
|
||
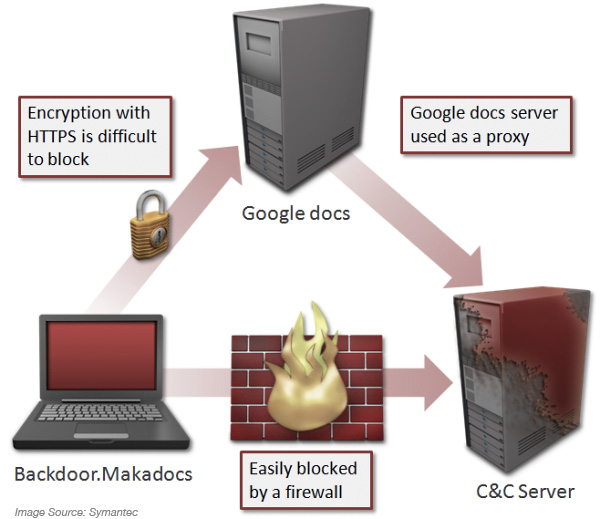
Security researchers have found a new variant of the Macadocs malware to be using Google docs as a proxy server and not connecting to a command and control (C&C) server directly. In a blog post on Friday, Symantec researcher Takashi Katsuki, wrote:
“Google docs has a function called viewer that retrieves the resources of another URL and displays it. Basically, this functionality allows a user to view a variety of file types in the browser. In violation of Google’s policies, Backdoor.Makadocs uses this function to access its C&C server. It is possible that the malware author has implemented this functionality in an attempt to prevent the direct connection to the C&C;from being discovered. The connection to the Google docs server is encrypted using HTTPS, thereby making it difficult to be blocked locally. It is possible for Google to prevent this connection by using a firewall. “
Sponsored byDNIB.com

Sponsored byRadix

Sponsored byCSC

Sponsored byVerisign

Sponsored byIPv4.Global

Sponsored byVerisign

Sponsored byWhoisXML API
