
 The Internet Watch Foundation (IWF) leads the charge to combat child sexual abuse material (CSAM) online, and we at Public Interest Registry (PIR) are dedicated to supporting their efforts. We are honored to work with them across two important programs: Domain Alerts and TLD Hopping List. IWF services have been extremely successful in addressing CSAM on .ORG over the past five years more
The Internet Watch Foundation (IWF) leads the charge to combat child sexual abuse material (CSAM) online, and we at Public Interest Registry (PIR) are dedicated to supporting their efforts. We are honored to work with them across two important programs: Domain Alerts and TLD Hopping List. IWF services have been extremely successful in addressing CSAM on .ORG over the past five years more
 In two weeks, final negotiations will begin on the UN's proposed Cybercrime Convention, a document which has elicited widespread concern from civil society, industry groups, and some states due to the serious risks it poses to human rights, including privacy and freedom of expression. Since 2022, GPD and other groups, including EFF, Human Rights Watch and Privacy International, have sought to alert stakeholders within the process to the need for substantial revisions... more
In two weeks, final negotiations will begin on the UN's proposed Cybercrime Convention, a document which has elicited widespread concern from civil society, industry groups, and some states due to the serious risks it poses to human rights, including privacy and freedom of expression. Since 2022, GPD and other groups, including EFF, Human Rights Watch and Privacy International, have sought to alert stakeholders within the process to the need for substantial revisions... more
 The 2024 "To-Do-List" for all stakeholders in the global Internet Governance Ecosystem is a very long one. Not only the real world but also the virtual world is in turmoil. Vint Cerf once argued that the Internet is just a mirror of the existing world. If the existing world is in trouble, the Internet world has a problem. more
The 2024 "To-Do-List" for all stakeholders in the global Internet Governance Ecosystem is a very long one. Not only the real world but also the virtual world is in turmoil. Vint Cerf once argued that the Internet is just a mirror of the existing world. If the existing world is in trouble, the Internet world has a problem. more
 Users are tired of hearing about data breaches that put their sensitive information at risk. Reports show that cybercriminals stole 6.41 million records in the first quarter of 2023 alone. From medical data to passwords and even DNA information, hackers have stolen a lot of sensitive information in 2023. more
Users are tired of hearing about data breaches that put their sensitive information at risk. Reports show that cybercriminals stole 6.41 million records in the first quarter of 2023 alone. From medical data to passwords and even DNA information, hackers have stolen a lot of sensitive information in 2023. more
 The FCA has been naming and shaming financial scam domains for decades. Its "warning list" is probably one the most extensive databases of its kind. But does it do a good enough job of actually warning people? Let us begin with the FCA website, which would not exactly get full points for user-friendliness: locating the "watch list" is a task in and of itself, to say nothing of consulting and scrutinising it. more
The FCA has been naming and shaming financial scam domains for decades. Its "warning list" is probably one the most extensive databases of its kind. But does it do a good enough job of actually warning people? Let us begin with the FCA website, which would not exactly get full points for user-friendliness: locating the "watch list" is a task in and of itself, to say nothing of consulting and scrutinising it. more
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology. more
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology. more
 As the brand protection industry approaches a quarter of a century in age, following the founding of pioneers Envisional and MarkMonitor in 1999, I present an overview of some of the main outstanding issues which are frequently unaddressed or are generally only partially solved by brand protection service providers. I term these the 'Millennium Problems' in reference to the set of unsolved mathematical problems published in 2000 by the Clay Mathematics Institute, and for which significant prizes were offered for solutions. more
As the brand protection industry approaches a quarter of a century in age, following the founding of pioneers Envisional and MarkMonitor in 1999, I present an overview of some of the main outstanding issues which are frequently unaddressed or are generally only partially solved by brand protection service providers. I term these the 'Millennium Problems' in reference to the set of unsolved mathematical problems published in 2000 by the Clay Mathematics Institute, and for which significant prizes were offered for solutions. more
 While threat actors can use any domain across thousands of top-level domains (TLDs), they often have favorites. For instance, you may be familiar with Spamhaus's 10 most-abused TLDs for spamming. WhoisXML API researchers recently built on this list by analyzing 40,000 newly registered domains (NRDs) that sported some of the listed unreputable TLDs. We called this study "DNS Abuse Trends: Dissecting the Domains Under the Most-Abused TLDs." more
While threat actors can use any domain across thousands of top-level domains (TLDs), they often have favorites. For instance, you may be familiar with Spamhaus's 10 most-abused TLDs for spamming. WhoisXML API researchers recently built on this list by analyzing 40,000 newly registered domains (NRDs) that sported some of the listed unreputable TLDs. We called this study "DNS Abuse Trends: Dissecting the Domains Under the Most-Abused TLDs." more
 Brand impersonation happens much more often than people realize. In CSC's latest Domain Security Report, we found that 75% of domains for the Global 2000 that contained more than six characters from the brand names were not actually owned by the brands themselves. The intent of these fake domain registrations is to leverage the trust placed on the targeted brands to launch phishing attacks, other forms of digital brand abuse, or IP infringement... more
Brand impersonation happens much more often than people realize. In CSC's latest Domain Security Report, we found that 75% of domains for the Global 2000 that contained more than six characters from the brand names were not actually owned by the brands themselves. The intent of these fake domain registrations is to leverage the trust placed on the targeted brands to launch phishing attacks, other forms of digital brand abuse, or IP infringement... more
 The DNS Abuse Institute recently published our sixth monthly report for our project to measure DNS Abuse: DNSAI Compass ('Compass'). Compass is an initiative of the DNS Abuse Institute to measure the use of the DNS for phishing and malware. The intention is to establish a credible source of metrics for addressing DNS Abuse. We hope this will enable focused conversations, and identify opportunities for improvement. more
The DNS Abuse Institute recently published our sixth monthly report for our project to measure DNS Abuse: DNSAI Compass ('Compass'). Compass is an initiative of the DNS Abuse Institute to measure the use of the DNS for phishing and malware. The intention is to establish a credible source of metrics for addressing DNS Abuse. We hope this will enable focused conversations, and identify opportunities for improvement. more
 In the first article of this two-part blog series, we looked at how frequently domains were used by bad actors for phishing activity across individual top-level domains (TLDs) or domain extensions, using data from CSC's Fraud Protection services, powered by our DomainSecSM platform. In this second article, we analyze multiple datasets to determine the highest-threat TLDs, based on the frequency with which the domains are used egregiously for a range of cybercrimes. more
In the first article of this two-part blog series, we looked at how frequently domains were used by bad actors for phishing activity across individual top-level domains (TLDs) or domain extensions, using data from CSC's Fraud Protection services, powered by our DomainSecSM platform. In this second article, we analyze multiple datasets to determine the highest-threat TLDs, based on the frequency with which the domains are used egregiously for a range of cybercrimes. more
 A domain name consists of two main elements: the second-level domain name to the left of the dot - often consisting of a brand name or relevant keywords - and the domain extension or top-level domain (TLD) to the right of the dot. Domain names form the key elements of the readable web addresses allowing users to access pages on the internet and also allowing the construction of email addresses. more
A domain name consists of two main elements: the second-level domain name to the left of the dot - often consisting of a brand name or relevant keywords - and the domain extension or top-level domain (TLD) to the right of the dot. Domain names form the key elements of the readable web addresses allowing users to access pages on the internet and also allowing the construction of email addresses. more
 At the beginning of 2023, the good news is that, in spite of all geopolitical tensions, the Internet infrastructure built around TCP/IP continues to carry emails, web pages, videos, and podcasts across the globe. Technically, the Internet remains robust. The bad news is that more and more digital borders will continue to affect the global nature of international digital communication... more
At the beginning of 2023, the good news is that, in spite of all geopolitical tensions, the Internet infrastructure built around TCP/IP continues to carry emails, web pages, videos, and podcasts across the globe. Technically, the Internet remains robust. The bad news is that more and more digital borders will continue to affect the global nature of international digital communication... more
 Domain name abuse is one of the most dangerous and under-regulated issues in digital business security today. An attack on a web domain can lead to the redirection of a company's website, domain spoofing, phishing attacks, network breaches, and business email compromise (BEC). Domains used as a company's online world are part of an organization's external attack surface and need to be continuously monitored for cybercrime attacks and fraud. more
Domain name abuse is one of the most dangerous and under-regulated issues in digital business security today. An attack on a web domain can lead to the redirection of a company's website, domain spoofing, phishing attacks, network breaches, and business email compromise (BEC). Domains used as a company's online world are part of an organization's external attack surface and need to be continuously monitored for cybercrime attacks and fraud. more
 More and more information is becoming available about the breach of Optus (Australia's second-largest telco). It looks like the hacker is more of an amateur than a professional criminal or a "state actor." This makes the hack even more worrisome. It looks as though Optus didn't have its security house in order. This makes the issue all the more painful for the company. It will dent its reputation, and customers could become somewhat wary about dealing with the company. more
More and more information is becoming available about the breach of Optus (Australia's second-largest telco). It looks like the hacker is more of an amateur than a professional criminal or a "state actor." This makes the hack even more worrisome. It looks as though Optus didn't have its security house in order. This makes the issue all the more painful for the company. It will dent its reputation, and customers could become somewhat wary about dealing with the company. more
 Ransomware Crisis in U.S. Healthcare
Ransomware Crisis in U.S. Healthcare Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation
Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation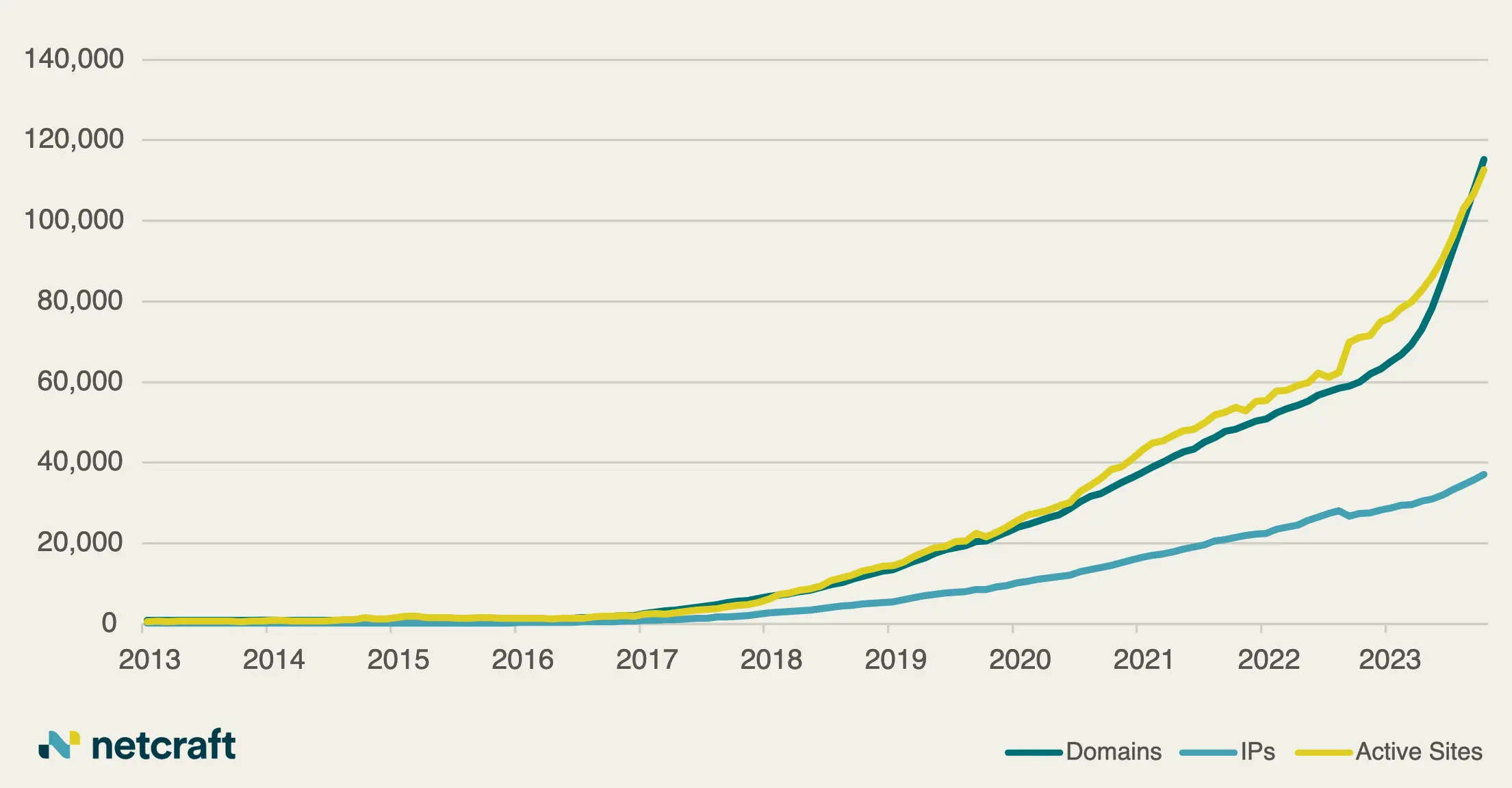 Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space
Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space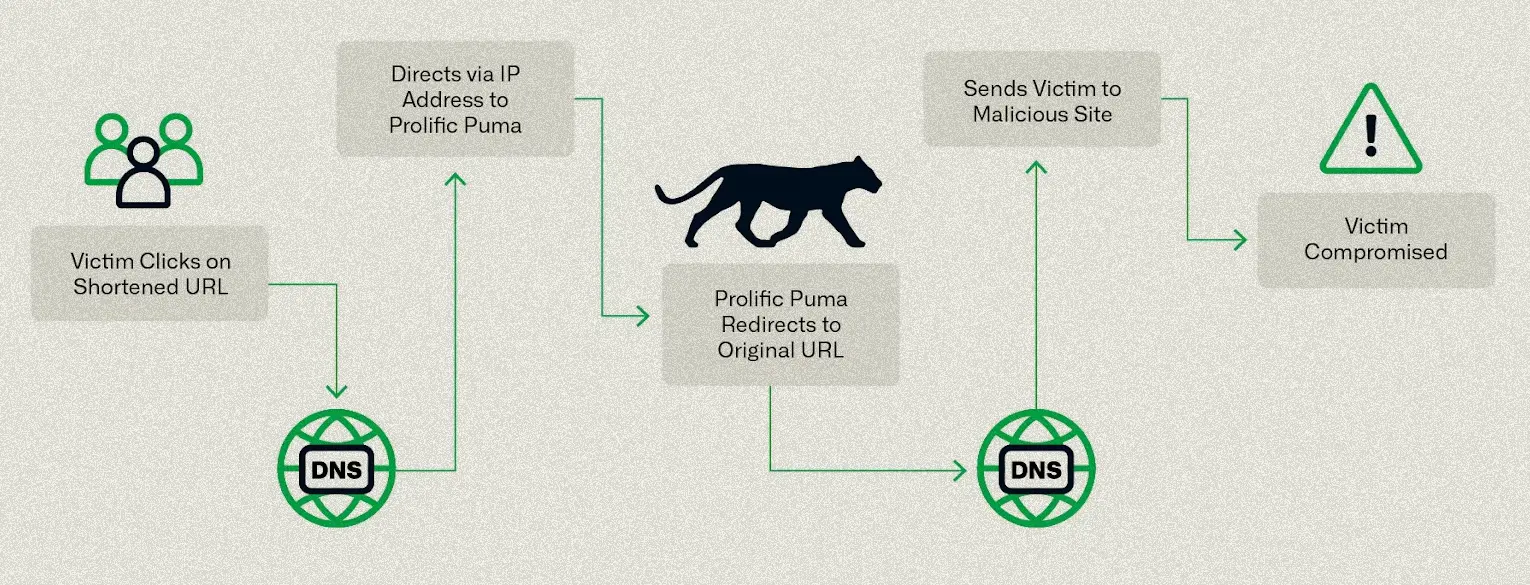 Researchers Uncover Massive Underground Link-Shortening Service Used by Malicious Actors
Researchers Uncover Massive Underground Link-Shortening Service Used by Malicious Actors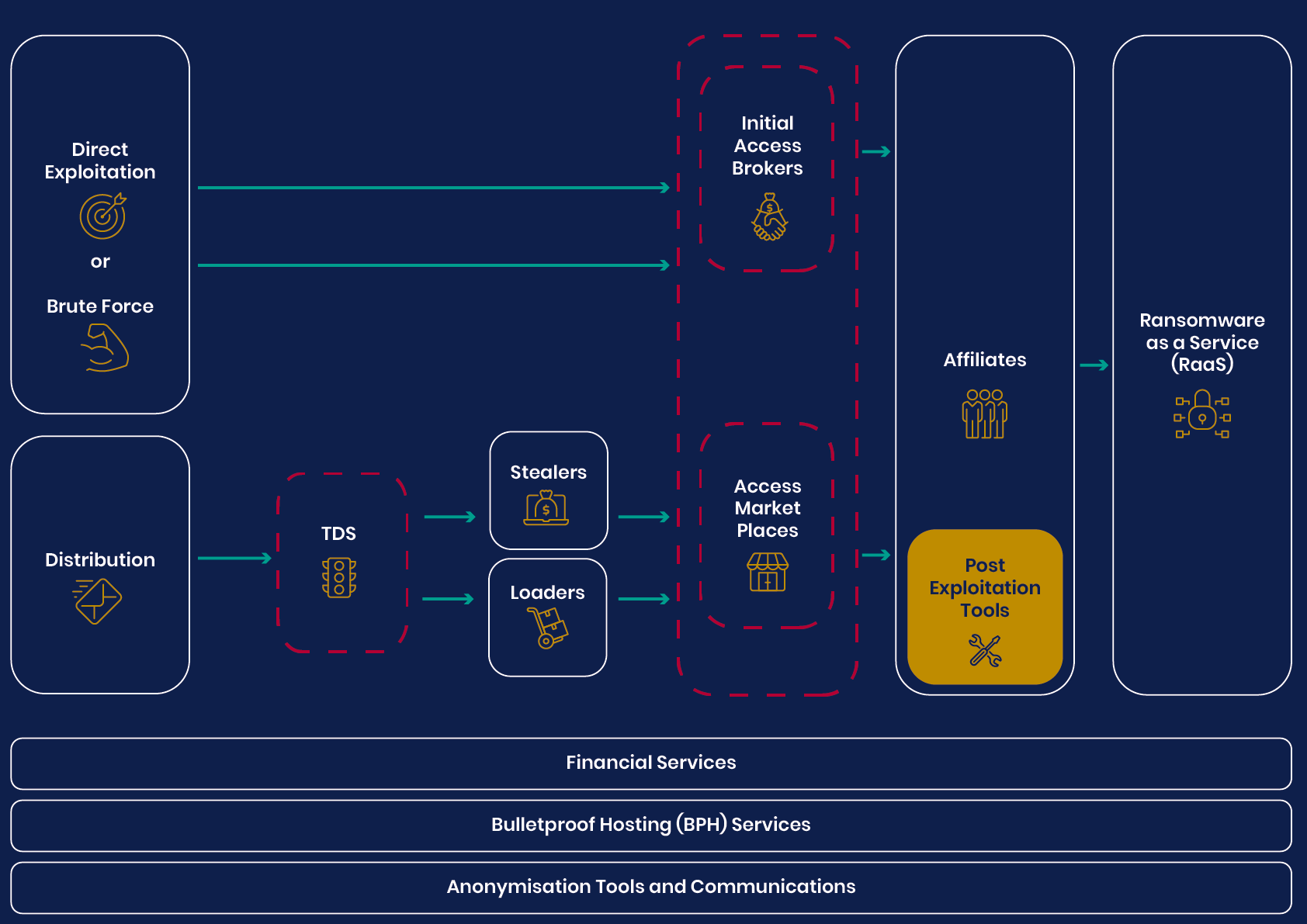 UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem
UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem The Hague to Probe Cyberwarfare Under Existing International Law
The Hague to Probe Cyberwarfare Under Existing International Law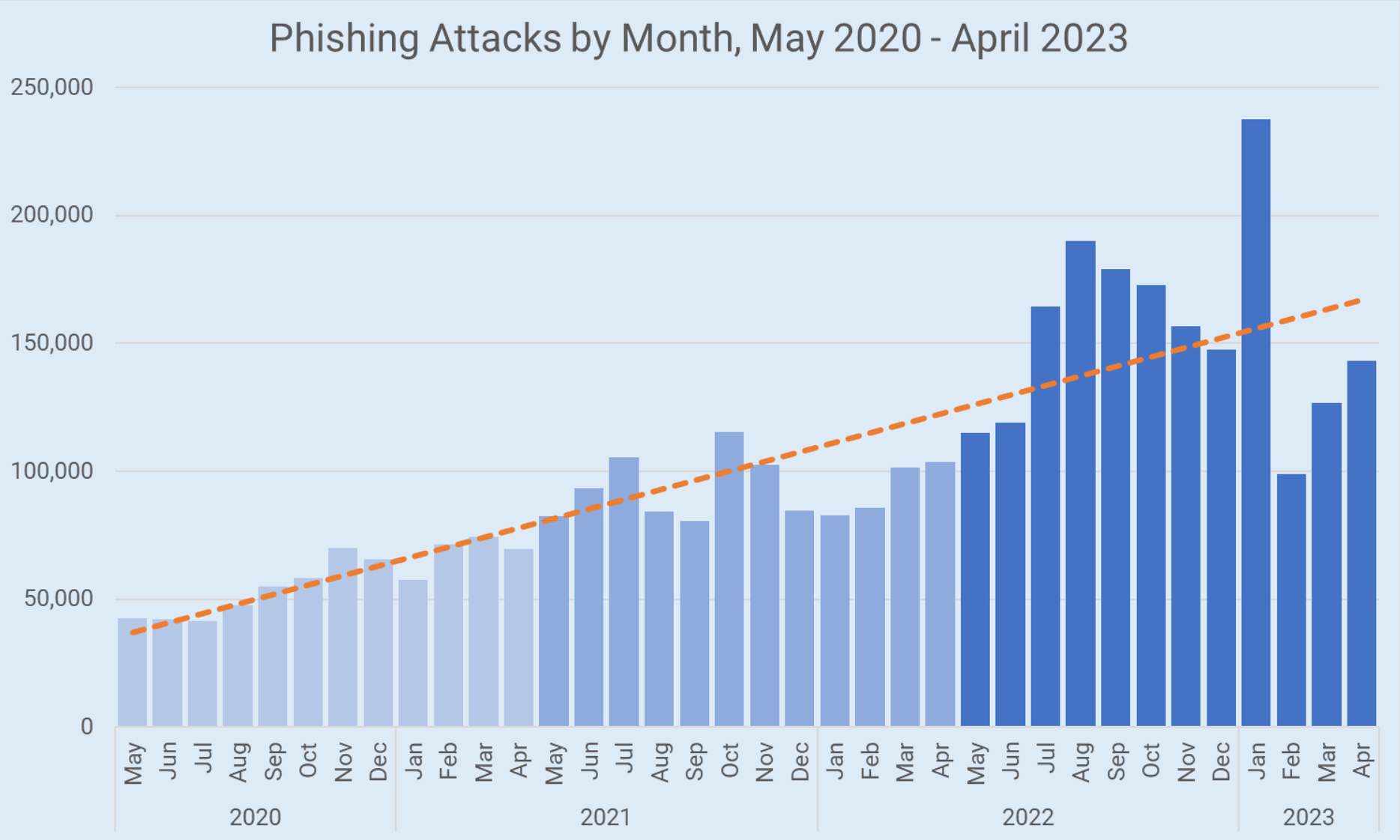 Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed
Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed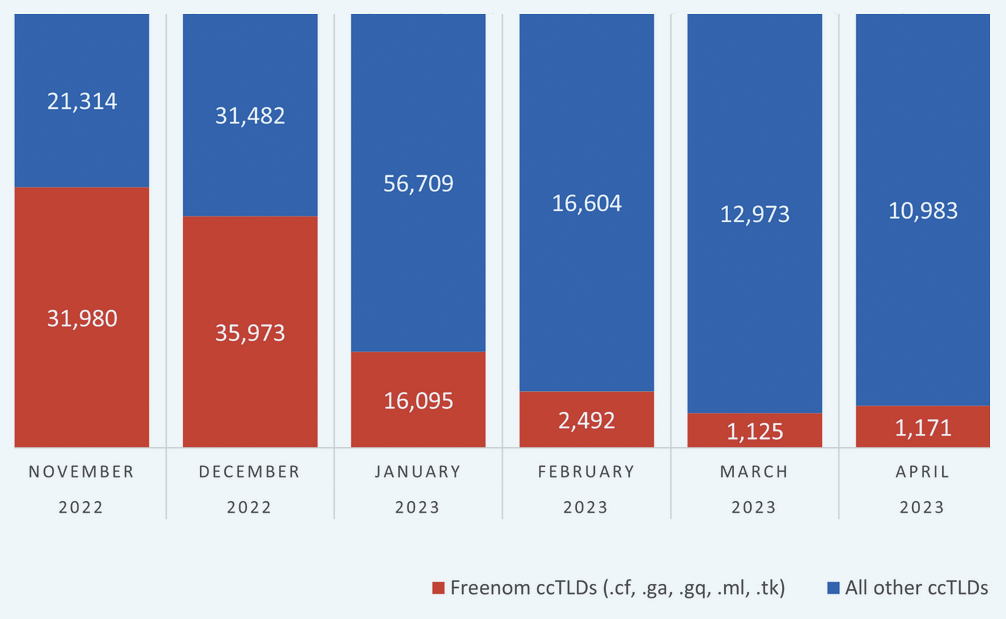 Meta Lawsuit Leads to Significant Decline in Phishing Domains Tied to Freenom
Meta Lawsuit Leads to Significant Decline in Phishing Domains Tied to Freenom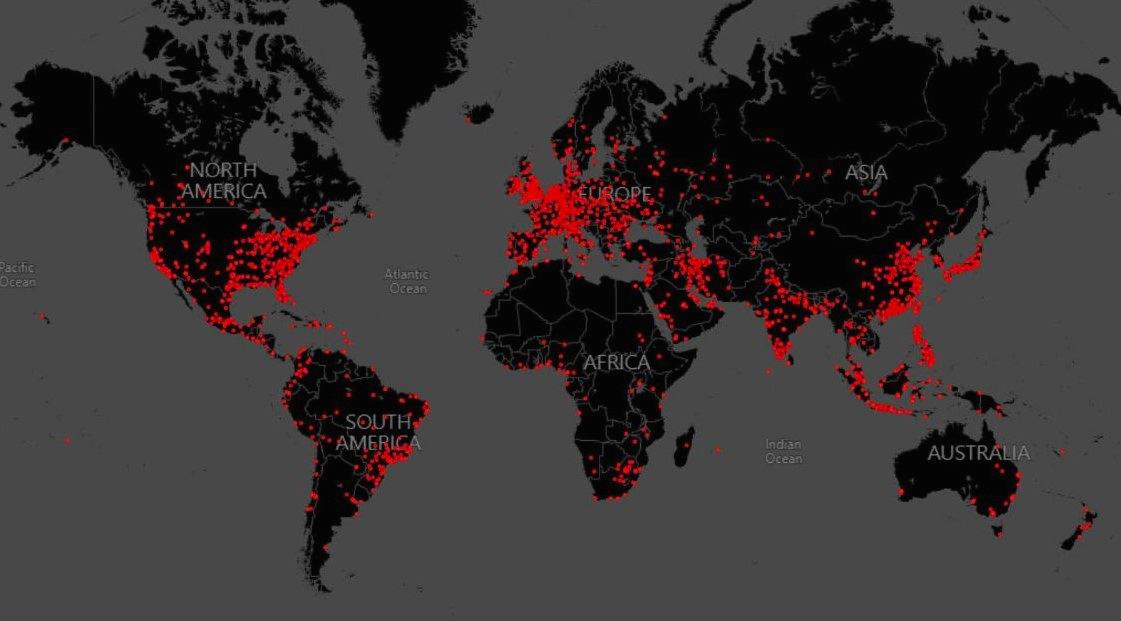 Microsoft, Fortra, and Health-ISAC Take Legal Action Against the Abuse of Cobalt Strike to Combat Ransomware Attacks
Microsoft, Fortra, and Health-ISAC Take Legal Action Against the Abuse of Cobalt Strike to Combat Ransomware Attacks FBI Takes Down ‘Genesis Market’ Cybercrime Store: Dozens Arrested Worldwide
FBI Takes Down ‘Genesis Market’ Cybercrime Store: Dozens Arrested Worldwide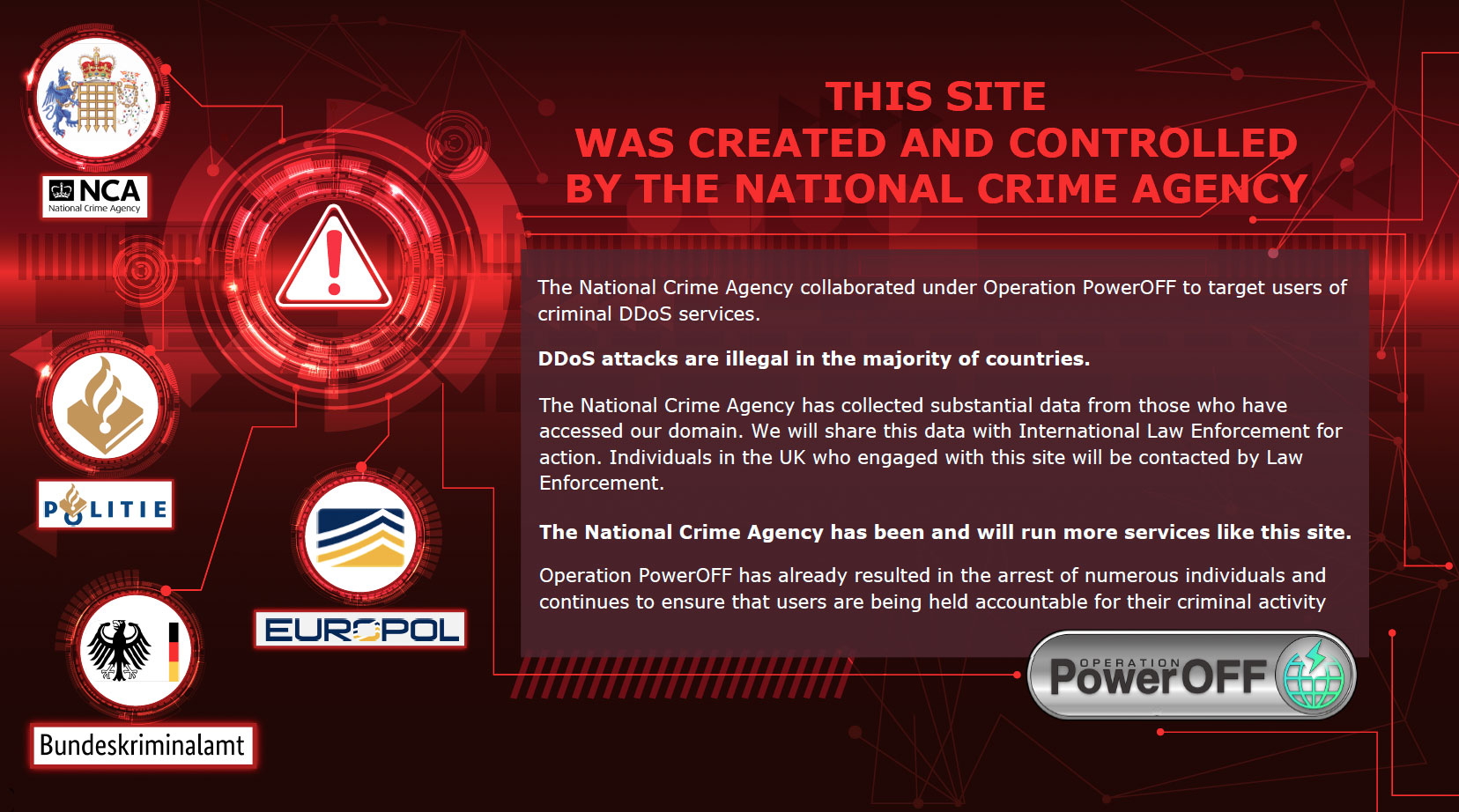 NCA Launches Campaign to Curb DDoS-for-Hire Website Use, Warns of Legal Risks
NCA Launches Campaign to Curb DDoS-for-Hire Website Use, Warns of Legal Risks Europol Warns on the Criminal Usage of ChatGPT and Its Implications for Law Enforcement
Europol Warns on the Criminal Usage of ChatGPT and Its Implications for Law Enforcement Biden Administration Bans Federal Agencies from Using Commercial Spyware
Biden Administration Bans Federal Agencies from Using Commercial Spyware