


|
||
|
||
Ransomware attacks have been plaguing individual users and organizations worldwide for years now. And that is not surprising because they work. In fact, ransomware victims were asked to pay an average of US$2.5 million in 2024.
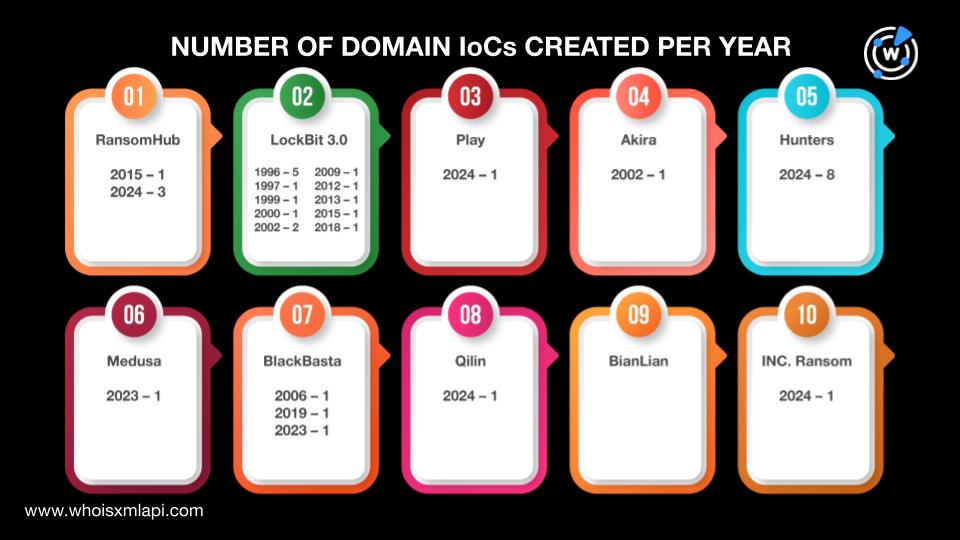
A report published on TheHackerNews named 10 of the most active ransomware families in 2024, which WhoisXML API decided to further investigate. We obtained lists of indicators of compromise (IoCs) for each of these ransomware variants:
We collated a total of 120 IoCs for all the ransomware families comprising 48 domains and 72 IP addresses. Take a look at their detailed breakdown below.
| VARIANT | DOMAIN IoCs | IP ADDRESS IoCs |
|---|---|---|
| RansomHub | 5 | 9 |
| LockBit 3.0 | 16 | 3 |
| Play | 1 | 1 |
| Akira | 1 | 1 |
| Hunters | 8 | 0 |
| Medusa | 5 | 32 |
| BlackBasta | 9 | 15 |
| Qilin | 1 | 7 |
| BianLian | 1 | 0 |
| INC. Ransom | 1 | 4 |
We sought to uncover connected artifacts that have not yet been published in any other threat report using various DNS intelligence sources. Our IoC list expansion analysis led to the discovery of:
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Before embarking on our expansion analysis, we sought to find more information on the IoCs first.
We started by querying the 48 domains identified as IoCs on Bulk WHOIS API. Only 35 of the domains had current WHOIS records. The results showed that:
Out of the 35 domains with current WHOIS record data, only 34 had registrar information. They were split among 15 registrars topped by Network Solutions and NiceNIC, which accounted for six domains each. Dynadot took the second spot with four domains. GoDaddy placed third with three domains. Amazon, Namecheap, PDR, and RU-CENTER accounted for two domains each. Cloudflare, eNom, NameSilo, Nominalia Internet, Register, Register.com, and Wild West Domains accounted for one domain each. Finally, one domain did not have a registrar on record.

Out of the 35 domains with current WHOIS record data, 32 had registrant country data. They were registered in nine different countries led by the U.S., which accounted for 19 domains. China placed second with five domains. Iceland took the third spot with two domains. Austria, India, Italy, Russia, Spain, and the U.K. accounted for one domain each. Finally, three domains did not have registrant countries on record.

We also queried the 48 domains tagged as IoCs on DNS Chronicle API and found that 36 had historical domain-to-IP resolutions. The 36 domains had 3,905 resolutions over time. A total of 11 domains—capsonic[.]com, cornwelltools[.]com, grupcovesa[.]com, hacla[.]org, imacorp[.]com, piramal[.]com, sterlingcheck[.]com, and valleywomenshealth[.]com (LockBit 3.0); dict[.]gov[.]ph (Medusa); grabify[.]link (RansomHub); and malicious-domain[.]com (BlackBasta)—posted the oldest resolution date—4 October 2019. Take a look at DNS Chronicle API details for five domains below.
| DOMAIN IoC | NUMBER OF IP RESOLUTIONS | FIRST IP RESOLUTION DATE |
|---|---|---|
| 12301230[.]co(RansomHub) | 44 | 16 July 2023 |
| americajobmail[.]site(Play) | 17 | 24 July 2023 |
| attacker-server[.]com(BlackBasta) | 55 | 17 December 2021 |
| cobcreditunion[.]com(LockBit 3.0) | 46 | 5 October 2019 |
| cybersecsentinel[.]com(INC. Ransom) | 14 | 14 February 2024 |
Next, we queried the 72 IP addresses identified as IoCs on Bulk IP Geolocation Lookup and discovered that:


The 56 IP addresses with ISP information were administered by 41 different ISPs. OVHcloud and The Constant Company were the top ISPs, accounting for five IP addresses each. Akamai and Zwiebelfreunde tied in second place with three IP addresses each. Hivelocity, Selectel, and Stark Industries took the third spot with two IP addresses each. AlexHost, Alibaba, AT&T, BeGet, Charter Communications, Cherry Servers, Clouvider, Comcast, DHUB, DigitalOcean, EDIS, EvosHosting, F3 Netze, FBW Networks, Fiber Gride, FranTech Solutions, Green Floid, Hetzner Online, IWACOM, Latitude.sh, Linode, Magenta Telekom, Mediacom Communications, Microsoft, Namecheap, Nubes, OKB Progress, ServerAstra, Shock Hosting, Simoresta, VDSINA, Verizon, ViewQwest, and VNPT accounted for one IP address each. Finally, 16 IP addresses did not have ISPs on record.

We also queried the 72 IP addresses tagged as IoCs on DNS Chronicle API and found that 56 had historical IP-to-domain resolutions. Specifically, the 56 IP addresses recorded 7,171 domain resolutions over time. Three IP addresses—104[.]86[.]182[.]8 and 209[.]197[.]3[.]8 (Qilin) and 91[.]219[.]236[.]204 (Medusa)—recorded the oldest domain resolution date—4 October 2019. Take a look at DNS Chronicle API details for five IP addresses below.
| IP ADDRESS IoC | NUMBER OF DOMAIN RESOLUTIONS | FIRST DOMAIN RESOLUTION DATE |
|---|---|---|
| 104[.]187[.]107[.]81(BlackBasta) | 14 | 19 November 2021 |
| 108[.]11[.]30[.]103(Medusa) | 13 | 19 November 2021 |
| 139[.]180[.]184[.]147(LockBit 3.0) | 41 | 2 July 2021 |
| 154[.]12[.]242[.]58(INC. Ransom) | 49 | 4 December 2024 |
| 172[.]96[.]137[.]224(Play) | 14 | 24 July 2023 |
After unearthing more information on the IoCs, we further proceeded with our IoC list expansion.
First, we queried the 48 domains identified as IoCs on WHOIS History API and found that 26 had email addresses in their historical WHOIS records. In fact, the 26 domains had 252 email addresses after duplicates were filtered out. Upon closer examination, 44 email addresses were public.
We then queried the 44 public email addresses on Reverse WHOIS API and discovered that 30 appeared in the historical WHOIS records of 944 domains after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the 944 email-connected domains showed that 27 were already considered malicious. Take a look at five examples below.
| MALICIOUS EMAIL-CONNECTED DOMAIN | ASSOCIATED THREAT |
|---|---|
| aaaeieiiiofffpn[.]su | Malware distribution |
| arculus[.]su | Malware distribution |
| eoufaoeuhoauengi[.]su | Generic threat |
| mertonera[.]su | Malware distribution |
| podisong[.]su | Malware distribution |
Next, we queried the 48 domains identified as IoCs on DNS Lookup API and discovered that 30 currently resolve to 48 IP addresses after duplicates and those already tagged as IoCs were filtered out.
A Threat Intelligence API query for the 48 additional IP addresses revealed that 34 have already figured in malicious campaigns.
This post only contains a snapshot of the full research. Download the complete findings and a sample of the additional artifacts on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Sponsored byVerisign

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byCSC

Sponsored byDNIB.com

Sponsored byVerisign

Sponsored byIPv4.Global
