

 eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
eco's topDNS initiative and AV-Test are publishing monthly reports to help ISPs detect and mitigate DNS abuse by analysing malware, phishing, and PUA trends, creating a long-term data foundation for industry-wide transparency.
 A recent news story, following research from security provider Infoblox, highlighted the case of the 'Revolver Rabbit' cybercriminal gang, who have registered more than half-a-million domains to be used for the distribution of information-stealing malware. The gang make use of automated algorithms to register their domains, but unlike the long, pseudo-random ('high entropy') domain names frequently associated with such tools, the Revolver Rabbit domains instead tend to consist of hyphen-separated dictionary words (presumably so as to obfuscate their true purpose), with a string of digits at the end.
A recent news story, following research from security provider Infoblox, highlighted the case of the 'Revolver Rabbit' cybercriminal gang, who have registered more than half-a-million domains to be used for the distribution of information-stealing malware. The gang make use of automated algorithms to register their domains, but unlike the long, pseudo-random ('high entropy') domain names frequently associated with such tools, the Revolver Rabbit domains instead tend to consist of hyphen-separated dictionary words (presumably so as to obfuscate their true purpose), with a string of digits at the end.
 Android users can choose from 3.718 million applications in the Google Play Store. When installing applications, the majority of consumers trust Google to keep their devices safe from hackers. However, the reality is different. Just back in May 2023, researchers discovered over 101 infected applications in the Android store. Many of these apps counted over 400 million downloads.
Android users can choose from 3.718 million applications in the Google Play Store. When installing applications, the majority of consumers trust Google to keep their devices safe from hackers. However, the reality is different. Just back in May 2023, researchers discovered over 101 infected applications in the Android store. Many of these apps counted over 400 million downloads.
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
 The DNS Abuse Institute recently published our sixth monthly report for our project to measure DNS Abuse: DNSAI Compass ('Compass'). Compass is an initiative of the DNS Abuse Institute to measure the use of the DNS for phishing and malware. The intention is to establish a credible source of metrics for addressing DNS Abuse. We hope this will enable focused conversations, and identify opportunities for improvement.
The DNS Abuse Institute recently published our sixth monthly report for our project to measure DNS Abuse: DNSAI Compass ('Compass'). Compass is an initiative of the DNS Abuse Institute to measure the use of the DNS for phishing and malware. The intention is to establish a credible source of metrics for addressing DNS Abuse. We hope this will enable focused conversations, and identify opportunities for improvement.
 Recently I was asked by a customer how they can easily set up rollback capabilities on the endpoints in their corporate network. They had seen the marketing hype by various security technology providers that their products included rollback capabilities they could utilize if/when one of their workstations or servers was infected by malware. Having gotten this question more than once, I thought it would be a good subject to share with a broader audience.
Recently I was asked by a customer how they can easily set up rollback capabilities on the endpoints in their corporate network. They had seen the marketing hype by various security technology providers that their products included rollback capabilities they could utilize if/when one of their workstations or servers was infected by malware. Having gotten this question more than once, I thought it would be a good subject to share with a broader audience.
 Efforts have been ongoing in the ICANN community to develop a better understanding of its role in the combat of abuse. This theme has been rising in prominence every year since 2018, and 2021 appears to be the tipping point, in which consensus has built around the idea that more can be accomplished in terms of reducing the impact of rogue actors using the Internet for malicious purposes.
Efforts have been ongoing in the ICANN community to develop a better understanding of its role in the combat of abuse. This theme has been rising in prominence every year since 2018, and 2021 appears to be the tipping point, in which consensus has built around the idea that more can be accomplished in terms of reducing the impact of rogue actors using the Internet for malicious purposes.
 Two months ago, the Federal Bureau of Investigation (FBI) alerted the public to a list of domains that could easily be mistaken to be part of its network. The list of artifacts contained a total of 92 domain names, 78 of which led to potentially malicious websites, while the remaining 14 have yet to be activated or are no longer active as of 23 November 2020.
Two months ago, the Federal Bureau of Investigation (FBI) alerted the public to a list of domains that could easily be mistaken to be part of its network. The list of artifacts contained a total of 92 domain names, 78 of which led to potentially malicious websites, while the remaining 14 have yet to be activated or are no longer active as of 23 November 2020.
 Despite a recent Ninth Circuit decision denying immunity to malware detection software for targeting competitor's software, court holds that Section 230 protected Malwarebytes from liability for designating software driver program as potentially unwanted program. Plaintiff provided software that works in real-time in the background of the operating system to optimize processing and locate and install missing and outdated software drivers.
Despite a recent Ninth Circuit decision denying immunity to malware detection software for targeting competitor's software, court holds that Section 230 protected Malwarebytes from liability for designating software driver program as potentially unwanted program. Plaintiff provided software that works in real-time in the background of the operating system to optimize processing and locate and install missing and outdated software drivers.
 As 2019 wrapped up, we took some time to reflect on some of the most impactful digital developments of the past decade and how they helped change our digital lives, including: the rise of mobile and tablet usage; the importance of mobile apps; the explosion of social media and online gaming; cloud computing; domain names, brand protection and the impact of GDP. Now that we've passed the New Year, it's time to look forward.
As 2019 wrapped up, we took some time to reflect on some of the most impactful digital developments of the past decade and how they helped change our digital lives, including: the rise of mobile and tablet usage; the importance of mobile apps; the explosion of social media and online gaming; cloud computing; domain names, brand protection and the impact of GDP. Now that we've passed the New Year, it's time to look forward.
 Kim Zetter has a new story out describing a very serious attack. In fact, the implications are about as bad as possible. The attack has been dubbed ShadowHammer by Kaspersky Lab, which discovered it. Briefly, some crew of attackers -- I suspect an intelligence agency; more on that below -- has managed to abuse ASUS' update channel and private signing key to distribute bogus patches.
Kim Zetter has a new story out describing a very serious attack. In fact, the implications are about as bad as possible. The attack has been dubbed ShadowHammer by Kaspersky Lab, which discovered it. Briefly, some crew of attackers -- I suspect an intelligence agency; more on that below -- has managed to abuse ASUS' update channel and private signing key to distribute bogus patches.
 Want to be a cybersleuth and track down hackers? It may sound ambitious considering that malevolent entities are extremely clever, and tracing them requires certain skills that may not be easy to build for the typical computer user. But then again, the best defense is offense. And learning the basics of sniffing out cybercriminals may not only be necessary nowadays, it has become essential for survival on the Web. So where can you begin?
Want to be a cybersleuth and track down hackers? It may sound ambitious considering that malevolent entities are extremely clever, and tracing them requires certain skills that may not be easy to build for the typical computer user. But then again, the best defense is offense. And learning the basics of sniffing out cybercriminals may not only be necessary nowadays, it has become essential for survival on the Web. So where can you begin?
 As part of my job, I manage an incident response team that was engaged by a significant organization in Georgia whose network was infected by the QBOT (a.k.a. QAKBOT) malware. The customer had been infected for over a year, several teams before ours had failed to solve the problem, and they continued to get reinfected by the malware when they thought they had eradicated it. Over time it had spread to more than 1,000 computers in their ecosystem stealing user credentials along the way.
As part of my job, I manage an incident response team that was engaged by a significant organization in Georgia whose network was infected by the QBOT (a.k.a. QAKBOT) malware. The customer had been infected for over a year, several teams before ours had failed to solve the problem, and they continued to get reinfected by the malware when they thought they had eradicated it. Over time it had spread to more than 1,000 computers in their ecosystem stealing user credentials along the way.
 Plaintiff anti-malware software provider sued defendant -- who also provides software that protects internet users from malware, adware etc. -- bringing claims for false advertising under the Section 43(a) of Lanham Act, as well as other business torts. Plaintiff claimed that defendant wrongfully revised its software's criteria to identify plaintiff's software as a security threat when, according to plaintiff, its software is "legitimate" and posed no threat to users' computers.
Plaintiff anti-malware software provider sued defendant -- who also provides software that protects internet users from malware, adware etc. -- bringing claims for false advertising under the Section 43(a) of Lanham Act, as well as other business torts. Plaintiff claimed that defendant wrongfully revised its software's criteria to identify plaintiff's software as a security threat when, according to plaintiff, its software is "legitimate" and posed no threat to users' computers.
 The Qatar Crisis started with a targeted Poli-Cyber hack of an unprecedented nature. Its shockwaves and repercussions continue to alter political and business fortunes, directions and paradigms not only in the Gulf region but globally. Almost everyone around the world is now aware of the this crisis that started early June. By mid July a Washington Post report cited US intelligence officials that the UAE orchestrated hacking of Qatari government sites, sparking regional upheaval that started it all.
The Qatar Crisis started with a targeted Poli-Cyber hack of an unprecedented nature. Its shockwaves and repercussions continue to alter political and business fortunes, directions and paradigms not only in the Gulf region but globally. Almost everyone around the world is now aware of the this crisis that started early June. By mid July a Washington Post report cited US intelligence officials that the UAE orchestrated hacking of Qatari government sites, sparking regional upheaval that started it all.
 South Korean Telecom Giant KT Corporation Accused of Infecting 600,000 Users with Malware Over Torrent Use
South Korean Telecom Giant KT Corporation Accused of Infecting 600,000 Users with Malware Over Torrent Use Mystery Malware Takes Down 600,000 Windstream Routers in Coordinated Attack
Mystery Malware Takes Down 600,000 Windstream Routers in Coordinated Attack Unsolicited Smartwatches Bearing Malware Target U.S. Service Members: Army CID Raises Alarm
Unsolicited Smartwatches Bearing Malware Target U.S. Service Members: Army CID Raises Alarm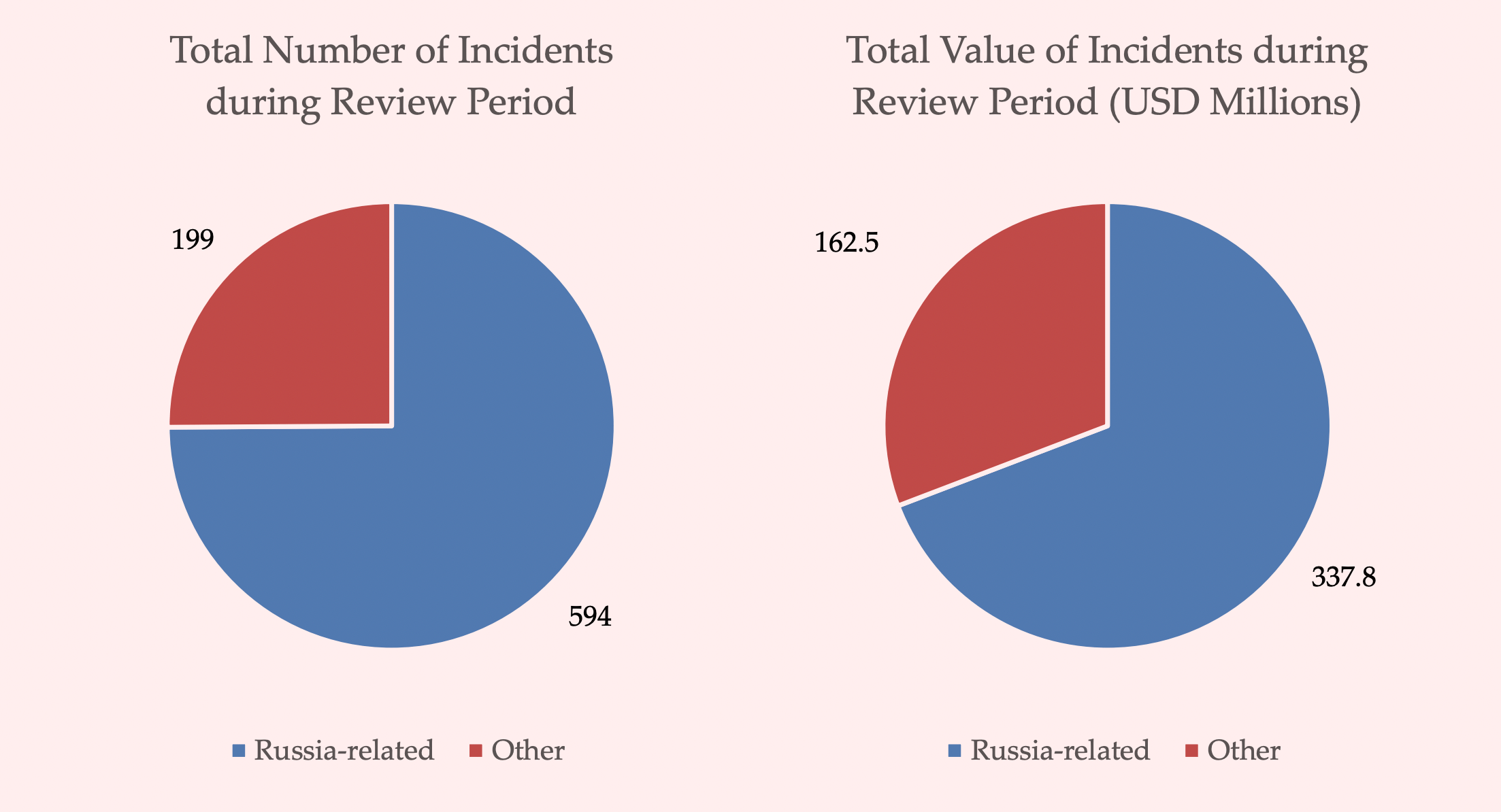 U.S. Targets Russian Mastermind Behind Dominant Ransomware Landscape, Offers $10 Million Reward
U.S. Targets Russian Mastermind Behind Dominant Ransomware Landscape, Offers $10 Million Reward Microsoft, Fortra, and Health-ISAC Take Legal Action Against the Abuse of Cobalt Strike to Combat Ransomware Attacks
Microsoft, Fortra, and Health-ISAC Take Legal Action Against the Abuse of Cobalt Strike to Combat Ransomware Attacks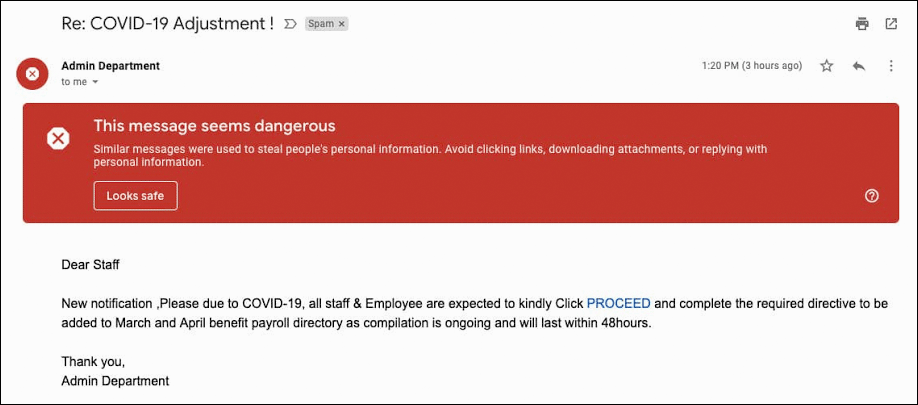 Google Reports 18 Million Daily COVID-19 Related Malware, Phishing Emails Per Day
Google Reports 18 Million Daily COVID-19 Related Malware, Phishing Emails Per Day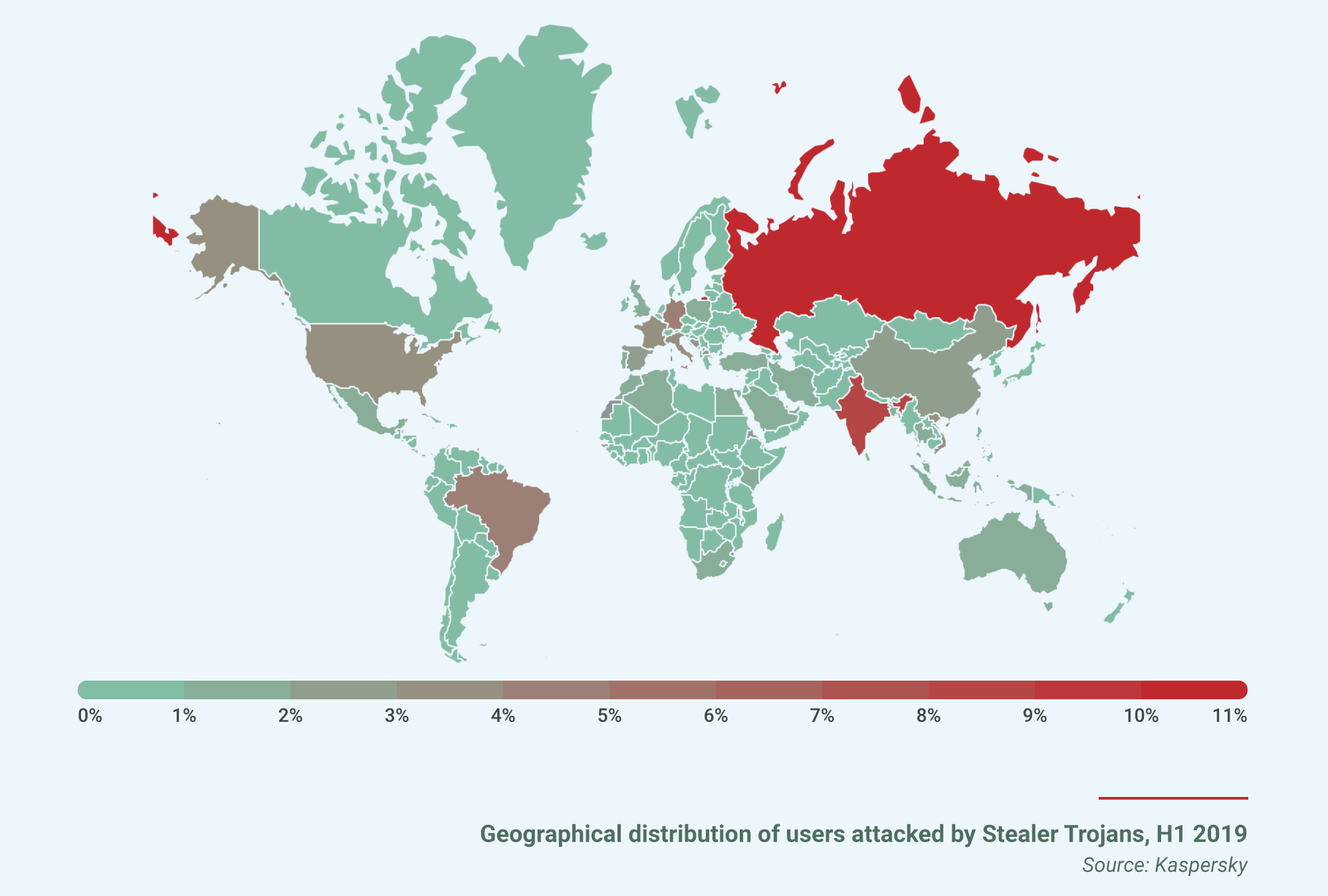 A 60% Rise Reported on Malware Designed to Harvest Consumers’ Digital Data, aka Password Stealers
A 60% Rise Reported on Malware Designed to Harvest Consumers’ Digital Data, aka Password Stealers Florida Cities Are Paying Hundreds of Thousands of Dollars in Ransom to Get Their Data Back
Florida Cities Are Paying Hundreds of Thousands of Dollars in Ransom to Get Their Data Back Notorious Hacker Group XENOTIME Expands Its Targeting Beyond Oil and Gas to Electric Utility Sector
Notorious Hacker Group XENOTIME Expands Its Targeting Beyond Oil and Gas to Electric Utility Sector Baltimore Gets Hacked: Main Computer Systems Crippled, Experts Estimate Months to Recover
Baltimore Gets Hacked: Main Computer Systems Crippled, Experts Estimate Months to Recover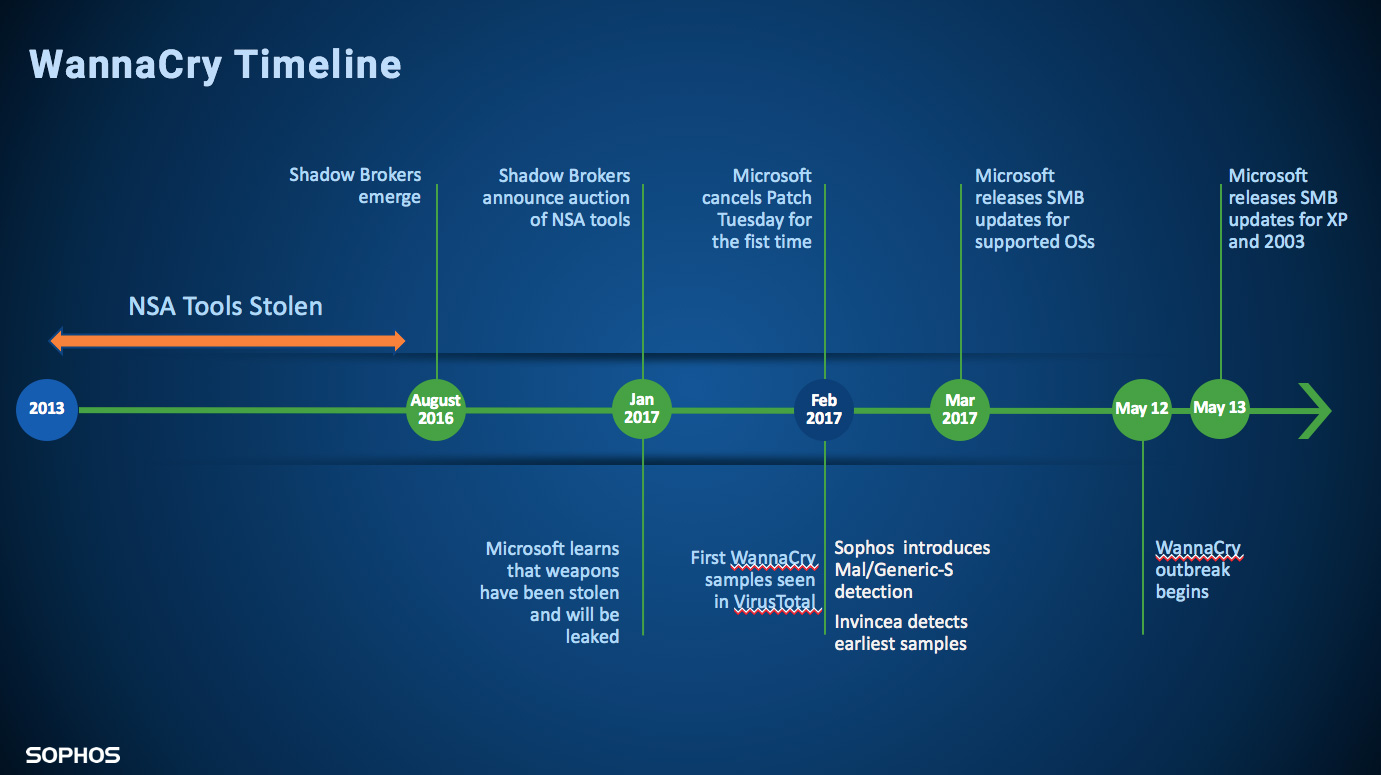 Two Years Later WannaCry Continues to Spread to Vulnerable Devices, Nearly 5M Devices Affected
Two Years Later WannaCry Continues to Spread to Vulnerable Devices, Nearly 5M Devices Affected