
|
||
A sophisticated cybercrime group that has maintained an especially devious Trojan horse for nearly three years has stolen login credentials of close to 300,000 online bank accounts and almost as many credit cards during that time, according to reports released today by RSA FraudAction Research Lab. The spyware is called Sinowal Trojan, also known as Torpig and Mebroot.
RSA reports that their findings are based on data collected on this Trojan over the course of almost three years—including information regarding its design and its infrastructure. Findings indicate that this may be one of the most pervasive and advanced pieces of crimeware ever created by fraudsters, say RSA experts.
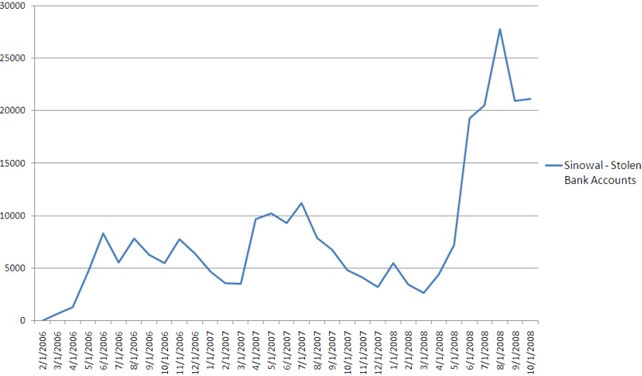 In the past six months alone, the Sinowal Trojan has compromised and stolen login credentials and other information of more than 100,000 online bank accounts. This diagram shows the rate at which Sinowal has been compromising online bank accounts. Source: RSA FraudAction Research Lab
In the past six months alone, the Sinowal Trojan has compromised and stolen login credentials and other information of more than 100,000 online bank accounts. This diagram shows the rate at which Sinowal has been compromising online bank accounts. Source: RSA FraudAction Research Lab“The sheer enormity of this makes this unique,” said Sean Brady, manager of identity protection for RSA. “And the scale is very unusual.” Overall, the gang behind Sinowal has managed to gain access to almost half a million bank accounts and credit cards, a volume RSA calls “ruthless” and “extraordinary.” “And the fact that the Trojan was managed by one group through its history and maintained for nearly three years is also very unusual,” Brady said.
Related Links:
One Sinowal Trojan + One Gang = Hundreds of Thousands of Compromised Accounts (RSA)
Virtual Heist Nets 500,000+ Bank, Credit Accounts (Washington Post)
‘Ruthless’ Trojan horse steals 500k bank, credit card log-ons (Computerworld)
Sponsored byWhoisXML API

Sponsored byRadix

Sponsored byCSC

Sponsored byVerisign

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byIPv4.Global
