
Cybersecurity |
Sponsored by |

|
 As a member of the ROW Planning Committee, I am writing this post on behalf of the Committee and welcome all community members to join us on June 4th. We are celebrating ROW's 10th anniversary! A decade of collaboration and inspiration! Thank you to the incredible community that has fueled this journey! more
As a member of the ROW Planning Committee, I am writing this post on behalf of the Committee and welcome all community members to join us on June 4th. We are celebrating ROW's 10th anniversary! A decade of collaboration and inspiration! Thank you to the incredible community that has fueled this journey! more
 The FCC lawfully fined U.S. facilities-based wireless carriers nearly $200 million for selling highly intrusive location data about subscribers without their "opt-in" consent. In Section 222 of the Communications Act, Congress comprehensively specified how the carriers bore an affirmative duty of care not to disclose clearly defined Customer Proprietary Information ("CPNI"). The Act explicitly required the FCC, and no other agency, to protect telecommunications consumers. more
The FCC lawfully fined U.S. facilities-based wireless carriers nearly $200 million for selling highly intrusive location data about subscribers without their "opt-in" consent. In Section 222 of the Communications Act, Congress comprehensively specified how the carriers bore an affirmative duty of care not to disclose clearly defined Customer Proprietary Information ("CPNI"). The Act explicitly required the FCC, and no other agency, to protect telecommunications consumers. more
 On 29 March 2024, an announcement was posted notifying the world that the Open-Source Software (OSS) package "xz-utils," which includes the xz data compression program and a library of software routines called "liblzma" and which is present in most Linux distributions, had been compromised. The insertion of the compromised code was done by "Jia Tan", the official maintainer of the xz-utils package. more
On 29 March 2024, an announcement was posted notifying the world that the Open-Source Software (OSS) package "xz-utils," which includes the xz data compression program and a library of software routines called "liblzma" and which is present in most Linux distributions, had been compromised. The insertion of the compromised code was done by "Jia Tan", the official maintainer of the xz-utils package. more
 Sixty years ago, Paul Baran and Sharla Boehm at The RAND Corporation released a seminal paper that would fundamentally reshape the cyber world forever more. Their paper, simply known as Memorandum RM -- 1303, described how specialized computers could be used to route digital communications among a distributed universe of other computers. It set the stage for a flood of endless developments that resulted in the interconnected world of everything, everywhere, all the time. more
Sixty years ago, Paul Baran and Sharla Boehm at The RAND Corporation released a seminal paper that would fundamentally reshape the cyber world forever more. Their paper, simply known as Memorandum RM -- 1303, described how specialized computers could be used to route digital communications among a distributed universe of other computers. It set the stage for a flood of endless developments that resulted in the interconnected world of everything, everywhere, all the time. more
 Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin. more
Satellites make it possible for governments to provide essential services, such as national defense, navigation, and weather forecasting. Private ventures use satellites to offer highly desired services that include video program distribution, telecommunications, and Internet access. The Russian launch of a satellite, with nuclear power and the likely ability to disable satellites, underscores how satellites are quite vulnerable to both natural and manmade ruin. more
 Last month, the Russian state-sponsored hacking group "Midnight Blizzard" gained access to the email accounts of Microsoft leadership, even exfiltrating documents and messages. The group reportedly used a simple brute-force style attack to access a forgotten test account and then exploited the permissions on that account to access the emails of employees in the cybersecurity and legal teams. more
Last month, the Russian state-sponsored hacking group "Midnight Blizzard" gained access to the email accounts of Microsoft leadership, even exfiltrating documents and messages. The group reportedly used a simple brute-force style attack to access a forgotten test account and then exploited the permissions on that account to access the emails of employees in the cybersecurity and legal teams. more
 This blog post and the associated report aim to provide an overview of DNS Abuse 1related issues the Governmental Advisory Committee (GAC), part of the ICANN multi-stakeholder model, has identified. We also summarize the relevant community activity taking place to address these areas of interest and highlight remaining gaps. From 2016 to June 2023, the GAC referenced four primary categories of activity related to DNS Abuse. more
This blog post and the associated report aim to provide an overview of DNS Abuse 1related issues the Governmental Advisory Committee (GAC), part of the ICANN multi-stakeholder model, has identified. We also summarize the relevant community activity taking place to address these areas of interest and highlight remaining gaps. From 2016 to June 2023, the GAC referenced four primary categories of activity related to DNS Abuse. more
 The 2024 "To-Do-List" for all stakeholders in the global Internet Governance Ecosystem is a very long one. Not only the real world but also the virtual world is in turmoil. Vint Cerf once argued that the Internet is just a mirror of the existing world. If the existing world is in trouble, the Internet world has a problem. more
The 2024 "To-Do-List" for all stakeholders in the global Internet Governance Ecosystem is a very long one. Not only the real world but also the virtual world is in turmoil. Vint Cerf once argued that the Internet is just a mirror of the existing world. If the existing world is in trouble, the Internet world has a problem. more
 Users are tired of hearing about data breaches that put their sensitive information at risk. Reports show that cybercriminals stole 6.41 million records in the first quarter of 2023 alone. From medical data to passwords and even DNA information, hackers have stolen a lot of sensitive information in 2023. more
Users are tired of hearing about data breaches that put their sensitive information at risk. Reports show that cybercriminals stole 6.41 million records in the first quarter of 2023 alone. From medical data to passwords and even DNA information, hackers have stolen a lot of sensitive information in 2023. more
 The quantum computing era is coming, and it will change everything about how the world connects online. While quantum computing will yield tremendous benefits, it will also create new risks, so it's essential that we prepare our critical internet infrastructure for what's to come. That's why we're so pleased to share our latest efforts in this area, including technology that we're making available as an open source implementation to help internet operators worldwide prepare. more
The quantum computing era is coming, and it will change everything about how the world connects online. While quantum computing will yield tremendous benefits, it will also create new risks, so it's essential that we prepare our critical internet infrastructure for what's to come. That's why we're so pleased to share our latest efforts in this area, including technology that we're making available as an open source implementation to help internet operators worldwide prepare. more
 IoT devices have ingrained themselves into almost every aspect of modern life. From home assistants to industrial machinery, it's hard to find a device that isn't connected to a network and gathering data. Despite widespread adoption, IoT cybersecurity compliance remains surprisingly low. A big reason for this is the unique challenges IoT devices pose to operators. more
IoT devices have ingrained themselves into almost every aspect of modern life. From home assistants to industrial machinery, it's hard to find a device that isn't connected to a network and gathering data. Despite widespread adoption, IoT cybersecurity compliance remains surprisingly low. A big reason for this is the unique challenges IoT devices pose to operators. more
 The 78th UN General Assembly (UNGA) addressed the issue of cybersecurity again at one of its last meetings in December 2023. It included the adoption of four resolutions on the Open-Ended Working Group (OEWG), a "Program of Action" (POA), and autonomous weapon systems. The texts of the four draft resolutions were negotiated in UNGA's 1st committee, responsible for international security issues, in October and November 2023. more
The 78th UN General Assembly (UNGA) addressed the issue of cybersecurity again at one of its last meetings in December 2023. It included the adoption of four resolutions on the Open-Ended Working Group (OEWG), a "Program of Action" (POA), and autonomous weapon systems. The texts of the four draft resolutions were negotiated in UNGA's 1st committee, responsible for international security issues, in October and November 2023. more
 The FCA has been naming and shaming financial scam domains for decades. Its "warning list" is probably one the most extensive databases of its kind. But does it do a good enough job of actually warning people? Let us begin with the FCA website, which would not exactly get full points for user-friendliness: locating the "watch list" is a task in and of itself, to say nothing of consulting and scrutinising it. more
The FCA has been naming and shaming financial scam domains for decades. Its "warning list" is probably one the most extensive databases of its kind. But does it do a good enough job of actually warning people? Let us begin with the FCA website, which would not exactly get full points for user-friendliness: locating the "watch list" is a task in and of itself, to say nothing of consulting and scrutinising it. more
 Android users can choose from 3.718 million applications in the Google Play Store. When installing applications, the majority of consumers trust Google to keep their devices safe from hackers. However, the reality is different. Just back in May 2023, researchers discovered over 101 infected applications in the Android store. Many of these apps counted over 400 million downloads. more
Android users can choose from 3.718 million applications in the Google Play Store. When installing applications, the majority of consumers trust Google to keep their devices safe from hackers. However, the reality is different. Just back in May 2023, researchers discovered over 101 infected applications in the Android store. Many of these apps counted over 400 million downloads. more
 From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology. more
From the creation of DNSAI Compass ("Compass"), we knew that measuring DNS Abuse1 would be difficult and that it would be beneficial to anticipate the challenges we would encounter. With more than a year of published reports, we are sharing insights into one of the obstacles we have faced. One of our core principles is transparency and we've worked hard to provide this with our methodology. more
 Biden Administration Alerts Governors to Rising Cyber Threats on U.S. Water Systems
Biden Administration Alerts Governors to Rising Cyber Threats on U.S. Water Systems Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation
Global Law Enforcement Strikes Major Blow Against LockBit Ransomware Operation Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm
Millions of Smart Toothbrushes Hijacked in Cyberattack on Swiss Firm Denmark Encounters Largest Cyber Attack on Its Critical Infrastructure to Date
Denmark Encounters Largest Cyber Attack on Its Critical Infrastructure to Date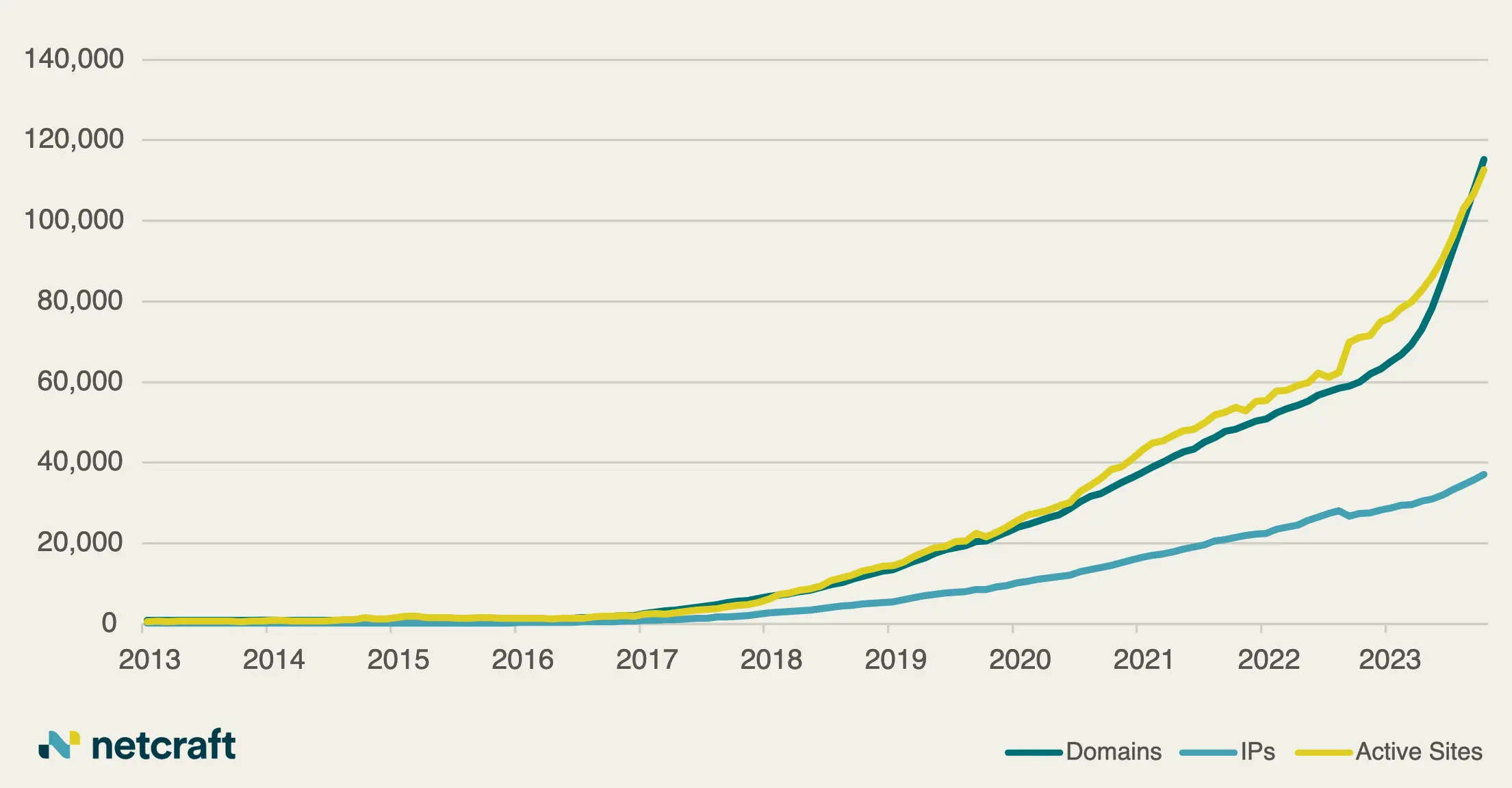 Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space
Rise in Cybercrime Exploiting Artificial Intelligence Hype Leads to Growing Threats Within the .ai Domain Space U.S. National Security Agency Announces AI Security Center
U.S. National Security Agency Announces AI Security Center Online Safety Bill: UK’s Digital Overhaul
Online Safety Bill: UK’s Digital Overhaul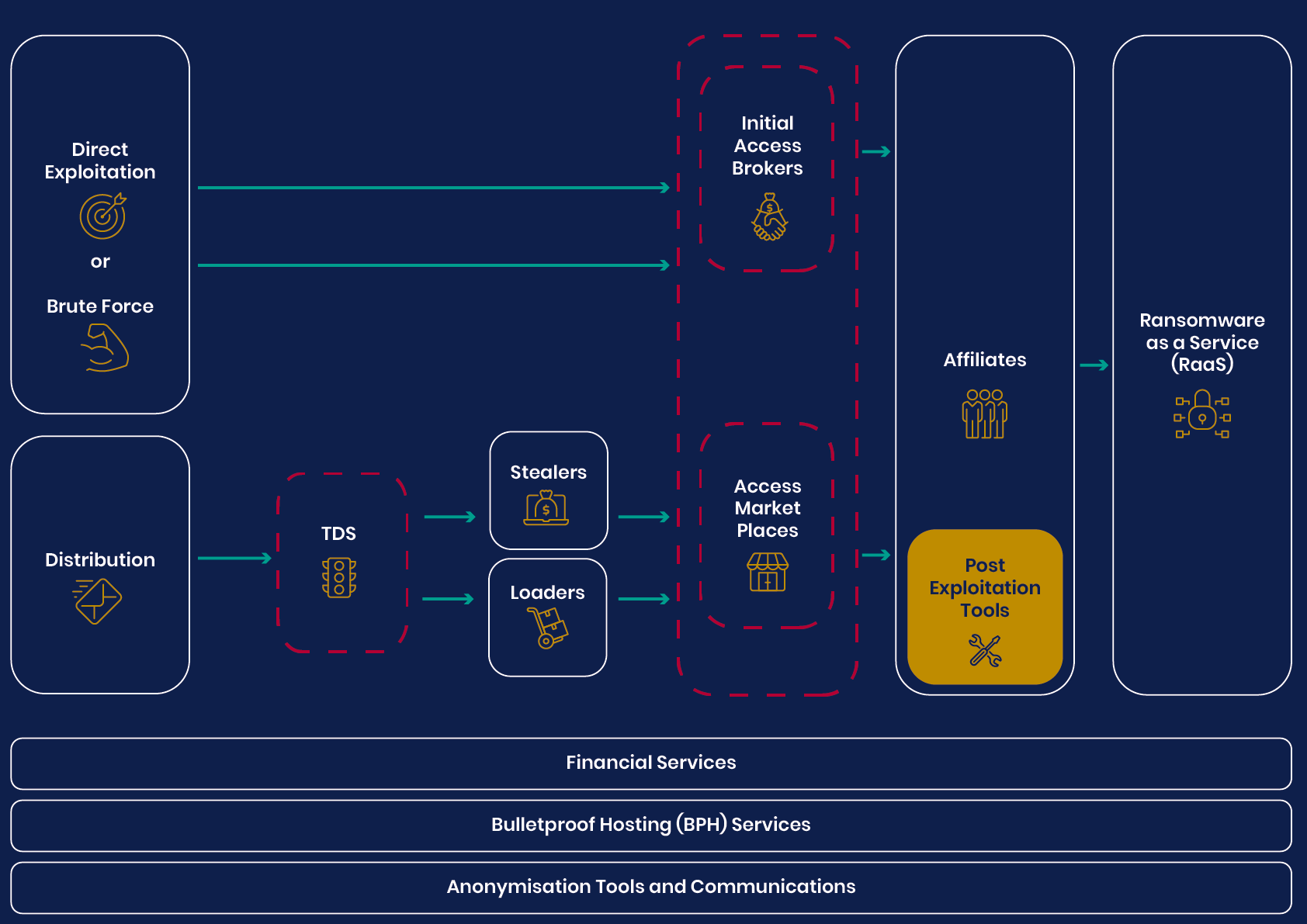 UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem
UK’s National Agencies Release White Paper on Evolving Cyber Crime Ecosystem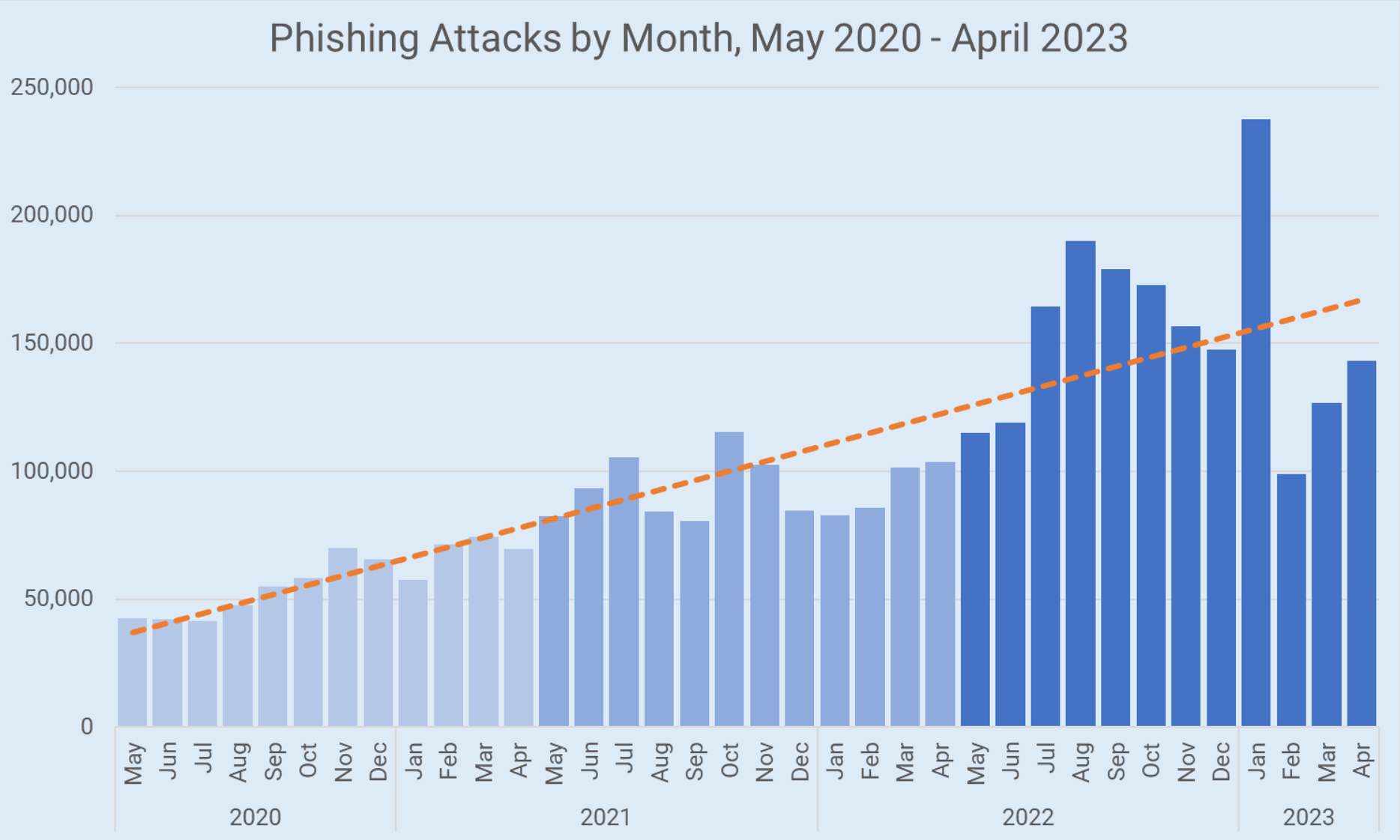 Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed
Phishing Attacks Surge Despite Increased Awareness, New Strategies Needed U.S. Schools Targeted in Ransomware Attacks: White House Responds
U.S. Schools Targeted in Ransomware Attacks: White House Responds British Researchers Discover AI-Powered Technique That Can Extract Data Through Typing Sounds
British Researchers Discover AI-Powered Technique That Can Extract Data Through Typing Sounds Widespread Cyberattack Paralyzes US Hospital Systems, Interrupting Critical Healthcare Services
Widespread Cyberattack Paralyzes US Hospital Systems, Interrupting Critical Healthcare ServicesAddressing DNS abuse and maintaining a healthy DNS ecosystem are important components of Verisign's commitment to being a responsible steward of the internet. We continuously engage with the Internet Corporation for Assigned Names and Numbers (ICANN) and other industry partners to help ensure the secure, stable and resilient operation of the DNS. more
Verisign just released its Q2 2018 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of customers of Verisign DDoS Protection Services. more
Currently scheduled for October 11, 2018, the Internet Corporation for Assigned Names and Numbers (ICANN) plans to change the cryptographic key that helps to secure the internet's Domain Name System (DNS) by performing a Root Zone Domain Name System Security Extensions (DNSSEC) key signing key (KSK) rollover. more
Verisign has released its Q1 2018 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of Verisign DDoS Protection Services, and security research conducted by Verisign Security Services. more
As DNS attacks grow in frequency and impact, organizations can no longer afford to overlook DNS security as part of their overall defense-in-depth strategy. As with IT security in general, no single tactic can address the entire DNS threat landscape or secure the complete DNS ecosystem. more
Verisign has released its Q4 2017 DDoS Trends Report, which represents a unique view into the attack trends unfolding online, through observations and insights derived from distributed denial of service (DDoS) attack mitigations enacted on behalf of Verisign DDoS Protection Services and security research conducted by Verisign Security Services. more
Cybercriminals recognize the value of DNS availability and look for ways to compromise DNS uptime and the DNS servers that support it. As such, DNS becomes an important point of security enforcement and a potential point in the Cyber Kill Chain for many cyber-attacks. more