

DNS |
Sponsored by |

|
 ICANN's proposed overhaul of root server governance would empower a new council to revoke America's operator status, risking a clash with a resurgent Trump administration and potentially imperiling the multistakeholder model that underpins the internet's core infrastructure.
ICANN's proposed overhaul of root server governance would empower a new council to revoke America's operator status, risking a clash with a resurgent Trump administration and potentially imperiling the multistakeholder model that underpins the internet's core infrastructure.
 Project Jake invites global DNS stakeholders to test JADDAR, a privacy-respecting framework for secure access to registration data, aiming to reduce regulatory fragmentation and modernise domain governance through collaborative, policy-aligned engineering solutions.
Project Jake invites global DNS stakeholders to test JADDAR, a privacy-respecting framework for secure access to registration data, aiming to reduce regulatory fragmentation and modernise domain governance through collaborative, policy-aligned engineering solutions.
 A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
 Meltnet envisions a federated internet model led by BRICS nations, combining digital sovereignty with cross-border interoperability. It challenges US-centric governance by proposing a trust-based architecture rooted in shared standards and mutual recognition.
Meltnet envisions a federated internet model led by BRICS nations, combining digital sovereignty with cross-border interoperability. It challenges US-centric governance by proposing a trust-based architecture rooted in shared standards and mutual recognition.
 DNSSEC promised to secure DNS with cryptographic proof, yet messy rollouts, outages, and hype backlash ruined its reputation. This piece argues that storytelling and emotions shape adoption as much as specs, and that automation enables a reset.
DNSSEC promised to secure DNS with cryptographic proof, yet messy rollouts, outages, and hype backlash ruined its reputation. This piece argues that storytelling and emotions shape adoption as much as specs, and that automation enables a reset.
 ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
ICANN invites proposals for its DNSSEC and Security Workshop at the ICANN85 Community Forum in March 2026, offering a platform for global experts to share insights on DNS, routing security, and emerging threats.
 Internet governance is shifting from participatory forums to security-driven mandates. As authority accelerates ahead of legitimacy, technical systems face growing instability and operators absorb the risks of politically motivated control.
Internet governance is shifting from participatory forums to security-driven mandates. As authority accelerates ahead of legitimacy, technical systems face growing instability and operators absorb the risks of politically motivated control.
 As Internet governance fragments in 2026, authority shifts from open, multistakeholder forums to state-led security regimes, legal instruments, and alliance-based cooperation, challenging longstanding institutions and reshaping global norms through enforcement rather than consensus.
As Internet governance fragments in 2026, authority shifts from open, multistakeholder forums to state-led security regimes, legal instruments, and alliance-based cooperation, challenging longstanding institutions and reshaping global norms through enforcement rather than consensus.
 ICANN is finalising a policy to curb DNS abuse, aiming to preserve internet stability while defending freedom of expression. With regulatory pressure mounting, the multistakeholder model faces a critical test.
ICANN is finalising a policy to curb DNS abuse, aiming to preserve internet stability while defending freedom of expression. With regulatory pressure mounting, the multistakeholder model faces a critical test.
 Grenada advances its digital resilience by signing the Convention on the Packet Clearing House Organization, positioning itself to help shape global Internet governance while gaining coordinated support, stronger infrastructure, and a formal voice in decisions that influence worldwide connectivity and security.
Grenada advances its digital resilience by signing the Convention on the Packet Clearing House Organization, positioning itself to help shape global Internet governance while gaining coordinated support, stronger infrastructure, and a formal voice in decisions that influence worldwide connectivity and security.
 To prepare DNS security for a post-quantum future, Verisign and partners are testing new cryptographic strategies that balance security, performance, and feasibility, especially through the novel Merkle Tree Ladder mode for managing large signatures.
To prepare DNS security for a post-quantum future, Verisign and partners are testing new cryptographic strategies that balance security, performance, and feasibility, especially through the novel Merkle Tree Ladder mode for managing large signatures.
 eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
 As ICANN prepares to expand the domain name space, calls grow for a public-law framework to govern the DNS root, ensuring global equity, transparency, and accountability in managing the Internet's core infrastructure.
As ICANN prepares to expand the domain name space, calls grow for a public-law framework to govern the DNS root, ensuring global equity, transparency, and accountability in managing the Internet's core infrastructure.
 The arrangements regarding the composition and organisation of the provision and operation of authoritative root servers are one of the more long-lasting aspects of the public Internet. In the late 1980s, Jon Postel, as the IANA, worked with a small set of interested organisations to provide this service. It was informally arranged, without contracts and without payment of any form.
The arrangements regarding the composition and organisation of the provision and operation of authoritative root servers are one of the more long-lasting aspects of the public Internet. In the late 1980s, Jon Postel, as the IANA, worked with a small set of interested organisations to provide this service. It was informally arranged, without contracts and without payment of any form.
 The international community has long struggled with the challenge of translating international law into actionable norms and practices in cyberspace. The conclusion of the United Nations Open-Ended Working Group (OEWG) on the security of and in the use of information and communications technologies 2021-2025 marks a vital milestone in that ongoing process.
The international community has long struggled with the challenge of translating international law into actionable norms and practices in cyberspace. The conclusion of the United Nations Open-Ended Working Group (OEWG) on the security of and in the use of information and communications technologies 2021-2025 marks a vital milestone in that ongoing process.
 Massive AWS Outage Disrupts Global Internet, Services Restored After DNS Failure
Massive AWS Outage Disrupts Global Internet, Services Restored After DNS Failure Chinese APT Groups Exploit Global Domains in Sweeping Cyber Campaign
Chinese APT Groups Exploit Global Domains in Sweeping Cyber Campaign French Court Orders Google, Cloudflare, Cisco to Poison DNS in Anti-Piracy Crackdown
French Court Orders Google, Cloudflare, Cisco to Poison DNS in Anti-Piracy Crackdown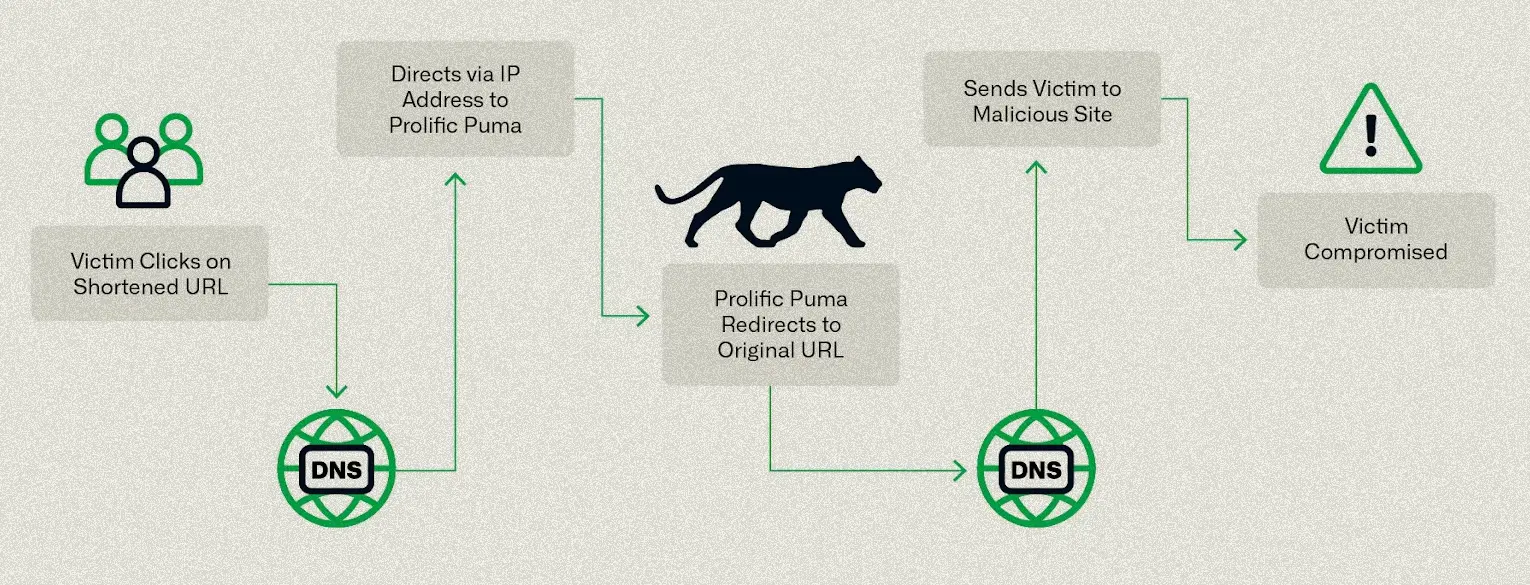 Researchers Uncover Massive Underground Link-Shortening Service Used by Malicious Actors
Researchers Uncover Massive Underground Link-Shortening Service Used by Malicious Actors CIRA Calls for Experienced Professionals to Join Its Board
CIRA Calls for Experienced Professionals to Join Its Board EU-based DNS Internet Infrastructure Beginning to Take Shape, Planned to Onboard 100 Million Users
EU-based DNS Internet Infrastructure Beginning to Take Shape, Planned to Onboard 100 Million UsersThe fourth quarter of 2025 closed with 386.9 million domain name registrations across all top-level domains (TLDs), an increase of 22.7 million domain name registrations compared to the fourth quarter of 2024, according to the latest issue of the Domain Name Industry Brief Quarterly Report released Thursday at DNIB.com. more
The Domain Name Industry Brief reports 378.5 million total domain name registrations in Q3 2025, marking a 16.2 million increase year over year and offering detailed insights into top TLD, ccTLD, and gTLD trends. more
The second quarter of 2025 closed with 371.7 million domain name registrations across all top-level domains (TLDs), an increase of 9.3 million domain name registrations compared to the second quarter of 2024, according to the latest issue of the Domain Name Industry Brief Quarterly Report released Thursday at DNIB.com. more
The first quarter of 2025 closed with 368.4 million domain name registrations across all top-level domains (TLDs), an increase of 4.2 million domain name registrations compared to the previous quarter, according to the latest issue of the Domain Name Industry Brief Quarterly Report released Thursday at DNIB.com. more
The fourth quarter of 2024 closed with 364.3 million domain name registrations across all top-level domains (TLDs), an increase of 2.0 million domain name registrations compared to the previous quarter, according to the latest issue of the Domain Name Industry Brief Quarterly Report, released Thursday at DNIB.com. more
The third quarter of 2024 closed with 362.3 million domain name registrations across all top-level domains (TLDs), a decrease of 0.1 million domain name registrations compared to the previous quarter, according to the latest issue of the Domain Name Industry Brief released Thursday at DNIB.com. more
The second quarter of 2024 closed with 362.4 million domain name registrations across all top-level domains (TLDs), unchanged compared to the first quarter of 2024, according to the latest issue of the Domain Name Industry Brief released Thursday at DNIB.com. more