

A three-decade natural experiment suggests America's centralized regulatory review fostered far greater wealth creation than Europe's precautionary principle, raising stark questions about whether importing EU-style AI rules would undermine US innovation and prosperity.
 As the 2026 gTLD round opens, applicants face an overlooked geopolitical hazard: what happens if the registry or RIR underpinning their domain collapses under sanctions or war, leaving contracts stranded and accountability elusive.
As the 2026 gTLD round opens, applicants face an overlooked geopolitical hazard: what happens if the registry or RIR underpinning their domain collapses under sanctions or war, leaving contracts stranded and accountability elusive.
As policymakers search for an IAEA for AI, lessons from ICANN and internet governance loom large, raising questions about multistakeholder legitimacy, mission creep, technical fragmentation and whether AI demands sector-specific regulation rather than grand global architectures.
 At NANOG 96, the AI boom dominated discussions as firms race to build gigawatt-scale data centres packed with advanced GPUs, liquid cooling, and lossless networks, raising fears of overinvestment, neglected security priorities, and a looming infrastructure bubble.
At NANOG 96, the AI boom dominated discussions as firms race to build gigawatt-scale data centres packed with advanced GPUs, liquid cooling, and lossless networks, raising fears of overinvestment, neglected security priorities, and a looming infrastructure bubble.
 America has declared its intent to win the 6G race, casting next-generation wireless as vital to security and growth. Yet standards are global, vendors multinational, and the rhetoric looks like spectrum lobbying than technological rivalry.
America has declared its intent to win the 6G race, casting next-generation wireless as vital to security and growth. Yet standards are global, vendors multinational, and the rhetoric looks like spectrum lobbying than technological rivalry.
 Under ICANN's ICP-2 framework, RIR emergency operations extend beyond technical redundancy to encompass legal relocation, policy divergence and geopolitical risk, exposing tensions between operational resilience and national sovereignty in safeguarding global internet governance.
Under ICANN's ICP-2 framework, RIR emergency operations extend beyond technical redundancy to encompass legal relocation, policy divergence and geopolitical risk, exposing tensions between operational resilience and national sovereignty in safeguarding global internet governance.
 Pew Research finds most Americans are online, yet access still tracks income, age and geography. Broadband gaps persist as subsidies fade, while smartphone dependence rises, reshaping how millions connect to work, services and civic life.
Pew Research finds most Americans are online, yet access still tracks income, age and geography. Broadband gaps persist as subsidies fade, while smartphone dependence rises, reshaping how millions connect to work, services and civic life.
 A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
A six year study of Global 2000 firms finds progress on email authentication but worrying gaps elsewhere. Despite rising DMARC adoption, falling DNS redundancy and uneven regional uptake leave companies exposed to domain based attacks.
 In February 1996, a libertarian myth of cyberspace and sweeping US platform immunity collided, hardwiring digital exceptionalism. Three decades on, that original sin still shields tech and AI from accountability, with legal and social consequences.
In February 1996, a libertarian myth of cyberspace and sweeping US platform immunity collided, hardwiring digital exceptionalism. Three decades on, that original sin still shields tech and AI from accountability, with legal and social consequences.
 SpaceX has filed a plan to place more than a million satellites in low Earth orbit, recasting data centres as spaceborne infrastructure while testing regulators, safety, competition and the line between vision and paper ambition.
SpaceX has filed a plan to place more than a million satellites in low Earth orbit, recasting data centres as spaceborne infrastructure while testing regulators, safety, competition and the line between vision and paper ambition.
 Iran's 2026 internet shutdown was not a glitch but a trial of digital sovereignty, revealing how easily connectivity can be weaponised to silence society, concentrate state power, and fracture the promise of a global internet.
Iran's 2026 internet shutdown was not a glitch but a trial of digital sovereignty, revealing how easily connectivity can be weaponised to silence society, concentrate state power, and fracture the promise of a global internet.
 Predictions of IPv4's demise were premature. A market webinar shows demand has diversified, prices reflect structure not relevance, and leasing, policy shifts and broadband funding will keep the ageing protocol strategically important for years ahead.
Predictions of IPv4's demise were premature. A market webinar shows demand has diversified, prices reflect structure not relevance, and leasing, policy shifts and broadband funding will keep the ageing protocol strategically important for years ahead.
 Meltnet envisions a federated internet model led by BRICS nations, combining digital sovereignty with cross-border interoperability. It challenges US-centric governance by proposing a trust-based architecture rooted in shared standards and mutual recognition.
Meltnet envisions a federated internet model led by BRICS nations, combining digital sovereignty with cross-border interoperability. It challenges US-centric governance by proposing a trust-based architecture rooted in shared standards and mutual recognition.
 Starlink is leveraging its growing dominance with data-hungry AI ambitions, regulatory demands, and space infrastructure plans. A merger with xAI could solidify its position as an unregulated gatekeeper of orbital connectivity and intelligence.
Starlink is leveraging its growing dominance with data-hungry AI ambitions, regulatory demands, and space infrastructure plans. A merger with xAI could solidify its position as an unregulated gatekeeper of orbital connectivity and intelligence.
 With the NIS2 Directive now in effect, a new annex to ICANN contracts offers registries and registrars a practical, flexible path to Article 28 compliance. Early adoption has drawn international praise.
With the NIS2 Directive now in effect, a new annex to ICANN contracts offers registries and registrars a practical, flexible path to Article 28 compliance. Early adoption has drawn international praise.
 Iran Expands Digital Dragnet After Crushing Protests
Iran Expands Digital Dragnet After Crushing Protests David J. Farber, Early Architect of the Internet, Dies at 91
David J. Farber, Early Architect of the Internet, Dies at 91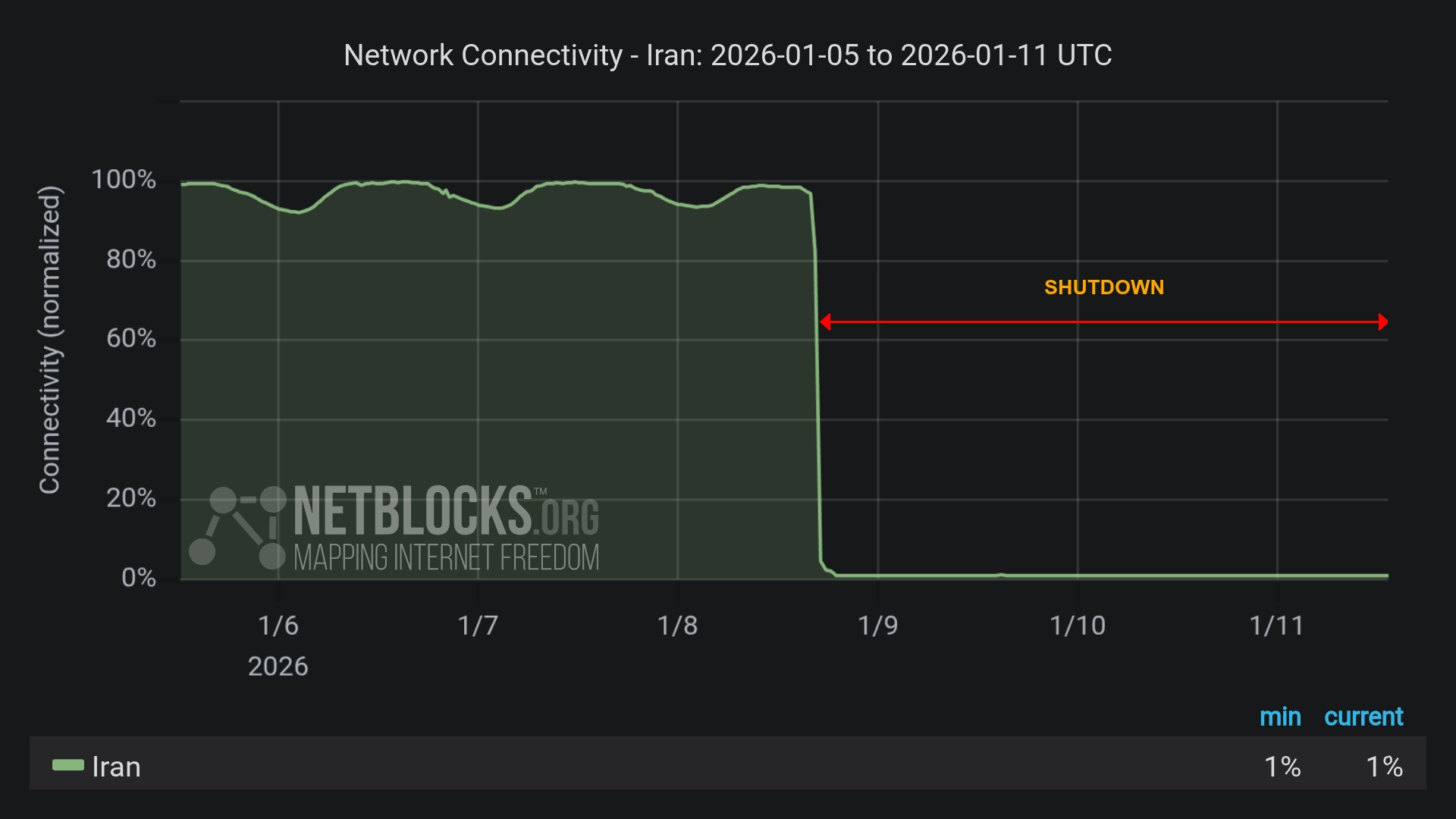 Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests
Iran Cuts Off Internet Nationwide as Regime Disrupts Even Starlink Amid Expanding Protests US Senators Move to Shield Undersea Internet Cables from Global Threats
US Senators Move to Shield Undersea Internet Cables from Global Threats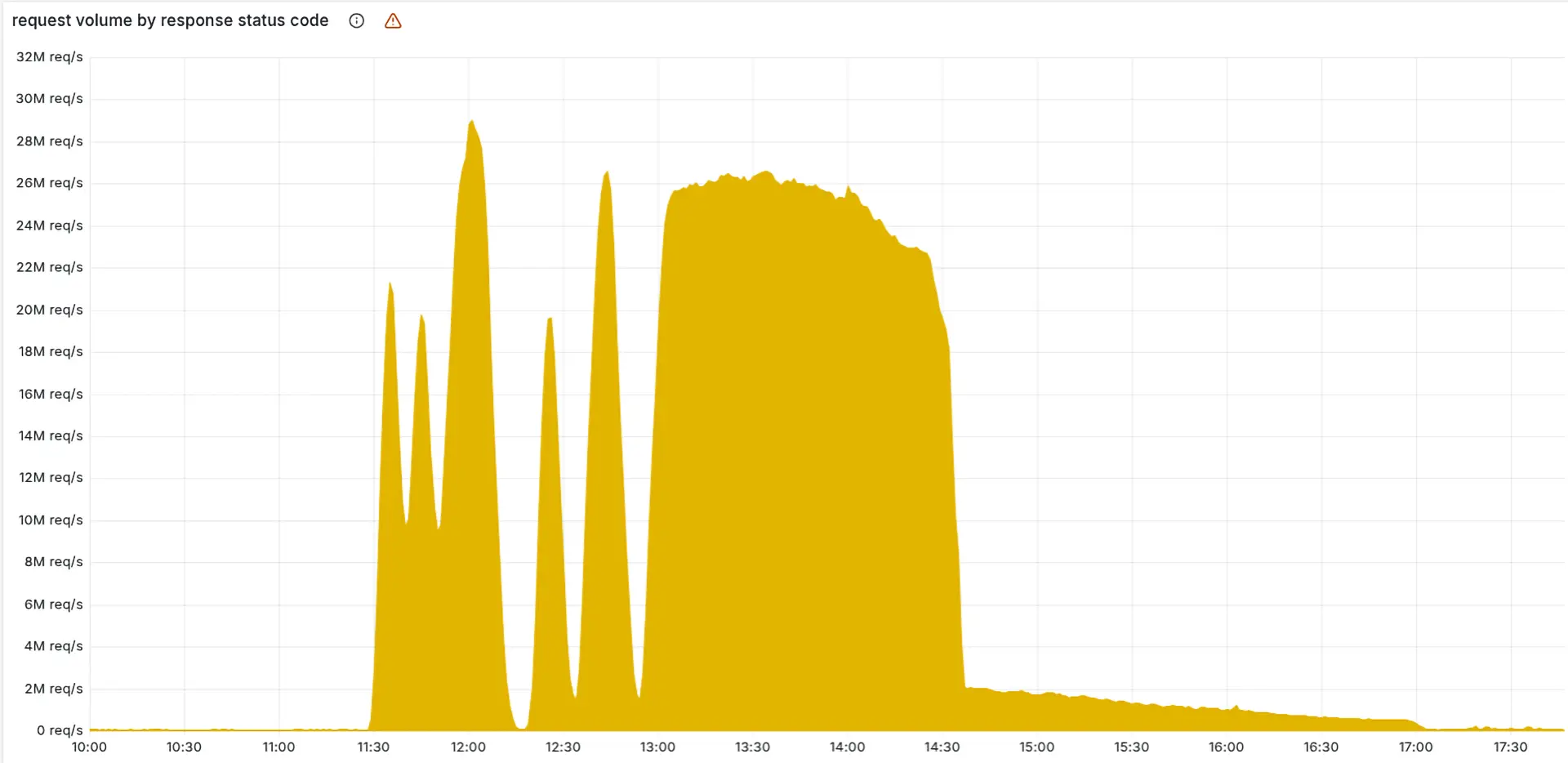 Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem
Configuration Chaos: Cloudflare Explains Major Outage in Detailed Post-Mortem Cloudflare Outage Highlights Internet’s Growing Single Points of Failure
Cloudflare Outage Highlights Internet’s Growing Single Points of Failure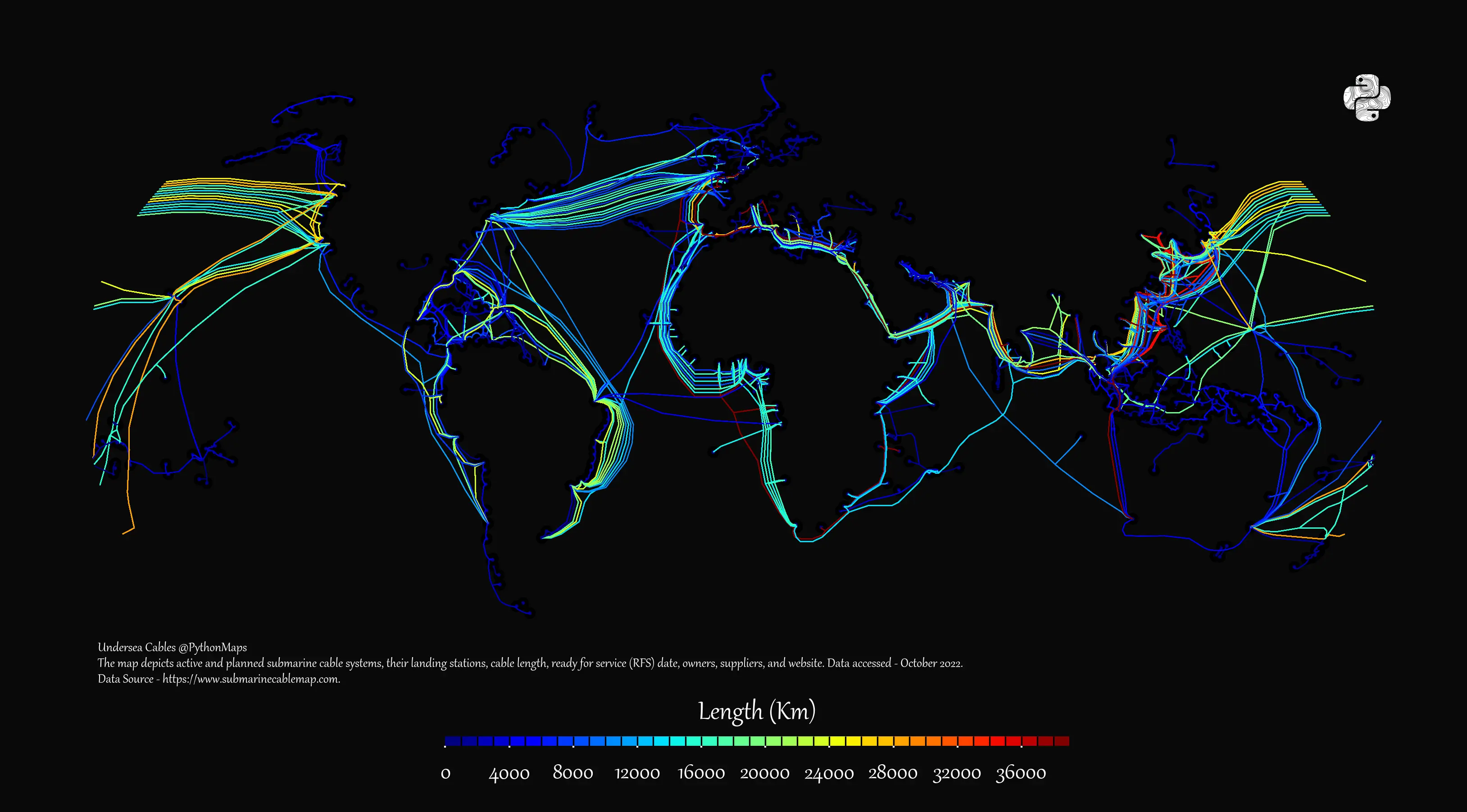 AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns
AI Boom Spurs Record Investment in Undersea Cables Amid Geopolitical and Security Concerns Verizon and AWS Expand Network Ties to Meet AI Data Demands
Verizon and AWS Expand Network Ties to Meet AI Data Demands