

 At Munich's twin security gatherings, leaders warned that cyber conflict, transatlantic rifts and weaponised AI are pushing the rules-based order into a perilous transition, where deterrence falters, norms erode and digital sovereignty trumps multistakeholder ideals.
At Munich's twin security gatherings, leaders warned that cyber conflict, transatlantic rifts and weaponised AI are pushing the rules-based order into a perilous transition, where deterrence falters, norms erode and digital sovereignty trumps multistakeholder ideals.
 A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
 Poland thwarted a large-scale cyberattack on its energy grid without disruption, offering a rare case study in critical infrastructure resilience, decentralised energy governance, and the balancing act between openness and digital security.
Poland thwarted a large-scale cyberattack on its energy grid without disruption, offering a rare case study in critical infrastructure resilience, decentralised energy governance, and the balancing act between openness and digital security.
 Google's lawsuit against the Lighthouse phishing syndicate exposes the industrial scale of cybercrime, highlighting how criminals exploit easy access to digital infrastructure to scam millions. The broader supply chain enabling such operations demands urgent reform.
Google's lawsuit against the Lighthouse phishing syndicate exposes the industrial scale of cybercrime, highlighting how criminals exploit easy access to digital infrastructure to scam millions. The broader supply chain enabling such operations demands urgent reform.
 Cybercriminals live by the tenet "If it ain't broke, don't fix it." They'll use the same tactics repeatedly until they no longer work, then switch things up. That's why CISOs and their security teams maintain constant vigilance. Underscoring this, recent analysis of global DNS activity found that new domains continue to be a major tactic for bad actors.
Cybercriminals live by the tenet "If it ain't broke, don't fix it." They'll use the same tactics repeatedly until they no longer work, then switch things up. That's why CISOs and their security teams maintain constant vigilance. Underscoring this, recent analysis of global DNS activity found that new domains continue to be a major tactic for bad actors.
 The international community has long struggled with the challenge of translating international law into actionable norms and practices in cyberspace. The conclusion of the United Nations Open-Ended Working Group (OEWG) on the security of and in the use of information and communications technologies 2021-2025 marks a vital milestone in that ongoing process.
The international community has long struggled with the challenge of translating international law into actionable norms and practices in cyberspace. The conclusion of the United Nations Open-Ended Working Group (OEWG) on the security of and in the use of information and communications technologies 2021-2025 marks a vital milestone in that ongoing process.
 Netscout recently released its latest Threat Intelligence Report that documents DDoS attacks in the second half of 2024. As has been the trend for many years, the largest target of DDoS attacks has been ISP networks. There were over 8.9 million DDoS attacks documented in the second half of last year, up 12.75% over the first half of the year.
Netscout recently released its latest Threat Intelligence Report that documents DDoS attacks in the second half of 2024. As has been the trend for many years, the largest target of DDoS attacks has been ISP networks. There were over 8.9 million DDoS attacks documented in the second half of last year, up 12.75% over the first half of the year.
 It seems like there is more disturbing news every day about Chinese infiltration of our telecommunications networks. A recent headline said that nine large ISPs have now been infiltrated. Tom Wheeler, a previous Chairman of the FCC, recently wrote an article for the Brookings Institute that speculates that the ability of the Chinese to infiltrate our networks stems back to decisions made decades ago that have never been updated for the modern world of sophisticated hacking.
It seems like there is more disturbing news every day about Chinese infiltration of our telecommunications networks. A recent headline said that nine large ISPs have now been infiltrated. Tom Wheeler, a previous Chairman of the FCC, recently wrote an article for the Brookings Institute that speculates that the ability of the Chinese to infiltrate our networks stems back to decisions made decades ago that have never been updated for the modern world of sophisticated hacking.
 As if we didn't have a long enough list of problems to worry about, Lumen researchers at its Black Lotus Labs recently released a blog that said that it knows of three U.S. ISPs and one in India was hacked this summer. Lumen said the hackers took advantage of flaws in software provided by Versa Networks being used to manage wide-area networks.
As if we didn't have a long enough list of problems to worry about, Lumen researchers at its Black Lotus Labs recently released a blog that said that it knows of three U.S. ISPs and one in India was hacked this summer. Lumen said the hackers took advantage of flaws in software provided by Versa Networks being used to manage wide-area networks.
 On 29 March 2024, an announcement was posted notifying the world that the Open-Source Software (OSS) package "xz-utils," which includes the xz data compression program and a library of software routines called "liblzma" and which is present in most Linux distributions, had been compromised. The insertion of the compromised code was done by "Jia Tan", the official maintainer of the xz-utils package.
On 29 March 2024, an announcement was posted notifying the world that the Open-Source Software (OSS) package "xz-utils," which includes the xz data compression program and a library of software routines called "liblzma" and which is present in most Linux distributions, had been compromised. The insertion of the compromised code was done by "Jia Tan", the official maintainer of the xz-utils package.
 Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
 Last month, the Russian state-sponsored hacking group "Midnight Blizzard" gained access to the email accounts of Microsoft leadership, even exfiltrating documents and messages. The group reportedly used a simple brute-force style attack to access a forgotten test account and then exploited the permissions on that account to access the emails of employees in the cybersecurity and legal teams.
Last month, the Russian state-sponsored hacking group "Midnight Blizzard" gained access to the email accounts of Microsoft leadership, even exfiltrating documents and messages. The group reportedly used a simple brute-force style attack to access a forgotten test account and then exploited the permissions on that account to access the emails of employees in the cybersecurity and legal teams.
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
 The Uptime Institute (UI) is an IT industry research firm best known for certifying that data centers meet industry standards. UI issues an annual report that analyzes the cause of data center outages. The causes for data center outages are relevant to the broadband industry because the same kinds of issues shut down switching hubs and Network Operations Centers.
The Uptime Institute (UI) is an IT industry research firm best known for certifying that data centers meet industry standards. UI issues an annual report that analyzes the cause of data center outages. The causes for data center outages are relevant to the broadband industry because the same kinds of issues shut down switching hubs and Network Operations Centers.
 Unsuspecting website visitors are often unaware when they have landed on a spoofed page or are re-directed to malware-hosting web servers designed to steal their sensitive data and information. This attack is known as subdomain hijacking, or subdomain takeover. A web user's private information is then traded on the dark web, and cybercriminals profit, further fueling the expansion of identity theft in the online world.
Unsuspecting website visitors are often unaware when they have landed on a spoofed page or are re-directed to malware-hosting web servers designed to steal their sensitive data and information. This attack is known as subdomain hijacking, or subdomain takeover. A web user's private information is then traded on the dark web, and cybercriminals profit, further fueling the expansion of identity theft in the online world.
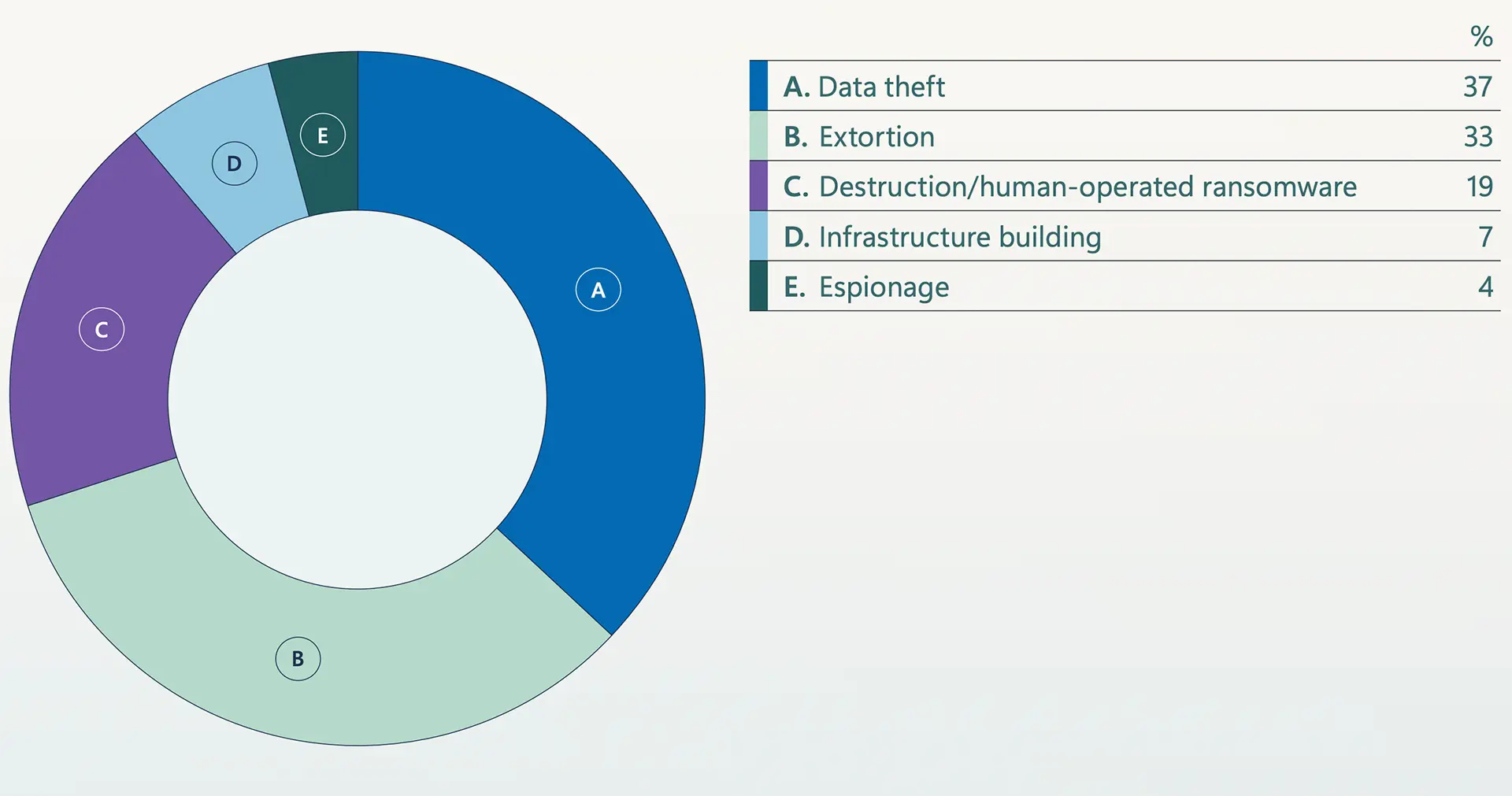 Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation
Microsoft Warns Extortion Drives Majority of Attacks Amid AI Escalation, Identity Collapse, and Global Fragmentation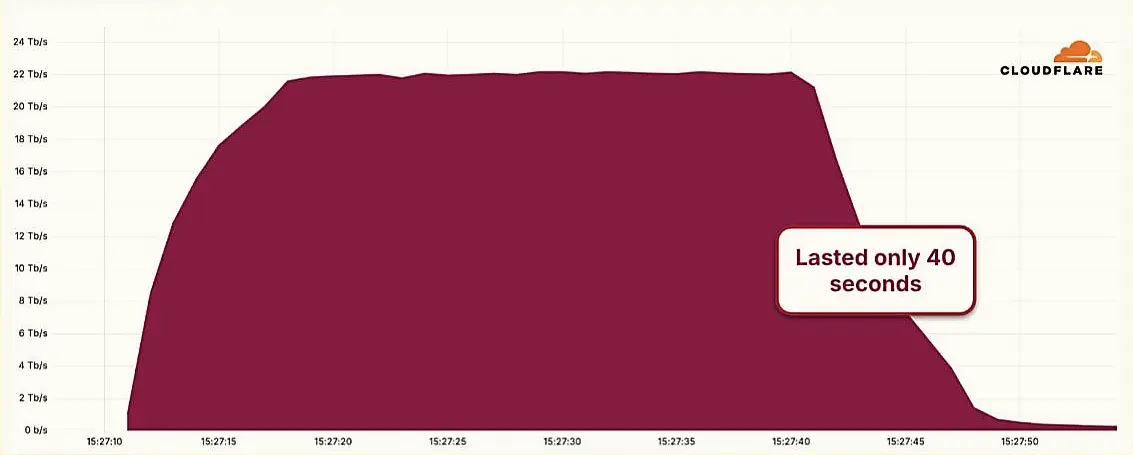 Hyper-Volumetric DDoS Attack Sets New Benchmark at 22.2 Tbps
Hyper-Volumetric DDoS Attack Sets New Benchmark at 22.2 Tbps European Airports Still Reeling from Ransomware Attack as Software Fix Nears
European Airports Still Reeling from Ransomware Attack as Software Fix Nears Chinese APT Groups Exploit Global Domains in Sweeping Cyber Campaign
Chinese APT Groups Exploit Global Domains in Sweeping Cyber Campaign Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats
Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats Massive Iberian Power Outage Raises Cybersecurity Questions
Massive Iberian Power Outage Raises Cybersecurity Questions Massive Cyber Assault on X: Musk Hints at Foreign Involvement
Massive Cyber Assault on X: Musk Hints at Foreign Involvement Chinese Hackers Exploit U.S. Telecom Systems, Eviction Efforts Lag
Chinese Hackers Exploit U.S. Telecom Systems, Eviction Efforts Lag Chinese Hackers Had Access to Canadian Government Systems for Years, Report Reveals
Chinese Hackers Had Access to Canadian Government Systems for Years, Report Reveals Sudanese Nationals Charged in Global Cyberattack Campaign
Sudanese Nationals Charged in Global Cyberattack Campaign Over 2 Million VPN Passwords Compromised by Malware Attacks
Over 2 Million VPN Passwords Compromised by Malware Attacks FBI Takes Down China-Backed Botnet, Facilitates Ransomware Negotiations
FBI Takes Down China-Backed Botnet, Facilitates Ransomware Negotiations Mystery Malware Takes Down 600,000 Windstream Routers in Coordinated Attack
Mystery Malware Takes Down 600,000 Windstream Routers in Coordinated Attack Biden Administration Alerts Governors to Rising Cyber Threats on U.S. Water Systems
Biden Administration Alerts Governors to Rising Cyber Threats on U.S. Water Systems Ransomware Crisis in U.S. Healthcare
Ransomware Crisis in U.S. Healthcare Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation
Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm
Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm