

 The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light!
The story of computing and communications over the past eighty years has been a story of quite astounding improvements in the capability, cost and efficiency of computers and communications. If the same efficiency improvements had been made in the automobile industry cars would cost a couple of dollars, would cost fractions of a cent to use for trips, and be capable of travelling at speeds probably approaching the speed of light!
 Dave Taht died on April 1st. I met him only recently, and never in person, but his passing saddens me. His technical work and evangelism have improved the Internet, and I will give some examples of his contributions to the Internet community and users, but I am sad because he was a good person -- idealistic, unselfish, open, and funny. I'll miss him. First, his contributions, then his values.
Dave Taht died on April 1st. I met him only recently, and never in person, but his passing saddens me. His technical work and evangelism have improved the Internet, and I will give some examples of his contributions to the Internet community and users, but I am sad because he was a good person -- idealistic, unselfish, open, and funny. I'll miss him. First, his contributions, then his values.
 The Christmas Goat attracted 809 unique AS numbers this year, with IPv6 usage led by the USA and Finland. Despite a rise to 39% IPv6 adoption, challenges like outdated routers persist. As this 15-year tradition concludes, the holiday Goat highlights the progress and hurdles of IPv6 integration.
The Christmas Goat attracted 809 unique AS numbers this year, with IPv6 usage led by the USA and Finland. Despite a rise to 39% IPv6 adoption, challenges like outdated routers persist. As this 15-year tradition concludes, the holiday Goat highlights the progress and hurdles of IPv6 integration.
 If you operate an Internet Exchange Point (IXP) or are interested in creating one, the Internet Society has a “Sustainable Peering Infrastructure” funding program that is open for applications until this Friday, September 6, 2024... Grant funds from USD $5,000 up to $50,000 are open to all regions and are available to assist in equipment purchases (switches, optic modules, servers, and routers), training, capacity building, and community development.
If you operate an Internet Exchange Point (IXP) or are interested in creating one, the Internet Society has a “Sustainable Peering Infrastructure” funding program that is open for applications until this Friday, September 6, 2024... Grant funds from USD $5,000 up to $50,000 are open to all regions and are available to assist in equipment purchases (switches, optic modules, servers, and routers), training, capacity building, and community development.
 The Optus outage in Australia from last year was immediately on my mind when on Friday afternoon a similar event swept, this time, across the world. Also, in this case it was a software update that caused the problem. This time from global security software provider CrowdStrike. The culprit appears to be an update to the CrowdStrike Falcon platform, a security monitoring tool widely deployed by businesses and organisations on Microsoft desktop computers and notebooks.
The Optus outage in Australia from last year was immediately on my mind when on Friday afternoon a similar event swept, this time, across the world. Also, in this case it was a software update that caused the problem. This time from global security software provider CrowdStrike. The culprit appears to be an update to the CrowdStrike Falcon platform, a security monitoring tool widely deployed by businesses and organisations on Microsoft desktop computers and notebooks.
 CLAT/NAT64 is utilized across many mobile networks globally, and I am only talking about Ethernet and Wi-Fi in home and small office/home office (SOHO) environments. I experimented by completely disabling IPv4 at home and established a SSID where my MacBook Pro operates without an actual IPv4 address. The MacBook supports CLAT (RFC 6877), and by implementing PREF64 (RFC 8781) and DHCP Option 108 (RFC 8925) in my network, I was able to achieve a 100% IPv6 environment.
CLAT/NAT64 is utilized across many mobile networks globally, and I am only talking about Ethernet and Wi-Fi in home and small office/home office (SOHO) environments. I experimented by completely disabling IPv4 at home and established a SSID where my MacBook Pro operates without an actual IPv4 address. The MacBook supports CLAT (RFC 6877), and by implementing PREF64 (RFC 8781) and DHCP Option 108 (RFC 8925) in my network, I was able to achieve a 100% IPv6 environment.
 The FCC lawfully fined U.S. facilities-based wireless carriers nearly $200 million for selling highly intrusive location data about subscribers without their "opt-in" consent. In Section 222 of the Communications Act, Congress comprehensively specified how the carriers bore an affirmative duty of care not to disclose clearly defined Customer Proprietary Information ("CPNI"). The Act explicitly required the FCC, and no other agency, to protect telecommunications consumers.
The FCC lawfully fined U.S. facilities-based wireless carriers nearly $200 million for selling highly intrusive location data about subscribers without their "opt-in" consent. In Section 222 of the Communications Act, Congress comprehensively specified how the carriers bore an affirmative duty of care not to disclose clearly defined Customer Proprietary Information ("CPNI"). The Act explicitly required the FCC, and no other agency, to protect telecommunications consumers.
 Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin.
 An IPv4 address identifies your connection to the online world. IP addresses make it possible to host websites, manage secure communication, and engage in countless other essential, internet-related activities. Typically, when migrating to a new cloud provider, a business has only one path: lease the provider's IP addresses. But what if a business already has a block of IP addresses?
An IPv4 address identifies your connection to the online world. IP addresses make it possible to host websites, manage secure communication, and engage in countless other essential, internet-related activities. Typically, when migrating to a new cloud provider, a business has only one path: lease the provider's IP addresses. But what if a business already has a block of IP addresses?
 A new year and a new goat with new conditions, the goat was slowly eaten by jackdaws, and in the end, almost only the frame remained. This was really slow TV for the devastation… You can read more on Wikipedia about the devastating jackdaws and the straw... 36% IPv6 is equal to last year, and I had high hopes as Telia (AS3301) has made great progress in IPv6 and that Sweden should be the dominant country.
A new year and a new goat with new conditions, the goat was slowly eaten by jackdaws, and in the end, almost only the frame remained. This was really slow TV for the devastation… You can read more on Wikipedia about the devastating jackdaws and the straw... 36% IPv6 is equal to last year, and I had high hopes as Telia (AS3301) has made great progress in IPv6 and that Sweden should be the dominant country.
 There was a somewhat unfortunate outage for a major communications service provider in Australia, Optus, in mid-November. It appears that one of their peer Border Gateway Protocol (BGP) networks mistakenly advertised a very large route collection to the Optus BGP network, which caused the routers to malfunction in some manner.
There was a somewhat unfortunate outage for a major communications service provider in Australia, Optus, in mid-November. It appears that one of their peer Border Gateway Protocol (BGP) networks mistakenly advertised a very large route collection to the Optus BGP network, which caused the routers to malfunction in some manner.
 Trust is such a difficult concept in any context, and certainly, computer networks are no exception. How can you be assured that your network infrastructure is running on authentic platforms, both hardware and software and its operation has not been compromised in any way?
Trust is such a difficult concept in any context, and certainly, computer networks are no exception. How can you be assured that your network infrastructure is running on authentic platforms, both hardware and software and its operation has not been compromised in any way?
 A few years ago, there were a lot of predictions that we'd see broadband networks converting to quantum technology because of the enhanced security. As happens with many new technologies, quantum computing is advancing at a slower pace than the wild predictions that accompanied the launch of the new technology.
A few years ago, there were a lot of predictions that we'd see broadband networks converting to quantum technology because of the enhanced security. As happens with many new technologies, quantum computing is advancing at a slower pace than the wild predictions that accompanied the launch of the new technology.
 The Uptime Institute (UI) is an IT industry research firm best known for certifying that data centers meet industry standards. UI issues an annual report that analyzes the cause of data center outages. The causes for data center outages are relevant to the broadband industry because the same kinds of issues shut down switching hubs and Network Operations Centers.
The Uptime Institute (UI) is an IT industry research firm best known for certifying that data centers meet industry standards. UI issues an annual report that analyzes the cause of data center outages. The causes for data center outages are relevant to the broadband industry because the same kinds of issues shut down switching hubs and Network Operations Centers.
 Interested in learning more about routing security? How it can affect your connectivity supply chain? What are best practices for enterprises and organizations? What is the role of CSIRTs in securing routing? What are governments doing now, and planning to do in the future around routing security?
Interested in learning more about routing security? How it can affect your connectivity supply chain? What are best practices for enterprises and organizations? What is the role of CSIRTs in securing routing? What are governments doing now, and planning to do in the future around routing security?
 Internet Visionaries Honored with Postel Service Award
Internet Visionaries Honored with Postel Service Award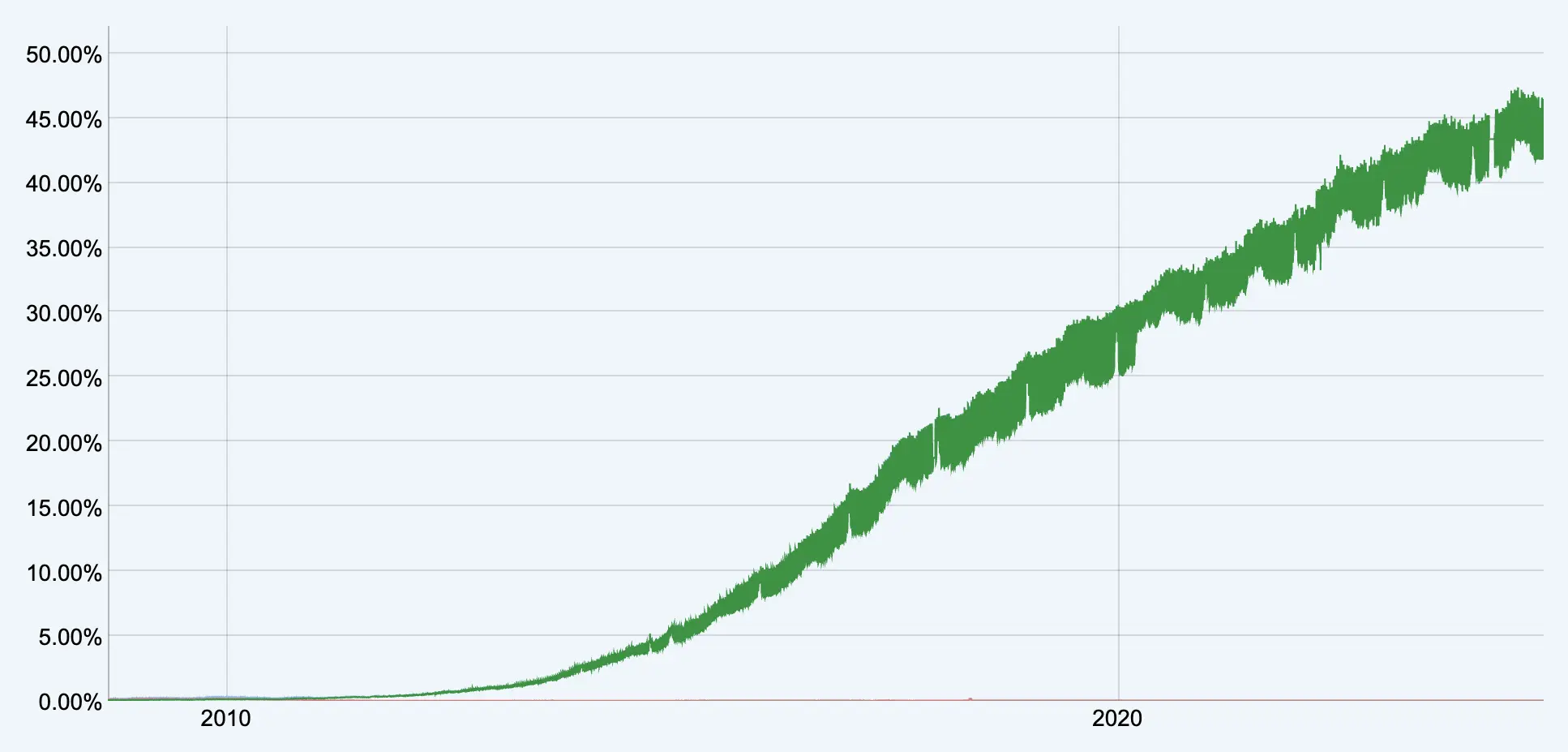 IPv6 Transition Stalls as Internet Moves Beyond IP Addresses
IPv6 Transition Stalls as Internet Moves Beyond IP Addresses Global IT Outage Disrupts Airlines, Businesses, and Hospitals
Global IT Outage Disrupts Airlines, Businesses, and Hospitals Vint Cerf Receives IEEE Medal of Honor
Vint Cerf Receives IEEE Medal of Honor