

 Telecom operators are challenging OTT platforms by deploying Rich Communication Services. This reversal of roles prompts fresh regulatory scrutiny, revives the case for network neutrality, and demands a risk-based approach to preserving digital competition.
Telecom operators are challenging OTT platforms by deploying Rich Communication Services. This reversal of roles prompts fresh regulatory scrutiny, revives the case for network neutrality, and demands a risk-based approach to preserving digital competition.
 Do you know someone who deserves recognition for helping build the Internet in their region or country? Or someone who made the Internet more secure through the work they've done? Or someone who made some major technical innovation that made the Internet faster or better?
Do you know someone who deserves recognition for helping build the Internet in their region or country? Or someone who made the Internet more secure through the work they've done? Or someone who made some major technical innovation that made the Internet faster or better?
 Voice over IP (VoIP) represents a sharp break from the traditional telephony. The story of VoIP is important in helping us think beyond the simplistic framing of a "digital transition". The first stage of any technology is emulating the old. Indeed, digital telephony was just like traditional analog telephony -- just FBC (Faster, Better Cheaper) but not fundamentally different. Merely changing from analog to digital isn't transformational in itself. But it creates the opportunity for transformation.
Voice over IP (VoIP) represents a sharp break from the traditional telephony. The story of VoIP is important in helping us think beyond the simplistic framing of a "digital transition". The first stage of any technology is emulating the old. Indeed, digital telephony was just like traditional analog telephony -- just FBC (Faster, Better Cheaper) but not fundamentally different. Merely changing from analog to digital isn't transformational in itself. But it creates the opportunity for transformation.
 5G represents a threat to the level playing field and innovation of the Internet. It is the new face of the battle over network neutrality. At its inception in the 19th-century, the talking telegraph (AKA the telephone) was an amazing feat of engineering using analog technology. One could speak into a microphone in one city and be heard in another city. Accomplishing this required a very large investment in technology. The customers were consumers of the service.
5G represents a threat to the level playing field and innovation of the Internet. It is the new face of the battle over network neutrality. At its inception in the 19th-century, the talking telegraph (AKA the telephone) was an amazing feat of engineering using analog technology. One could speak into a microphone in one city and be heard in another city. Accomplishing this required a very large investment in technology. The customers were consumers of the service.
The last few weeks have reinforced the importance of modern communication networks to societies. Health care providers, schools, governments, and businesses all rely on networks that enable us to connect and collaborate remotely. Had we encountered a similar pandemic ten years ago, we would not have been able to continue our activities on the level that is possible today.
 Consumers are embracing VoIP services now more than ever as they get used to calling over Internet application services such as Skype, Facetime, and Google Hangouts. Market Research Store predict that the global value of the VoIP services market is expected to reach above USD140 billion in 2021, representing a compound annual growth rate of above 9.1% between 2016 and 2021.
Consumers are embracing VoIP services now more than ever as they get used to calling over Internet application services such as Skype, Facetime, and Google Hangouts. Market Research Store predict that the global value of the VoIP services market is expected to reach above USD140 billion in 2021, representing a compound annual growth rate of above 9.1% between 2016 and 2021.
 In just the last two weeks, there were three major DNS outages between Google, Microsoft Azure, and Fonality. But only one of these companies was able to make even bigger waves with the way they handled their blunder. Fonality, who sells VoIP services and business phone systems, offered a very rare and transparent analysis of their outage. In a detailed statement from Chief Marketing Officer Jeff Valentine, readers were given crucial insight on how to prevent the same mistakes from happening to other companies.
In just the last two weeks, there were three major DNS outages between Google, Microsoft Azure, and Fonality. But only one of these companies was able to make even bigger waves with the way they handled their blunder. Fonality, who sells VoIP services and business phone systems, offered a very rare and transparent analysis of their outage. In a detailed statement from Chief Marketing Officer Jeff Valentine, readers were given crucial insight on how to prevent the same mistakes from happening to other companies.
 With companies shifting away from on-premises and "traditional" telecom networks to Internet-based protocols - such as Voice Over IP (oIP) - the market for critical communications infrastructure - most notably SIP trunking - is on the rise; not only multiple failover sites but cloud-based SIP-as-a-service solutions are now popular options. However, there's a caveat: problems unique to SIP systems that can cause IT headaches if you're not prepared. Here are three of the most common.
With companies shifting away from on-premises and "traditional" telecom networks to Internet-based protocols - such as Voice Over IP (oIP) - the market for critical communications infrastructure - most notably SIP trunking - is on the rise; not only multiple failover sites but cloud-based SIP-as-a-service solutions are now popular options. However, there's a caveat: problems unique to SIP systems that can cause IT headaches if you're not prepared. Here are three of the most common.
 As much as I am enjoying the new Wire app, there is a fundamental dilemma that Wire faces... as well as Talko, Firefox Hello, Subrosa and every other Over-The-Top (OTT) or WebRTC application that is seeking to become THE way that we communicate via voice, chat and/or video from our mobile phones and desktops. That is: How do they gather the "directory" of people that others want to talk to?
As much as I am enjoying the new Wire app, there is a fundamental dilemma that Wire faces... as well as Talko, Firefox Hello, Subrosa and every other Over-The-Top (OTT) or WebRTC application that is seeking to become THE way that we communicate via voice, chat and/or video from our mobile phones and desktops. That is: How do they gather the "directory" of people that others want to talk to?
 Following my comments about the iPhone VoLTE announcement I had an interesting conversation with Andy Huckridge from Gigamon, a company that provides intelligent traffic visibility networking solutions for enterprises, datacentres and service providers around the globe. An interesting concept that we discussed was the 'triple challenge of network transformation'. The three elements of this challenge are...
Following my comments about the iPhone VoLTE announcement I had an interesting conversation with Andy Huckridge from Gigamon, a company that provides intelligent traffic visibility networking solutions for enterprises, datacentres and service providers around the globe. An interesting concept that we discussed was the 'triple challenge of network transformation'. The three elements of this challenge are...
 "What is a minimum set of specifications that a vendor must implement to be able to say that it is SIP-compliant?" A friend asked me that question and my response was: "It depends." and even more unfortunately:
"What is a minimum set of specifications that a vendor must implement to be able to say that it is SIP-compliant?" A friend asked me that question and my response was: "It depends." and even more unfortunately:
"I don't know." It turns out to be a challenging question to answer... and it led me to ask: "How do we define what "SIP" is for telecommunications in 2014? How do we help vendors move their products/services to be based on SIP? As we talk about "turning off the PSTN" and "moving all telecom to IP", how can we make it easier for companies to switch to using SIP?
 As far back as 2011 we predicted that Apple would eventually enter the voice market. We indicated at that time that it was just a matter of time -- in the end it took another three years... While it didn't happen at Christmas that year the company is now ready and will use the VoLTE service to enter this market, which will make it possible to replace Telstra with any other mobile operator around the world... he telcos are not ready for this. While they should be seen as the leaders in the voice call market they are too preoccupied with protecting their traditional business and it is companies like Apple and Samsung who are now leading the charge.
As far back as 2011 we predicted that Apple would eventually enter the voice market. We indicated at that time that it was just a matter of time -- in the end it took another three years... While it didn't happen at Christmas that year the company is now ready and will use the VoLTE service to enter this market, which will make it possible to replace Telstra with any other mobile operator around the world... he telcos are not ready for this. While they should be seen as the leaders in the voice call market they are too preoccupied with protecting their traditional business and it is companies like Apple and Samsung who are now leading the charge.
 Few CSPs would dispute that IP-based mobile communications are the future. But some still see little reason to replace TDM switches that, on the surface, cost them little beyond energy and housing expenses. At the recent Neustar Interactive Insights Summit, telecommunications experts Jennifer Pigg, Vice President at Yankee Group, outlined the conundrum -- and revealed the cost of doing nothing is higher than many think.
Few CSPs would dispute that IP-based mobile communications are the future. But some still see little reason to replace TDM switches that, on the surface, cost them little beyond energy and housing expenses. At the recent Neustar Interactive Insights Summit, telecommunications experts Jennifer Pigg, Vice President at Yankee Group, outlined the conundrum -- and revealed the cost of doing nothing is higher than many think.
 What is the impact of IPv6 on telecommunications, VoIP, unified communications, etc? Why should telecom operators care about IPv6? What VoIP systems already support IPv6? What efforts are underway within organizations like the IETF and the SIP Forum to ensure that telecommunications can work over IPv6?
What is the impact of IPv6 on telecommunications, VoIP, unified communications, etc? Why should telecom operators care about IPv6? What VoIP systems already support IPv6? What efforts are underway within organizations like the IETF and the SIP Forum to ensure that telecommunications can work over IPv6?
 Interested in working on an open standard for "secure Caller ID" for voice-over-IP (VoIP)? If so, the new "Secure Telephone Identity Revisited (STIR)" working group was just officially chartered within the IETF and the mailing list is open for all to subscribe.
Interested in working on an open standard for "secure Caller ID" for voice-over-IP (VoIP)? If so, the new "Secure Telephone Identity Revisited (STIR)" working group was just officially chartered within the IETF and the mailing list is open for all to subscribe.
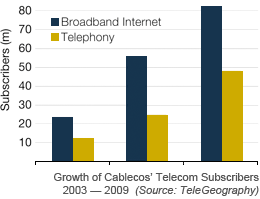 Cablecos Continue to Gain Telcom Market Share; Now at 15% and Growing
Cablecos Continue to Gain Telcom Market Share; Now at 15% and Growing Google CEO Discusses Future of the Web and Enterprise Computing
Google CEO Discusses Future of the Web and Enterprise Computing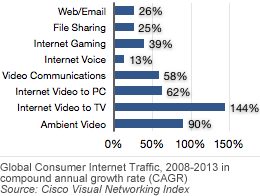 Annual Global IP Traffic Will Exceed Two-Third of a Zettabyte in 4 Years
Annual Global IP Traffic Will Exceed Two-Third of a Zettabyte in 4 Years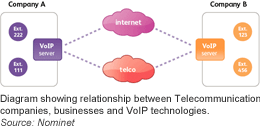 National Domain Registry Nominet Launches UK ENUM
National Domain Registry Nominet Launches UK ENUM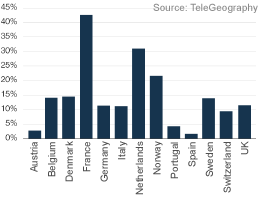 VoIP Services Reshaping the Fixed Line Market in Europe, Uptake Varies Widely
VoIP Services Reshaping the Fixed Line Market in Europe, Uptake Varies Widely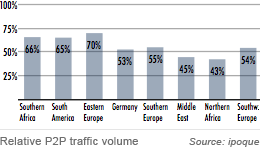 New Internet Study Finds Web and Streaming Higher Than P2P Traffic
New Internet Study Finds Web and Streaming Higher Than P2P Traffic