

 Tech developments saw less drama than trade and environmental shifts during Trump's first 100 days. Continuity, not abrupt change, defined his approach to AI and digital regulation. Only 9 of 139 executive orders (EOs) focused on tech. Trump's tech policy emphasised reviews and incremental shifts. Public consultations on AI, cybersecurity, and cryptocurrencies signal steady evolution over upheaval.
Tech developments saw less drama than trade and environmental shifts during Trump's first 100 days. Continuity, not abrupt change, defined his approach to AI and digital regulation. Only 9 of 139 executive orders (EOs) focused on tech. Trump's tech policy emphasised reviews and incremental shifts. Public consultations on AI, cybersecurity, and cryptocurrencies signal steady evolution over upheaval.
 Sometime by year-end, the UN General Assembly (UNGA) will vote on the proposed UN Convention Against Cybercrime. The treaty is opposed by most civil liberties organizations and Internet businesses, although the US position appears uncertain, mostly for reasons of foreign policy.
Sometime by year-end, the UN General Assembly (UNGA) will vote on the proposed UN Convention Against Cybercrime. The treaty is opposed by most civil liberties organizations and Internet businesses, although the US position appears uncertain, mostly for reasons of foreign policy.
 Cybersecurity and artificial intelligence were among the key topics at the 79th UN General Assembly (UNGA). UNGA's 1st Committee, responsible for disarmament and international security, concluded its negotiations in mid-November 2024. It discussed the 3rd Annual Progress Report (APR) of the Open-Ended Working Group (OEWG) and adopted a resolution that recommends, inter alia, the establishment of a new permanent cybersecurity mechanism within the UN system. Furthermore, it adopted two resolutions on autonomous weapon systems (AWS).
Cybersecurity and artificial intelligence were among the key topics at the 79th UN General Assembly (UNGA). UNGA's 1st Committee, responsible for disarmament and international security, concluded its negotiations in mid-November 2024. It discussed the 3rd Annual Progress Report (APR) of the Open-Ended Working Group (OEWG) and adopted a resolution that recommends, inter alia, the establishment of a new permanent cybersecurity mechanism within the UN system. Furthermore, it adopted two resolutions on autonomous weapon systems (AWS).
 In CSC's recent insight paper, we address the trend that many business leaders today don't realize the extent to which their modern enterprise -- and its millions of digital assets -- rely on. It's a vast domain ecosystem that needs to be protected from online threats. Often, to better understand this need for domain security, we need to understand how critical and interconnected domains are within a business.
In CSC's recent insight paper, we address the trend that many business leaders today don't realize the extent to which their modern enterprise -- and its millions of digital assets -- rely on. It's a vast domain ecosystem that needs to be protected from online threats. Often, to better understand this need for domain security, we need to understand how critical and interconnected domains are within a business.
 Despite global polarization, recent UN cyber diplomacy has achieved three significant agreements in 2024: a cyber attack reporting system, a convention against cybercrime, and a "Global Digital Compact." These successes show that consensus on global issues is possible, though the vague wording of agreements raises concerns about their long-term effectiveness in ensuring security and peace.
Despite global polarization, recent UN cyber diplomacy has achieved three significant agreements in 2024: a cyber attack reporting system, a convention against cybercrime, and a "Global Digital Compact." These successes show that consensus on global issues is possible, though the vague wording of agreements raises concerns about their long-term effectiveness in ensuring security and peace.
 Interisle Consulting Group today released its fourth annual Phishing Landscape report investigating where and how cybercriminals acquire naming and hosting resources for phishing. Our study shows that cybercriminals evolved their tactics for obtaining attack resources, including sharply increasing their exploitation of subdomain and gateway providers.
Interisle Consulting Group today released its fourth annual Phishing Landscape report investigating where and how cybercriminals acquire naming and hosting resources for phishing. Our study shows that cybercriminals evolved their tactics for obtaining attack resources, including sharply increasing their exploitation of subdomain and gateway providers.
 I recently appeared on the 419 Consulting podcast to discuss the European Union's NIS 2.0 Directive and its impact on the domain name ecosystem. I encourage all TLD registries, domain name registration service providers, and DNS operators to listen to the recording of that session which Andrew Campling has made available.
I recently appeared on the 419 Consulting podcast to discuss the European Union's NIS 2.0 Directive and its impact on the domain name ecosystem. I encourage all TLD registries, domain name registration service providers, and DNS operators to listen to the recording of that session which Andrew Campling has made available.
 The Internet Watch Foundation (IWF) leads the charge to combat child sexual abuse material (CSAM) online, and we at Public Interest Registry (PIR) are dedicated to supporting their efforts. We are honored to work with them across two important programs: Domain Alerts and TLD Hopping List. IWF services have been extremely successful in addressing CSAM on .ORG over the past five years
The Internet Watch Foundation (IWF) leads the charge to combat child sexual abuse material (CSAM) online, and we at Public Interest Registry (PIR) are dedicated to supporting their efforts. We are honored to work with them across two important programs: Domain Alerts and TLD Hopping List. IWF services have been extremely successful in addressing CSAM on .ORG over the past five years
 In two weeks, final negotiations will begin on the UN's proposed Cybercrime Convention, a document which has elicited widespread concern from civil society, industry groups, and some states due to the serious risks it poses to human rights, including privacy and freedom of expression. Since 2022, GPD and other groups, including EFF, Human Rights Watch and Privacy International, have sought to alert stakeholders within the process to the need for substantial revisions...
In two weeks, final negotiations will begin on the UN's proposed Cybercrime Convention, a document which has elicited widespread concern from civil society, industry groups, and some states due to the serious risks it poses to human rights, including privacy and freedom of expression. Since 2022, GPD and other groups, including EFF, Human Rights Watch and Privacy International, have sought to alert stakeholders within the process to the need for substantial revisions...
 The 2024 "To-Do-List" for all stakeholders in the global Internet Governance Ecosystem is a very long one. Not only the real world but also the virtual world is in turmoil. Vint Cerf once argued that the Internet is just a mirror of the existing world. If the existing world is in trouble, the Internet world has a problem.
The 2024 "To-Do-List" for all stakeholders in the global Internet Governance Ecosystem is a very long one. Not only the real world but also the virtual world is in turmoil. Vint Cerf once argued that the Internet is just a mirror of the existing world. If the existing world is in trouble, the Internet world has a problem.
 Users are tired of hearing about data breaches that put their sensitive information at risk. Reports show that cybercriminals stole 6.41 million records in the first quarter of 2023 alone. From medical data to passwords and even DNA information, hackers have stolen a lot of sensitive information in 2023.
Users are tired of hearing about data breaches that put their sensitive information at risk. Reports show that cybercriminals stole 6.41 million records in the first quarter of 2023 alone. From medical data to passwords and even DNA information, hackers have stolen a lot of sensitive information in 2023.
 The FCA has been naming and shaming financial scam domains for decades. Its "warning list" is probably one the most extensive databases of its kind. But does it do a good enough job of actually warning people? Let us begin with the FCA website, which would not exactly get full points for user-friendliness: locating the "watch list" is a task in and of itself, to say nothing of consulting and scrutinising it.
The FCA has been naming and shaming financial scam domains for decades. Its "warning list" is probably one the most extensive databases of its kind. But does it do a good enough job of actually warning people? Let us begin with the FCA website, which would not exactly get full points for user-friendliness: locating the "watch list" is a task in and of itself, to say nothing of consulting and scrutinising it.
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology.
 As the brand protection industry approaches a quarter of a century in age, following the founding of pioneers Envisional and MarkMonitor in 1999, I present an overview of some of the main outstanding issues which are frequently unaddressed or are generally only partially solved by brand protection service providers. I term these the 'Millennium Problems' in reference to the set of unsolved mathematical problems published in 2000 by the Clay Mathematics Institute, and for which significant prizes were offered for solutions.
As the brand protection industry approaches a quarter of a century in age, following the founding of pioneers Envisional and MarkMonitor in 1999, I present an overview of some of the main outstanding issues which are frequently unaddressed or are generally only partially solved by brand protection service providers. I term these the 'Millennium Problems' in reference to the set of unsolved mathematical problems published in 2000 by the Clay Mathematics Institute, and for which significant prizes were offered for solutions.
 While threat actors can use any domain across thousands of top-level domains (TLDs), they often have favorites. For instance, you may be familiar with Spamhaus's 10 most-abused TLDs for spamming. WhoisXML API researchers recently built on this list by analyzing 40,000 newly registered domains (NRDs) that sported some of the listed unreputable TLDs. We called this study "DNS Abuse Trends: Dissecting the Domains Under the Most-Abused TLDs."
While threat actors can use any domain across thousands of top-level domains (TLDs), they often have favorites. For instance, you may be familiar with Spamhaus's 10 most-abused TLDs for spamming. WhoisXML API researchers recently built on this list by analyzing 40,000 newly registered domains (NRDs) that sported some of the listed unreputable TLDs. We called this study "DNS Abuse Trends: Dissecting the Domains Under the Most-Abused TLDs."
 Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats
Cyberattacks Spur Boom in Insurance Demand Amid Rising Global Threats India Launches ‘.bank.in’ and ‘.fin.in’ Domains to Deter Financial Fraud
India Launches ‘.bank.in’ and ‘.fin.in’ Domains to Deter Financial Fraud Biden Administration to Back UN Cybercrime Treaty Amid Controversy
Biden Administration to Back UN Cybercrime Treaty Amid Controversy Ransomware Crisis in U.S. Healthcare
Ransomware Crisis in U.S. Healthcare Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation
Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation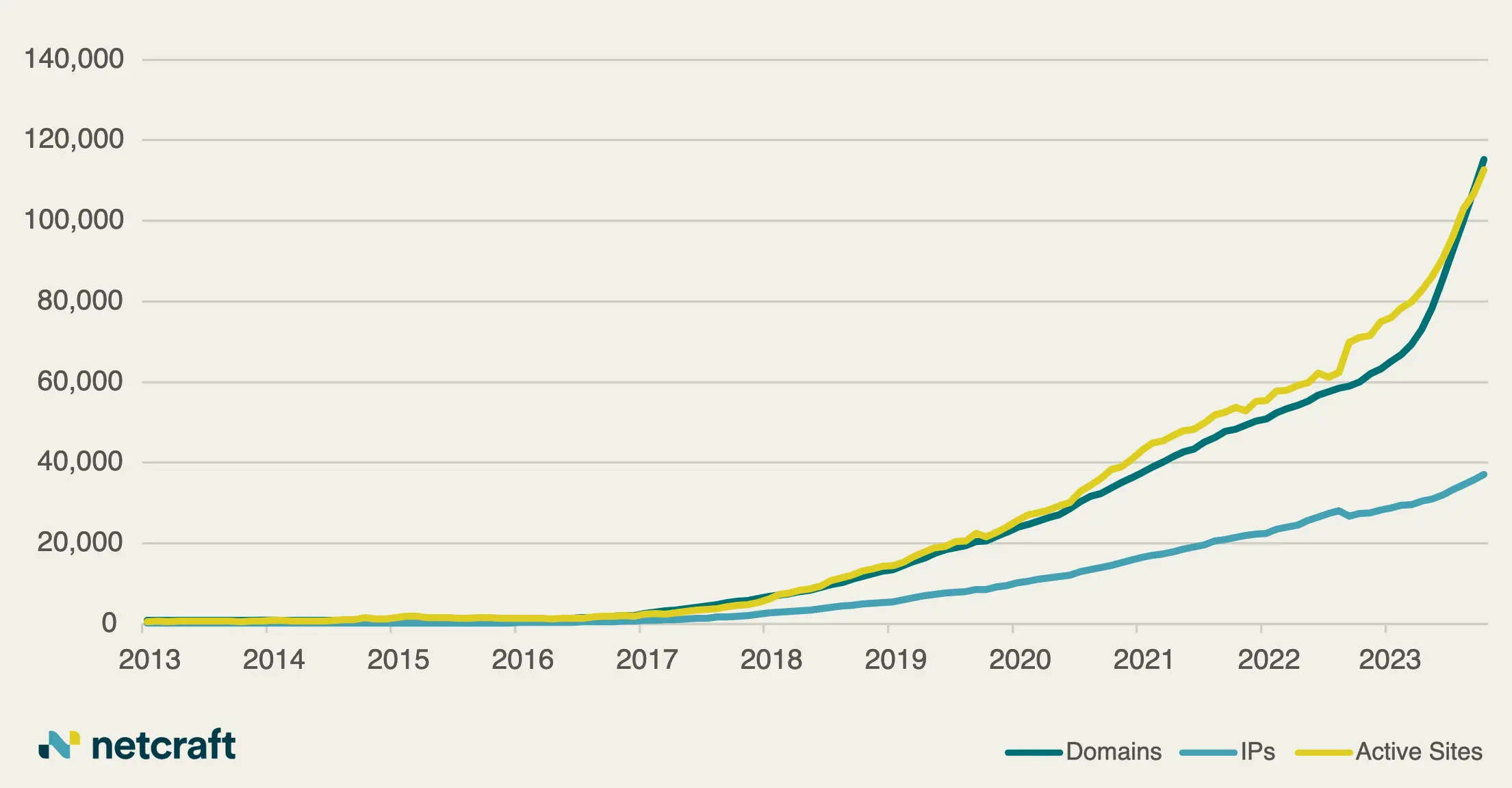 Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space
Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space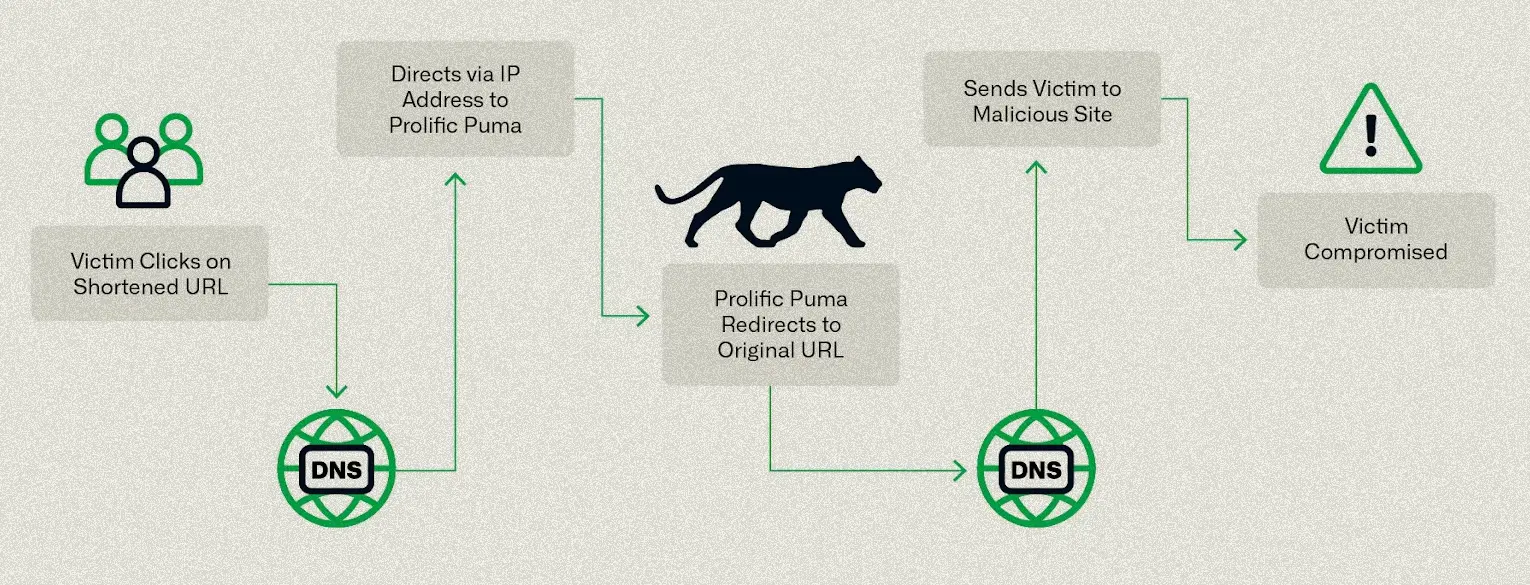 Researchers Uncover Massive Underground Link-Shortening Service Used by Malicious Actors
Researchers Uncover Massive Underground Link-Shortening Service Used by Malicious Actors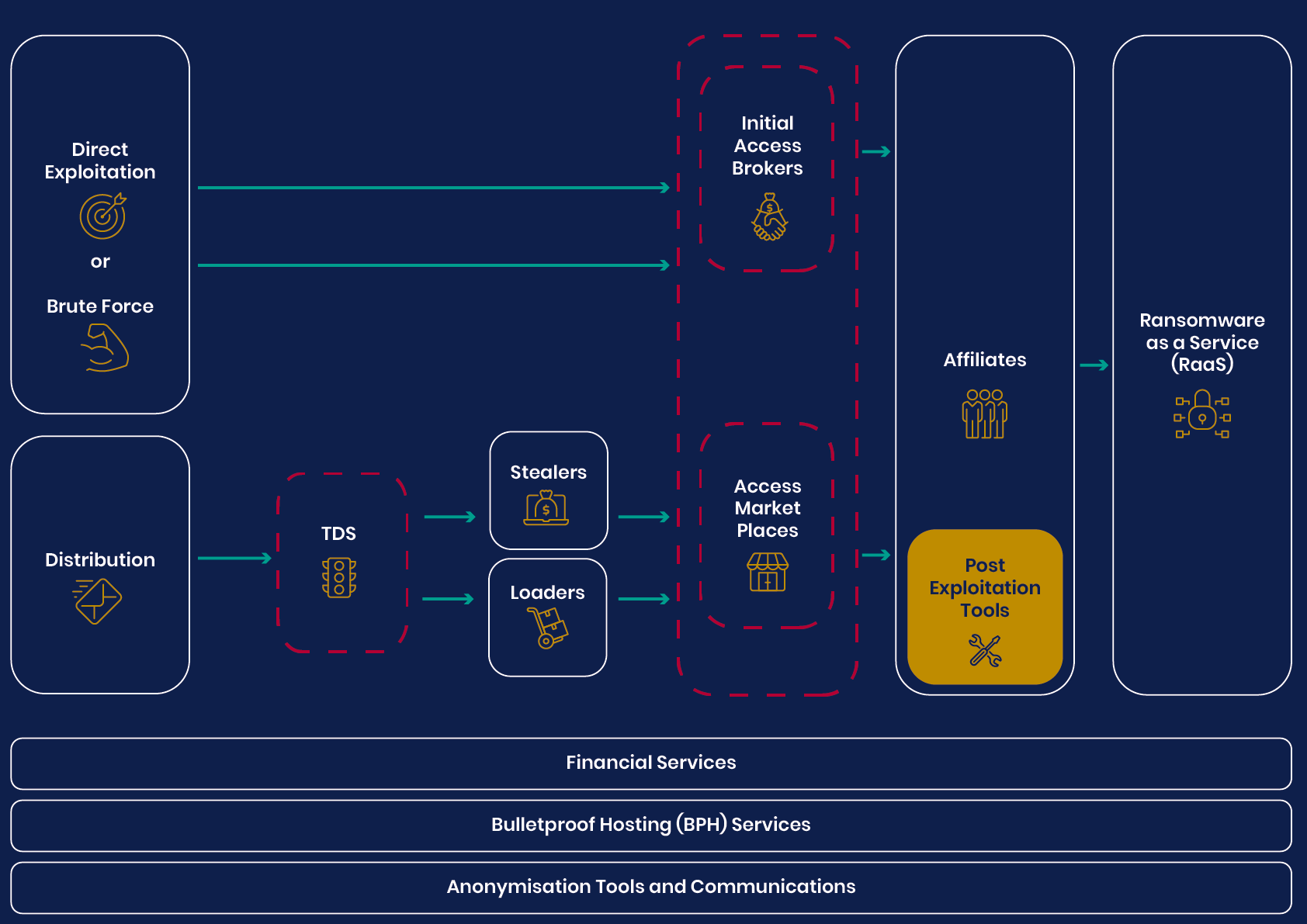 UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem
UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem The Hague to Probe Cyberwarfare Under Existing International Law
The Hague to Probe Cyberwarfare Under Existing International Law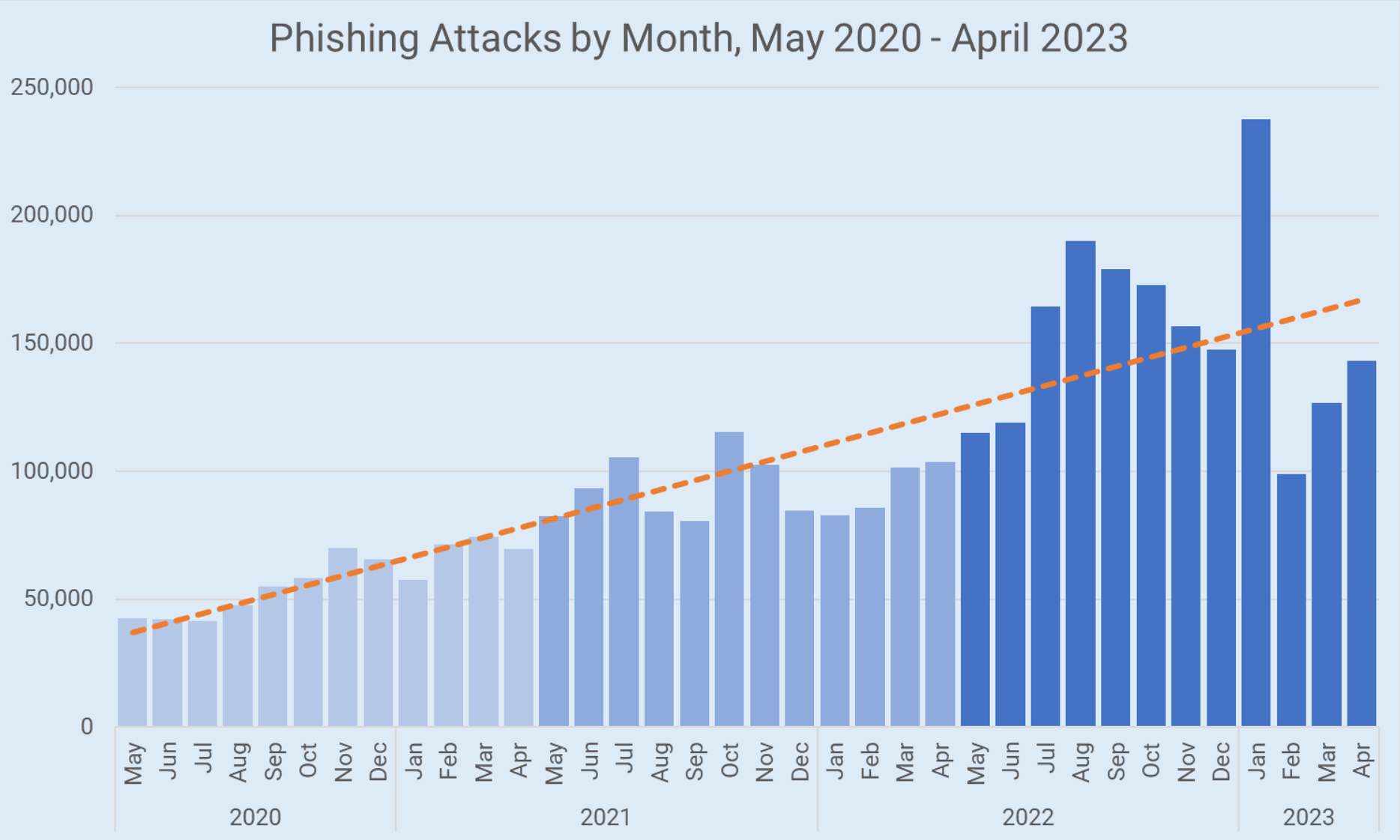 Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed
Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed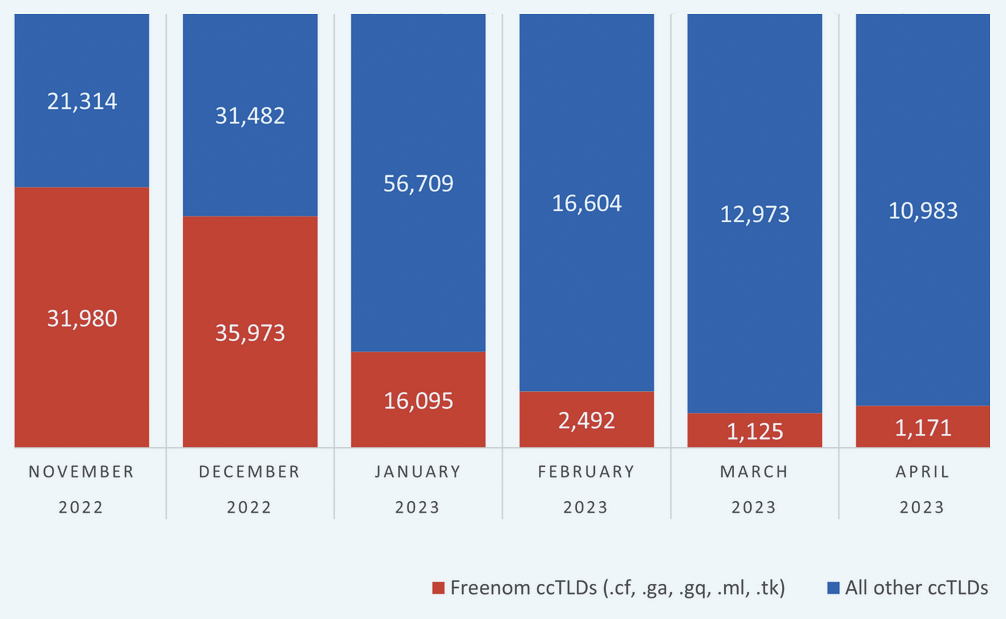 Meta Lawsuit Leads to Significant Decline in Phishing Domains Tied to Freenom
Meta Lawsuit Leads to Significant Decline in Phishing Domains Tied to Freenom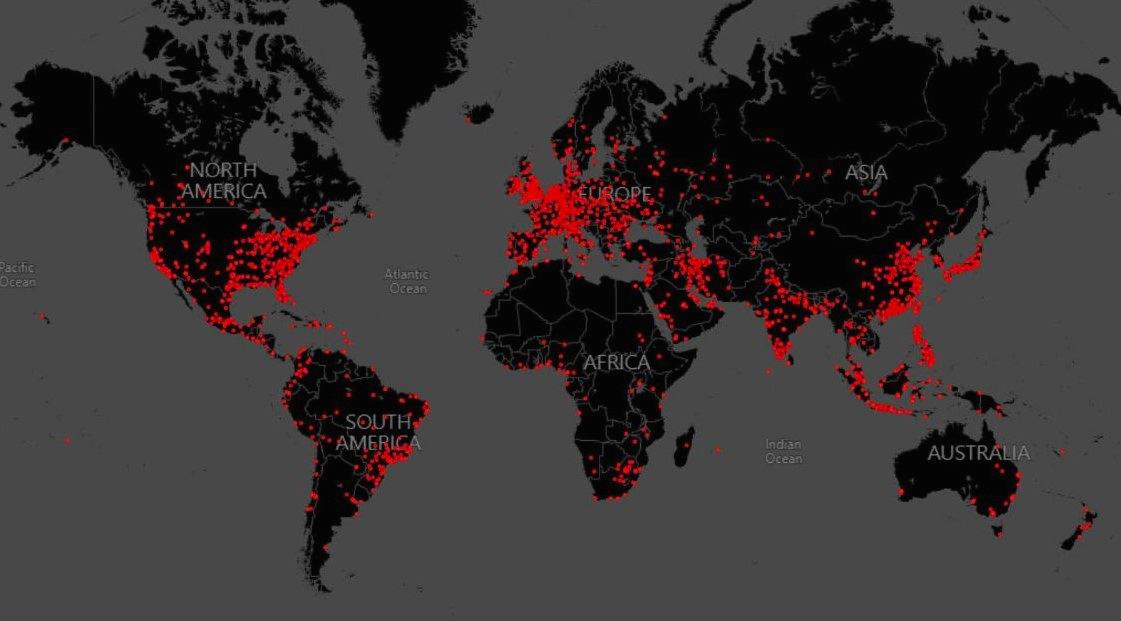 Microsoft, Fortra, and Health-ISAC Take Legal Action Against the Abuse of Cobalt Strike to Combat Ransomware Attacks
Microsoft, Fortra, and Health-ISAC Take Legal Action Against the Abuse of Cobalt Strike to Combat Ransomware Attacks FBI Takes Down ‘Genesis Market’ Cybercrime Store: Dozens Arrested Worldwide
FBI Takes Down ‘Genesis Market’ Cybercrime Store: Dozens Arrested Worldwide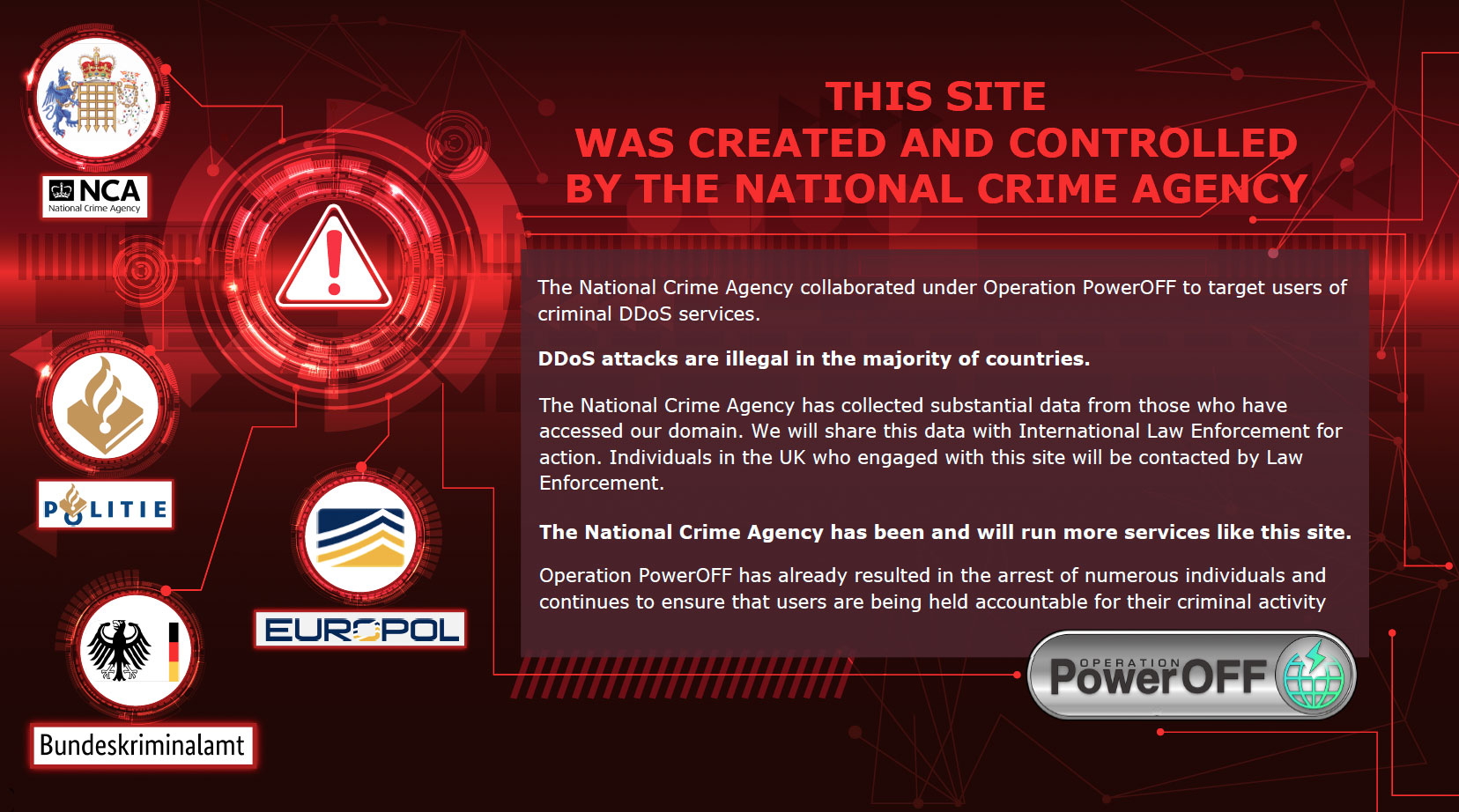 NCA Launches Campaign to Curb DDoS-for-Hire Website Use, Warns of Legal Risks
NCA Launches Campaign to Curb DDoS-for-Hire Website Use, Warns of Legal Risks