

 Despite steady expansion of fibre networks, the cost of building them is rising. New survey data show labour-heavy construction, higher aerial costs and persistent inflation pressures likely to push deployment expenses higher in 2026.
Despite steady expansion of fibre networks, the cost of building them is rising. New survey data show labour-heavy construction, higher aerial costs and persistent inflation pressures likely to push deployment expenses higher in 2026.
 ICANN's proposed overhaul of root server governance would empower a new council to revoke America's operator status, risking a clash with a resurgent Trump administration and potentially imperiling the multistakeholder model that underpins the internet's core infrastructure.
ICANN's proposed overhaul of root server governance would empower a new council to revoke America's operator status, risking a clash with a resurgent Trump administration and potentially imperiling the multistakeholder model that underpins the internet's core infrastructure.
 A debate over aligning internet and AI governance reveals stark differences in origin, incentives and power. While lessons from ICANN's multi-stakeholder model endure, AI's corporate dominance and geopolitical rivalry demand new, bottom-up approaches.
A debate over aligning internet and AI governance reveals stark differences in origin, incentives and power. While lessons from ICANN's multi-stakeholder model endure, AI's corporate dominance and geopolitical rivalry demand new, bottom-up approaches.
 Generative AI has turned brand impersonation from a nuisance into an industrial-scale threat, eroding trust. As ICANN's 2026 round approaches, DotBrand domains promise a structural fix to spoofing that strategies failed to deliver in 2012.
Generative AI has turned brand impersonation from a nuisance into an industrial-scale threat, eroding trust. As ICANN's 2026 round approaches, DotBrand domains promise a structural fix to spoofing that strategies failed to deliver in 2012.
 An FCC ruling in a dispute between Comcast and Appalachian Power clarifies pole attachment cost rules, but exposes how regulatory delays and uncooperative utilities can slow fiber deployment and raise costs for broadband providers.
An FCC ruling in a dispute between Comcast and Appalachian Power clarifies pole attachment cost rules, but exposes how regulatory delays and uncooperative utilities can slow fiber deployment and raise costs for broadband providers.
 As geopolitical tensions expose the fragility of subsea cables, Low Earth Orbit satellites and the QUIC protocol promise a more resilient internet by diversifying routes, preserving session continuity, and redefining control over global data flows.
As geopolitical tensions expose the fragility of subsea cables, Low Earth Orbit satellites and the QUIC protocol promise a more resilient internet by diversifying routes, preserving session continuity, and redefining control over global data flows.
 India's AI summit promised a Global South rethink of digital governance. Instead, a weak declaration and Delhi's accession to America's Pax Silica exposed widening power asymmetries, leaving countries like Brazil outside the real circuitry of control.
India's AI summit promised a Global South rethink of digital governance. Instead, a weak declaration and Delhi's accession to America's Pax Silica exposed widening power asymmetries, leaving countries like Brazil outside the real circuitry of control.
 At Munich's twin security gatherings, leaders warned that cyber conflict, transatlantic rifts and weaponised AI are pushing the rules-based order into a perilous transition, where deterrence falters, norms erode and digital sovereignty trumps multistakeholder ideals.
At Munich's twin security gatherings, leaders warned that cyber conflict, transatlantic rifts and weaponised AI are pushing the rules-based order into a perilous transition, where deterrence falters, norms erode and digital sovereignty trumps multistakeholder ideals.
 Project Jake invites global DNS stakeholders to test JADDAR, a privacy-respecting framework for secure access to registration data, aiming to reduce regulatory fragmentation and modernise domain governance through collaborative, policy-aligned engineering solutions.
Project Jake invites global DNS stakeholders to test JADDAR, a privacy-respecting framework for secure access to registration data, aiming to reduce regulatory fragmentation and modernise domain governance through collaborative, policy-aligned engineering solutions.
A three-decade natural experiment suggests America's centralized regulatory review fostered far greater wealth creation than Europe's precautionary principle, raising stark questions about whether importing EU-style AI rules would undermine US innovation and prosperity.
 As the 2026 gTLD round opens, applicants face an overlooked geopolitical hazard: what happens if the registry or RIR underpinning their domain collapses under sanctions or war, leaving contracts stranded and accountability elusive.
As the 2026 gTLD round opens, applicants face an overlooked geopolitical hazard: what happens if the registry or RIR underpinning their domain collapses under sanctions or war, leaving contracts stranded and accountability elusive.
As policymakers search for an IAEA for AI, lessons from ICANN and internet governance loom large, raising questions about multistakeholder legitimacy, mission creep, technical fragmentation and whether AI demands sector-specific regulation rather than grand global architectures.
 At NANOG 96, the AI boom dominated discussions as firms race to build gigawatt-scale data centres packed with advanced GPUs, liquid cooling, and lossless networks, raising fears of overinvestment, neglected security priorities, and a looming infrastructure bubble.
At NANOG 96, the AI boom dominated discussions as firms race to build gigawatt-scale data centres packed with advanced GPUs, liquid cooling, and lossless networks, raising fears of overinvestment, neglected security priorities, and a looming infrastructure bubble.
 America has declared its intent to win the 6G race, casting next-generation wireless as vital to security and growth. Yet standards are global, vendors multinational, and the rhetoric looks like spectrum lobbying than technological rivalry.
America has declared its intent to win the 6G race, casting next-generation wireless as vital to security and growth. Yet standards are global, vendors multinational, and the rhetoric looks like spectrum lobbying than technological rivalry.
 Under ICANN's ICP-2 framework, RIR emergency operations extend beyond technical redundancy to encompass legal relocation, policy divergence and geopolitical risk, exposing tensions between operational resilience and national sovereignty in safeguarding global internet governance.
Under ICANN's ICP-2 framework, RIR emergency operations extend beyond technical redundancy to encompass legal relocation, policy divergence and geopolitical risk, exposing tensions between operational resilience and national sovereignty in safeguarding global internet governance.
 Iranians Outsmart Internet Blackout to Broadcast Airstrikes
Iranians Outsmart Internet Blackout to Broadcast Airstrikes Iran Expands Digital Dragnet After Crushing Protests
Iran Expands Digital Dragnet After Crushing Protests David J. Farber, Early Architect of the Internet, Dies at 91
David J. Farber, Early Architect of the Internet, Dies at 91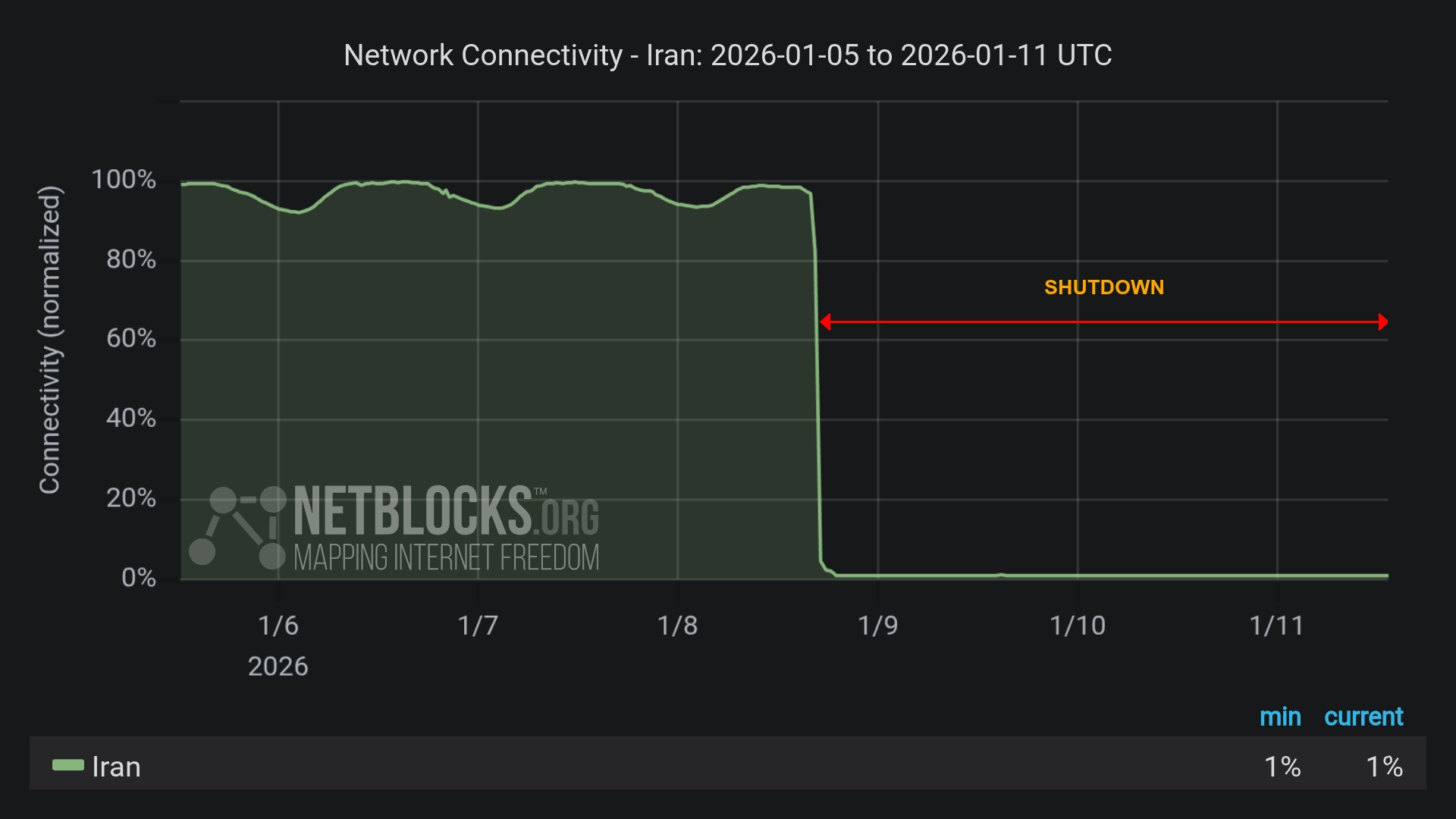 Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests
Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests US Senators Move to Shield Undersea Internet Cables from Global Threats
US Senators Move to Shield Undersea Internet Cables from Global Threats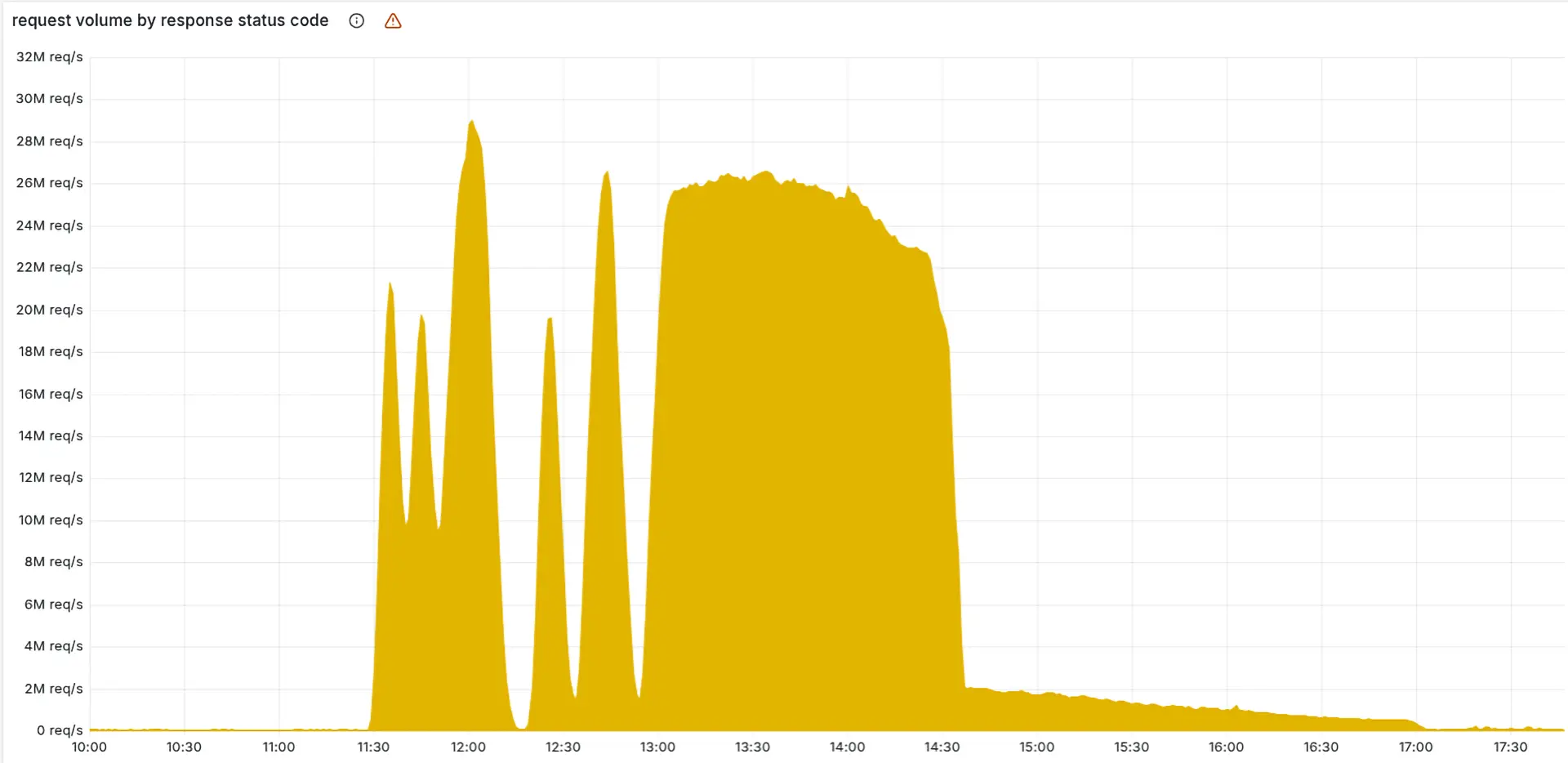 Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem
Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem Cloudflare Outage Highlights Internet’s Growing Single Points of Failure
Cloudflare Outage Highlights Internet’s Growing Single Points of Failure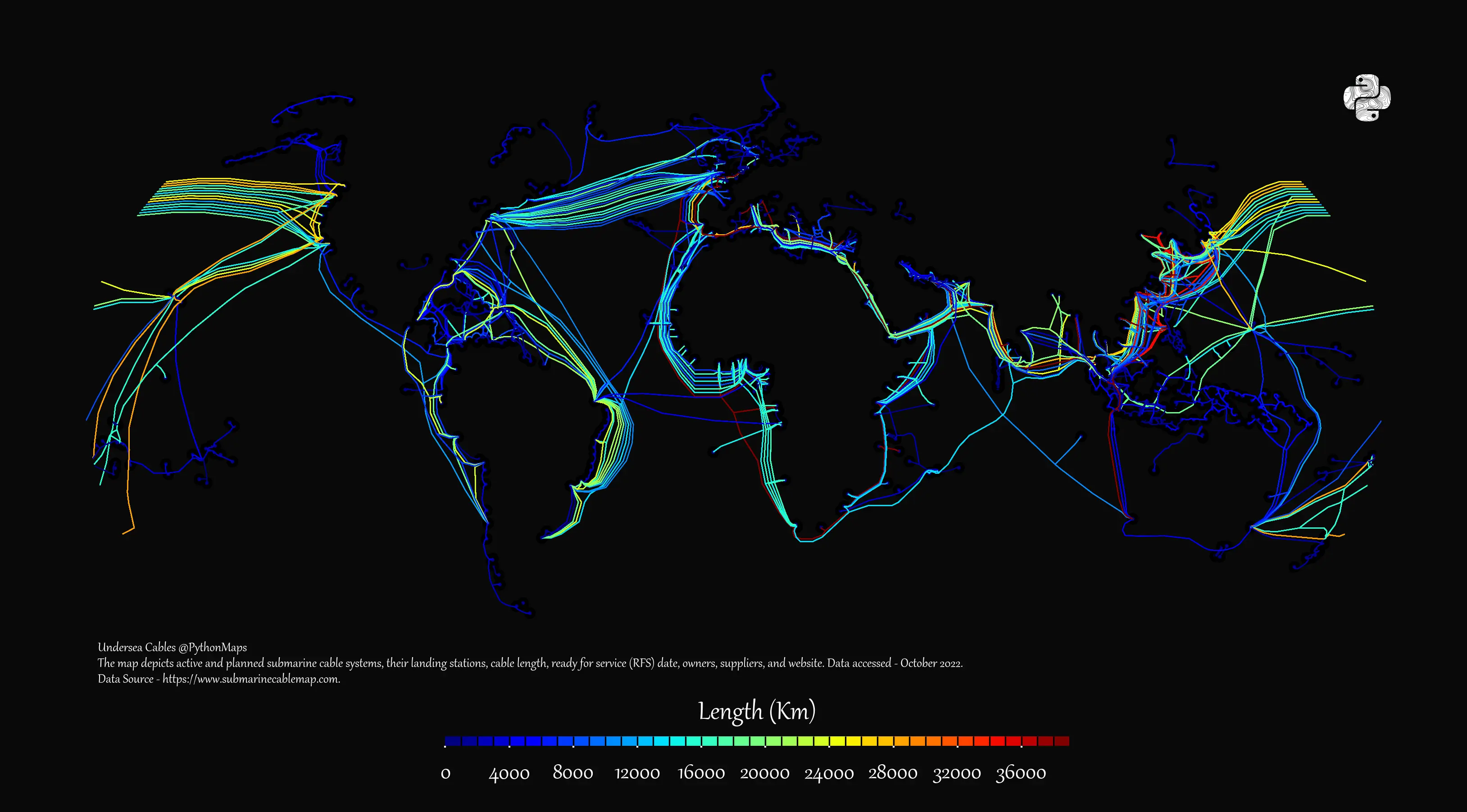 AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns
AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns Verizon and AWS Expand Network Ties to Meet AI Data Demands
Verizon and AWS Expand Network Ties to Meet AI Data Demands