakistan, China, Nepal, and Afghanistan, has struck once again. This time around, the threat actors updated their toolset and created new infrastructure to spread malware and control compromised systems. more
 Based on our Q1 2025 ranking of the most popular gTLDs and ccTLDs, the same players pretty much made the list. The .com gTLD remained in first place while the other gTLD extensions like .xyz, .top, and .shop lagged far behind. Among the ccTLDs, only .de made it to the top 10. more
Based on our Q1 2025 ranking of the most popular gTLDs and ccTLDs, the same players pretty much made the list. The .com gTLD remained in first place while the other gTLD extensions like .xyz, .top, and .shop lagged far behind. Among the ccTLDs, only .de made it to the top 10. more
 Attaxion, the external attack surface management (EASM) vendor with industry-leading asset coverage, announces the integration of the European Vulnerability Database (EUVD) into its platform. more
Attaxion, the external attack surface management (EASM) vendor with industry-leading asset coverage, announces the integration of the European Vulnerability Database (EUVD) into its platform. more
 HUMAN's Satori Threat Intelligence and Research Team recently uncovered and partially disrupted BADBOX 2.0 in collaboration with Google, Trend Micro, Shadowserver, and other partners. The threat has been dubbed "the largest botnet of infected connected TV (CTV) devices" uncovered to date. more
HUMAN's Satori Threat Intelligence and Research Team recently uncovered and partially disrupted BADBOX 2.0 in collaboration with Google, Trend Micro, Shadowserver, and other partners. The threat has been dubbed "the largest botnet of infected connected TV (CTV) devices" uncovered to date. more
 Cisco Talos recently uncovered multiple Lotus Blossom cyber espionage campaigns targeting government, manufacturing, telecommunications, and media organizations. The group used Sagerunex and other hacking tools after compromising target networks. more
Cisco Talos recently uncovered multiple Lotus Blossom cyber espionage campaigns targeting government, manufacturing, telecommunications, and media organizations. The group used Sagerunex and other hacking tools after compromising target networks. more
 Choosing an attack surface management or a vulnerability management platform often comes down to identifying which tool provides the right mix of visibility, automation, and precision that matches your team's needs, ideally at as low a price as possible. more
Choosing an attack surface management or a vulnerability management platform often comes down to identifying which tool provides the right mix of visibility, automation, and precision that matches your team's needs, ideally at as low a price as possible. more
 Symantec recently reported that a China-based threat actor who has been involved in installing backdoors in the systems of target government institutions (i.e., cyber espionage) has turned toward spreading RA World ransomware (i.e., a cybercriminal act) this time. Going from one act to the other is not usual for attackers. more
Symantec recently reported that a China-based threat actor who has been involved in installing backdoors in the systems of target government institutions (i.e., cyber espionage) has turned toward spreading RA World ransomware (i.e., a cybercriminal act) this time. Going from one act to the other is not usual for attackers. more
What is a Dedicated IP VPN? A Dedicated IP VPN is a Virtual Private Network (VPN) service that provides users with a unique, static IP address assigned exclusively to them. Unlike a shared IP address, which is used by multiple users simultaneously, a dedicated IP is reserved for a single user, offering greater control and security over their online activities. more
Starlink provides high-speed, low-latency satellite internet, making it ideal for rural and remote areas lacking traditional broadband. Installation is user-friendly, and coverage continues to expand globally. However, the service is relatively expensive, and performance can be impacted by adverse weather. Overall, Starlink is a reliable choice for those without access to conventional internet options. more
ISPs can see that you are using a VPN, as they can detect encrypted traffic and the IP address of the VPN server. However, they cannot see the content of your data or the websites you visit while the VPN is active because the data is encrypted. This provides privacy for your online activities, though the fact that you're using a VPN itself is visible to the ISP. more
Satellite internet is a broadband service that connects users via signals transmitted between orbiting satellites and a satellite dish at the user's location. Unlike fiber or cable, it doesn't require physical infrastructure, making it essential in rural and remote areas. Although historically slower with higher latency, advancements like Low Earth Orbit (LEO) satellites have improved speed and reduced delays, enhancing overall performance. more
Yes, NordVPN still works with Netflix in 2024. It effectively bypasses geo-restrictions, unlocking libraries from major regions like the U.S., UK, Japan, and more. However, occasional issues like blocked servers or slow connections may arise. Troubleshooting, such as switching servers or using SmartPlay, typically resolves problems and maintains reliable access to Netflix. more
NordVPN offers two ways to try the service risk-free: a 7-day free trial for Android users and a 30-day money-back guarantee for all users. Both options allow full access to NordVPN's premium features. The trial requires payment details but can be canceled before charges occur. NordVPN provides superior security, performance, and global content access compared to free alternatives. more
NordVPN stands out for its unique double encryption, adding an extra layer of privacy. With blazing-fast servers in 60 countries, it's perfect for streaming, gaming, and bypassing geo-blocks. Its strict no-logs policy and advanced features like CyberSec ad-blocker make it a top choice for anyone seeking strong security and seamless performance. more
The best countries for VPN server locations include Switzerland, Iceland, and Panama for privacy, Germany, Japan, and the United States for fast connections, and the U.S., U.K., and Canada for streaming. These countries offer strong privacy laws, advanced infrastructure, and optimal performance for various online activities. more
VPNs are critical for remote work because they secure data by encrypting internet connections, protecting sensitive company information from cyberattacks. They also enable remote access to company networks, ensuring employees can work safely from any location while maintaining privacy and compliance with security policies. more
A VPN protects you by encrypting your internet connection, hiding your IP address, and routing your data through a secure server. This shields your online activities from hackers, trackers, and surveillance, ensuring privacy and security, especially on public Wi-Fi or when accessing sensitive information. more