

 As geopolitical tensions expose the fragility of subsea cables, Low Earth Orbit satellites and the QUIC protocol promise a more resilient internet by diversifying routes, preserving session continuity, and redefining control over global data flows.
As geopolitical tensions expose the fragility of subsea cables, Low Earth Orbit satellites and the QUIC protocol promise a more resilient internet by diversifying routes, preserving session continuity, and redefining control over global data flows.
 DNSSEC promised to secure DNS with cryptographic proof, yet messy rollouts, outages, and hype backlash ruined its reputation. This piece argues that storytelling and emotions shape adoption as much as specs, and that automation enables a reset.
DNSSEC promised to secure DNS with cryptographic proof, yet messy rollouts, outages, and hype backlash ruined its reputation. This piece argues that storytelling and emotions shape adoption as much as specs, and that automation enables a reset.
 The Internet Society is accepting nominations for two seats on the 2026 Board of the Public Interest Registry, the non-profit behind .ORG and other domains serving civil society. Deadline: 30 January 2026.
The Internet Society is accepting nominations for two seats on the 2026 Board of the Public Interest Registry, the non-profit behind .ORG and other domains serving civil society. Deadline: 30 January 2026.
 The Internet is evolving far beyond screens and smartphones. A proposed seven-stage framework anticipates a future shaped by autonomous agents, sensory wearables, global connectivity, and quantum networks redefining how humans interact with the digital world.
The Internet is evolving far beyond screens and smartphones. A proposed seven-stage framework anticipates a future shaped by autonomous agents, sensory wearables, global connectivity, and quantum networks redefining how humans interact with the digital world.
 A revised governance document for Regional Internet Registries aims to replace outdated policy, enhancing transparency, continuity, and oversight in managing IP resources while preparing for future disruptions across the global Internet infrastructure.
A revised governance document for Regional Internet Registries aims to replace outdated policy, enhancing transparency, continuity, and oversight in managing IP resources while preparing for future disruptions across the global Internet infrastructure.
 The Internet has evolved from a scarcity-driven system into one defined by abundance, reshaping infrastructure, governance, and economic models while challenging long-held assumptions about addressing, network roles, and the future of protocol design.
The Internet has evolved from a scarcity-driven system into one defined by abundance, reshaping infrastructure, governance, and economic models while challenging long-held assumptions about addressing, network roles, and the future of protocol design.
 The Internet Society is seeking nominations for its 2026 Board of Trustees. Four seats are open across its global stakeholder communities, offering an opportunity to help steer the future of a trusted, open Internet.
The Internet Society is seeking nominations for its 2026 Board of Trustees. Four seats are open across its global stakeholder communities, offering an opportunity to help steer the future of a trusted, open Internet.
 With IPv4 addresses fetching up to $30 apiece and IPv6 adoption lagging, companies may be sitting on hidden digital assets. A strategic audit could unlock unexpected revenue and enhance long-term infrastructure planning.
With IPv4 addresses fetching up to $30 apiece and IPv6 adoption lagging, companies may be sitting on hidden digital assets. A strategic audit could unlock unexpected revenue and enhance long-term infrastructure planning.
 Through 2024, IPv4 leasing stayed steady at about $0.50 per IP per month, even as purchase prices diverged by block size. Large blocks (like /16) corrected notably while smaller blocks (/20 - /24) remained comparatively firm. That spread reflected shifting enterprise behavior (more surgical allocations, less speculative buying) and the resilience of subscription-like leasing in unstable conditions.
Through 2024, IPv4 leasing stayed steady at about $0.50 per IP per month, even as purchase prices diverged by block size. Large blocks (like /16) corrected notably while smaller blocks (/20 - /24) remained comparatively firm. That spread reflected shifting enterprise behavior (more surgical allocations, less speculative buying) and the resilience of subscription-like leasing in unstable conditions.
 The arrangements regarding the composition and organisation of the provision and operation of authoritative root servers are one of the more long-lasting aspects of the public Internet. In the late 1980s, Jon Postel, as the IANA, worked with a small set of interested organisations to provide this service. It was informally arranged, without contracts and without payment of any form.
The arrangements regarding the composition and organisation of the provision and operation of authoritative root servers are one of the more long-lasting aspects of the public Internet. In the late 1980s, Jon Postel, as the IANA, worked with a small set of interested organisations to provide this service. It was informally arranged, without contracts and without payment of any form.
 A Supreme Court judge in Mauritius has been appointed to investigate AFRINIC, Africa's IP address registry, following allegations of misconduct, legal irregularities, and criminal falsification. The inquiry marks a pivotal moment in African internet governance, with implications for regional digital infrastructure and the continent's credibility in managing critical online resources.
A Supreme Court judge in Mauritius has been appointed to investigate AFRINIC, Africa's IP address registry, following allegations of misconduct, legal irregularities, and criminal falsification. The inquiry marks a pivotal moment in African internet governance, with implications for regional digital infrastructure and the continent's credibility in managing critical online resources.
 This study analyzes the differences in domain name and IP address strategies among a number of current mainstream artificial intelligence (AI) service providers. We find that these technical choices not only reflect deployment decisions but also deep-seated corporate knowledge and capabilities in Internet infrastructure service provision, as well as brand positioning and market strategies.
This study analyzes the differences in domain name and IP address strategies among a number of current mainstream artificial intelligence (AI) service providers. We find that these technical choices not only reflect deployment decisions but also deep-seated corporate knowledge and capabilities in Internet infrastructure service provision, as well as brand positioning and market strategies.
 At the 20th Internet Governance Forum in Lillestrøm, Norway, the UN Internet Governance Forum's dynamic coalition Internet Standards, Security and Safety (IS3C) released its new report on post-quantum policies. This report presents the findings of a collaborative study undertaken by IS3C and the French domain name registry Afnic and examines the critical need for Post-Quantum Cryptography (PQC) to achieve greater security in the ever-expanding global IoT landscape.
At the 20th Internet Governance Forum in Lillestrøm, Norway, the UN Internet Governance Forum's dynamic coalition Internet Standards, Security and Safety (IS3C) released its new report on post-quantum policies. This report presents the findings of a collaborative study undertaken by IS3C and the French domain name registry Afnic and examines the critical need for Post-Quantum Cryptography (PQC) to achieve greater security in the ever-expanding global IoT landscape.
 Networks are typically built to provide certain services at an expected scale. The rationale for this focused objective is entirely reasonable: to overachieve would be inefficient and costly. So, we build service infrastructure to a level of sufficient capability to meet expectations and no more. In ideal conditions, this leads to a widely deployed and highly efficient infrastructure that is capable of supporting a single service profile.
Networks are typically built to provide certain services at an expected scale. The rationale for this focused objective is entirely reasonable: to overachieve would be inefficient and costly. So, we build service infrastructure to a level of sufficient capability to meet expectations and no more. In ideal conditions, this leads to a widely deployed and highly efficient infrastructure that is capable of supporting a single service profile.
 The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light!
The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light!
 David J. Farber, Early Architect of the Internet, Dies at 91
David J. Farber, Early Architect of the Internet, Dies at 91 Internet Visionaries Honored with Postel Service Award
Internet Visionaries Honored with Postel Service Award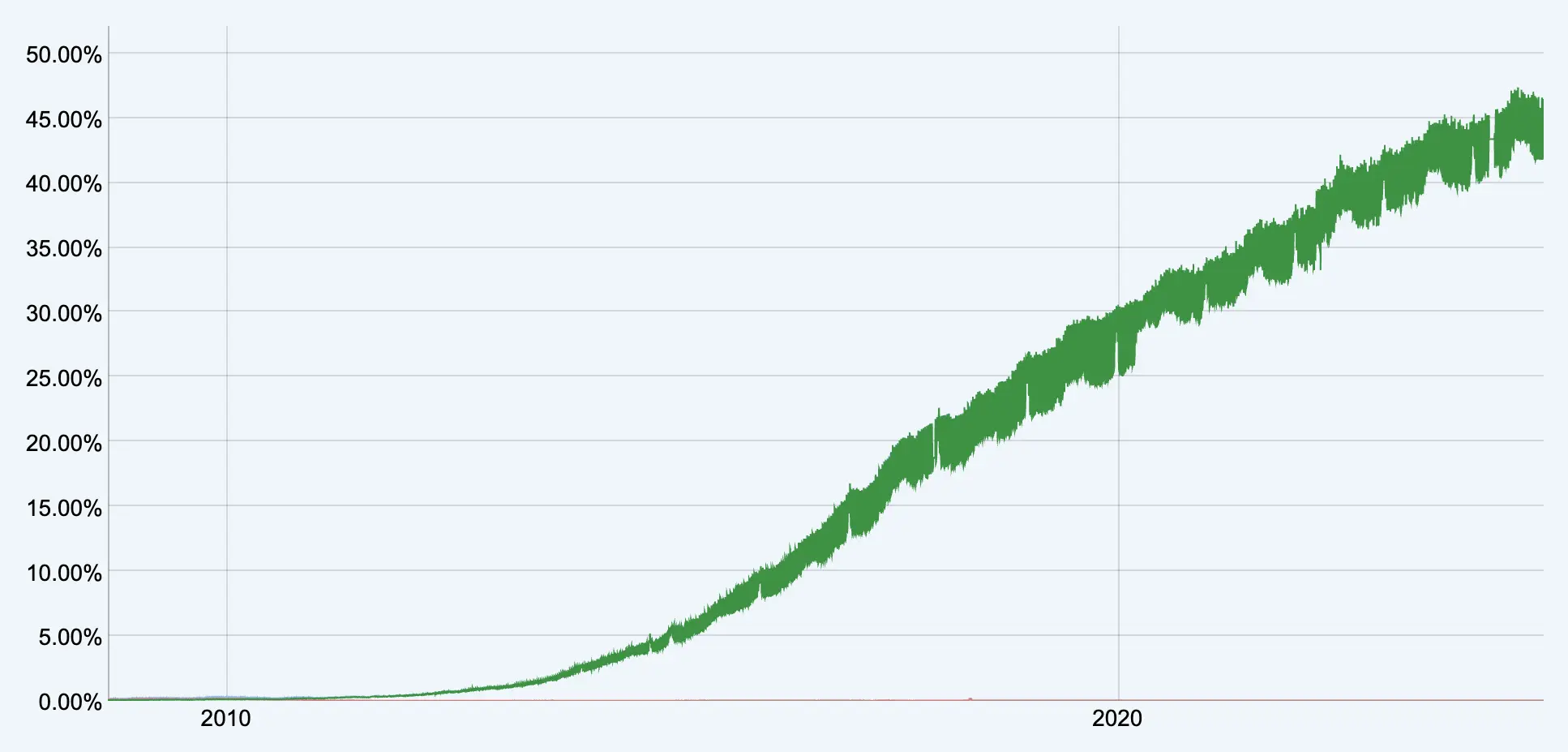 IPv6 Transition Stalls as Internet Moves Beyond IP Addresses
IPv6 Transition Stalls as Internet Moves Beyond IP Addresses Internet’s 50th Anniversary Celebrated Worldwide with IEEE Event
Internet’s 50th Anniversary Celebrated Worldwide with IEEE Event In Memoriam: Dave Mills (1938-2024)
In Memoriam: Dave Mills (1938-2024) Vint Cerf Receives IEEE Medal of Honor
Vint Cerf Receives IEEE Medal of Honor U.S. Department of Energy Unveils Blueprint for the Quantum Internet
U.S. Department of Energy Unveils Blueprint for the Quantum Internet “lo” and Behold
“lo” and Behold