

|
||
|
||
The release of a new application or operating system (OS) is typically greeted by enthusiasm, diverse opinions, and potential threats. Windows 11’s case is no different as we identified various assets that could be misused on the Internet. This post provides an overview of those found assets—domains and subdomains—as well as some data enrichment, including the identification of likely dangerous properties.
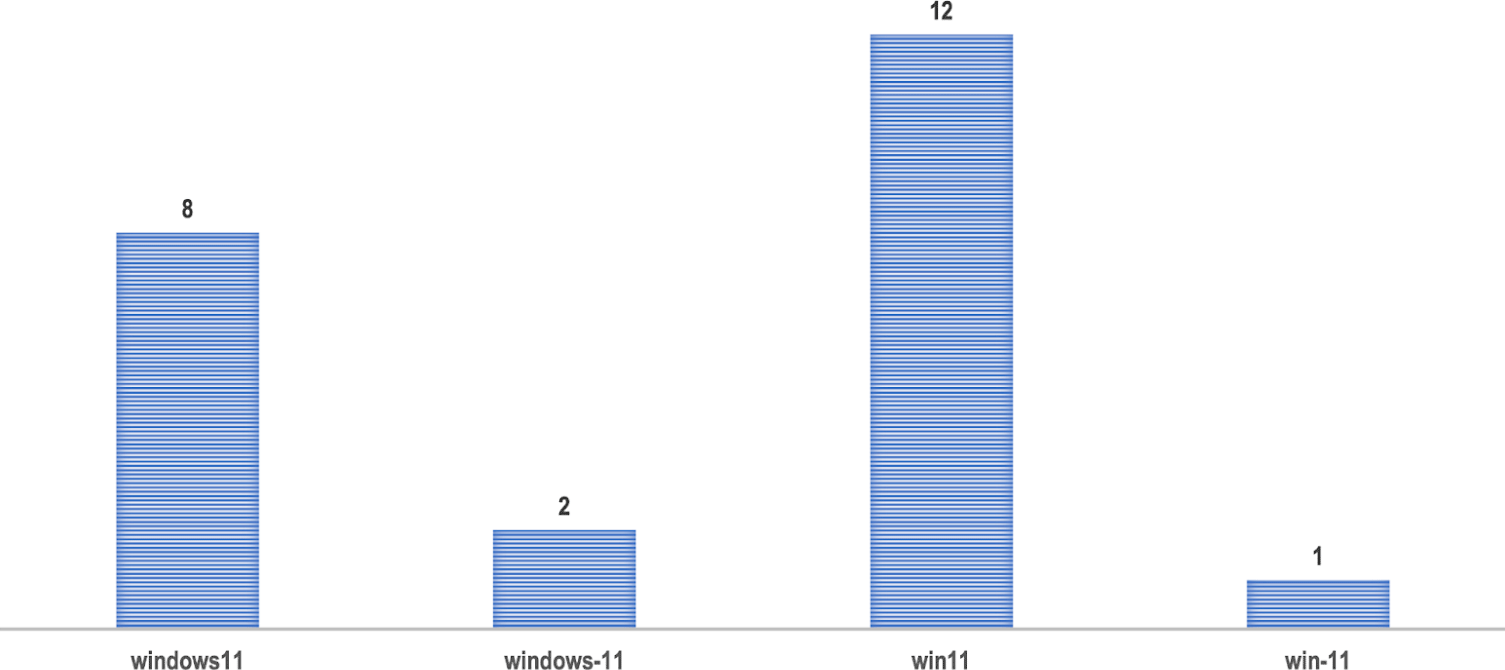
We looked at newly registered domain data feeds from 26 May to 26 June 2021 to see how many have the strings “windows11,” “windows-11,” “win11,” and “win-11” in them. Our rationale is that while some of these can have nonmalicious purposes, such as the launch of related products and services by various companies, others may have been registered for nefarious reasons, such as phishing.
For our analysis, we exclusively used the newly registered domains with the “.com” extension. From these, we obtained a sample containing 125 domain names, even though including other major TLDs in the analysis would have significantly increased our sample size.
The strings of those 125 domains were broken down into:

Five of the 125 domains were dubbed “malicious” when queried on our threat intelligence platform. Of these five flagged properties, examples that could easily figure into phishing campaigns are windows11activator[.]com and windows11appstore[.]com.
Windows11activator[.]com could, for instance, be used to lure in users in search of ways to get around activating their OSs without paying for licenses. Windows11appstore[.]com, meanwhile, could be used to trick users into giving out personally identifiable information (PII) or shelling out money to pay for apps for their new OS.
We used a subdomain finder to look for subdomains containing the strings “windows11,” “windows-11,” “win11,” and “win-11” that were added to the subdomain database since 26 May 2021.
A sampled total of 23 subdomains were found broken down by string into:
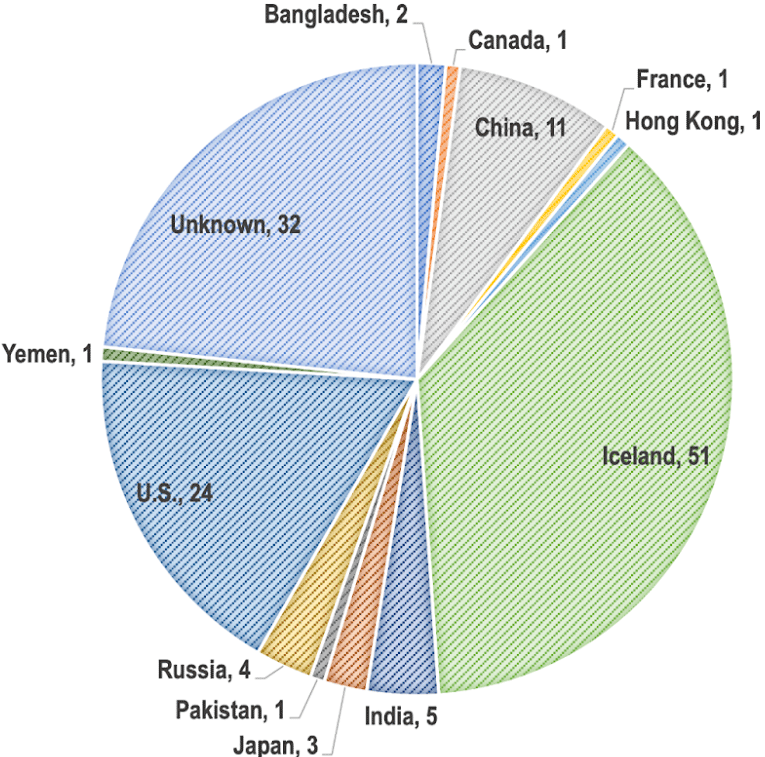
Combining the NRDs with the domains of the resulting subdomain searches gave us a list of 137 unique domains. None of them appeared to be owned by Microsoft based on the result of our bulk WHOIS lookup. They were also registered in 12 countries broken down into:
1% each were registered in Bangladesh, Canada, France, Hong Kong, Pakistan, and Yemen
Querying the domains on a DNS database provided us with a list of 92 unique IP addresses. Eleven of these were tagged “malicious” when run through a threat database.
Running them through a bulk IP geolocation tool revealed that a vast majority of them (75%) were geolocated in the U.S. They were scattered across 11 countries, namely, Australia, China, France, Germany, Hong Kong, Japan, the Netherlands, Singapore, Taiwan, the U.S., and Vietnam.

A comparison of the domain registrant and IP geolocation countries shows huge disparities. Only four countries—China, France, Hong Kong, Japan, and the U.S.—appeared in both charts.
To find more potential threat artifacts, the 11 malicious IP addresses were queried through a passive DNS database. Two important notes should, however, be kept in mind. First, the results of every passive DNS query are limited to 300 domains per IP address. And second, all duplicates were removed from the resulting list. That said, a total of 1,037 unique domains were collected. Since they resolved to a malicious IP address at least once, some of them could be dangerous to access as well. Examples include:
A few weeks away from the Windows 11 release, many domains containing related strings started being registered, some of which have already been flagged as suspicious or malicious. Other related subdomains have also started appearing to the DNS and may require closer attention.
If you wish to get a copy of the domains and subdomains we obtained for this Windows 11 study to enhance your security monitoring, don’t hesitate to contact us.
Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byDNIB.com

Sponsored byRadix

Sponsored byWhoisXML API

Sponsored byCSC
